Shift-Left Security: A Proactive Approach to Modern Cybersecurity
Shift-Left Security is a proactive cybersecurity approach that integrates security measures early in the software development lifecycle, reducing vulnerabilities and enhancing protection.

Shift-Left Security: A Proactive Approach to Modern Cybersecurity
Table of Contents
In light of how rapidly the digital terrain is shifting, the significance of cybersecurity has reached the highest level. There is no doubt that cyber crimes are increasing in complexity and evolving to target businesses from every sector. Most traditional methodologies when it comes to security focus on resolving the risks after the deployment of the systems. This, however, is no longer the case. The advent of Shift-Left Security brings a decisive change – security is enforced at the earliest stages of the development cycle which guarantees that systems and applications are secure by design.
What is Shift-Left Security?
Shift-Left Security is a methodology developed to incorporate security measures early in the software development life cycle processes. The phrase “shift-left” means that the consideration of security in a software development project as a continuum begins with the planning stage, coding stage, and now the security stage. It is a common scenario to see Shift-Left Security as a risk management discipline executed at the latter phase of software development, as the solution processes all the phases; including design, development and testing.
This type of thinking is, however, in clear contrast with the traditional thinking where testing on security is done toward the completion of the development processes in most cases resulting in the development cycle being dragged, being costlier than anticipated and inevitable breaches being the order of the day.
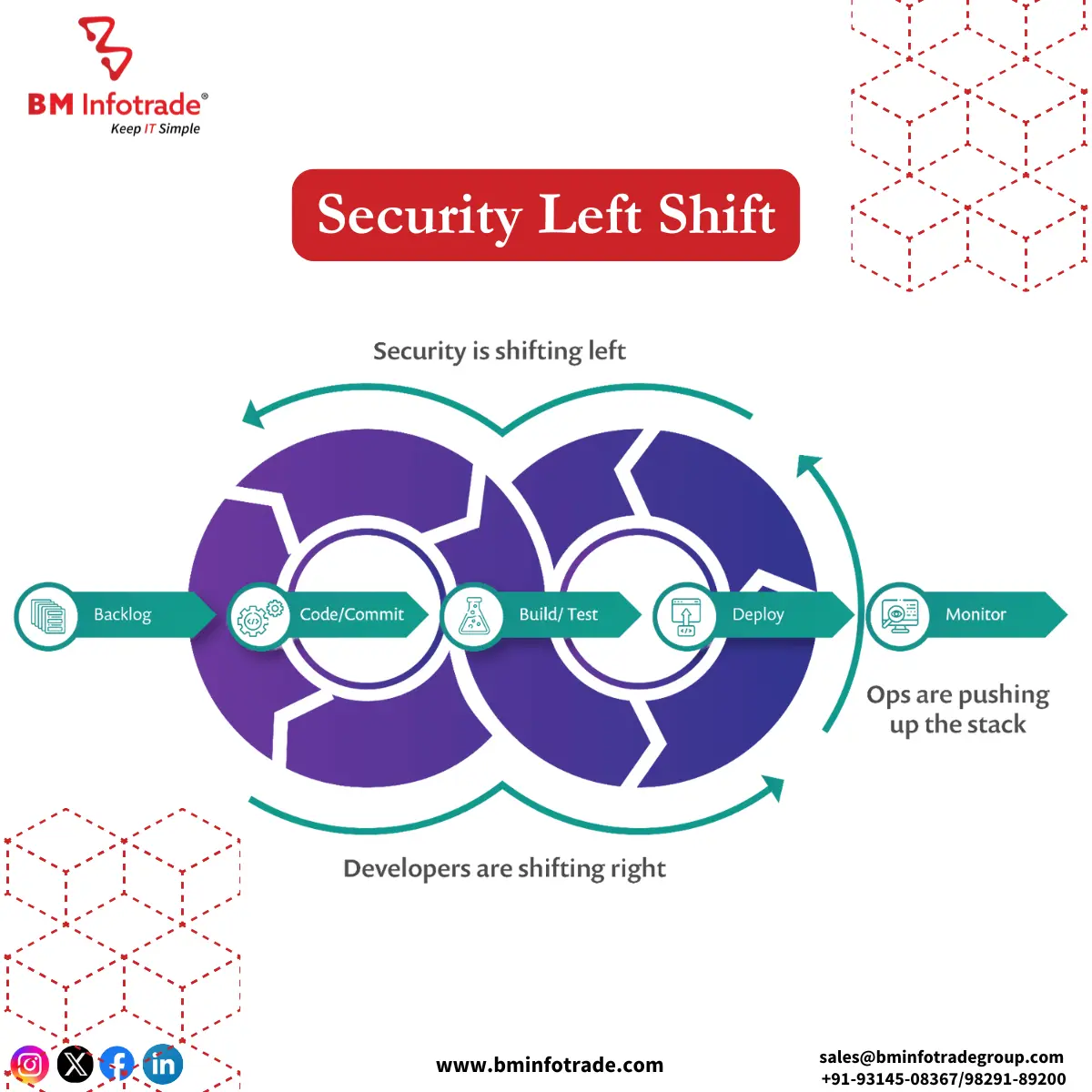
Early Integration of Security Measures
-
While coding, developers have tools and guidelines to deal with the vulnerabilities.
-
Security is not only the speciality of paid security professionals, but it is with the other teams as well.
Automation and Continuous Testing
-
Security testing tools are automatically integrated into the CI/CD pipelines for timely feedback.
-
Performing code reviews and penetration testing lowers the odds that the applications deployed will be inferior.
Collaboration Across Teams
-
Collaboration helps teams break down Development/Operations/Security silos.
-
Efforts to integrate development, operations, and security work transform mindsets to one of ownership across the function of the organization.
Security in the Form of Code
-
Policies and configurations related to security are considered as code which means they are versioned and are checkable.
-
Ensuring uniformity and reduction of human error is what this method promotes.
Benefits of Shift-Left Security
Cost Efficiency
-
The earlier security issues are dealt with in the life cycle of the system the lesser the cost required to rectify the weakness. There are studies that indicate the cost involved in fixing a bug reported after the system has been implemented is approximately 30 times that incurred if the bug was to be fixed during the design of the system.
Faster Time To Market
-
By dealing with security issues at the outset, security testing and remediation delays are avoided.
-
Consumers of applications are confident that applications are secure by design and can therefore be deployed without the usual apprehensiveness about the security of applications.
Improved Quality of Software
-
Integrating security into system development enhances the quality of the software, making it less prone to breaches, and strengthening the confidence of the users of the software.
Regulatory Compliance
-
Shift-Left Security enables organizations to be compliant with strict data protection legislation by making security considerations from the beginning.
Challenges in Implementing Shift-Left Security
Regardless of the various advantages, adopting Shift Left Security isn't free of difficulties:
Cultural Challenges
-
Development teams that have been following traditional processes may not be willing to extend their practices to include security.
-
Addressing this is straightforward – it requires a change of culture and adequate training.
Gaps in Skills
-
Developers may not have the requisite technical know-how in cybersecurity. Organizations have to commit resources towards reskilling their employees.
Tooling Complexity
-
There is a challenge in integrating and managing several security solutions into the existing pipelines.
-
It is important to choose the right tools and coordinate them with existing workflows.
Balancing Speed and Security
-
Security is viewed as a factor that inhibits development in most cases. Therefore, organizations need to ensure that both security and agility are present in equal measure.
Best Practices for Implementing Shift-Left Security
Empower Developers with Training: Conduct regular workshops and training sessions to enhance developers’ understanding of security best practices.
Adopt DevSecOps Practices: The phrase DevSecOps captures a cultural shift towards integrating security at every phase of development, which allows for adopting DevSecOps at scale across organizations. This can be done by enhancing every DevOps workflow time to deliver by including security as part of the process.
Use Advanced Security Tools: In particular, SAST (Static Application Security Testing), DAST (Dynamic Application Security Testing) and RASP (Runtime Application Self Protection) tools should be employed to be able to detect attacks early.
Encourage Collaboration: Security is everyone’s responsibility Therefore efforts should be made to improve communication between development, operations, and security in order to promote a shared responsibility culture.
Monitor and Iterate: Based on the feedback and the newly developing threats, stakeholders should be able to assess the security metrics and change organizational processes within the organization.
Real-World Applications of Shift-Left Security
The implementation of Shift-Left Security is proving to be advantageous to organizations in every sector. For instance:
-
Tech Giants: Google and Microsoft, for instance, embed security testing into their CI/CD processes such that vulnerabilities are identified and corrected before deployment.
-
Healthcare Sector: Healthcare organizations manage patient information, which is highly sensitive, hence there is the assimilating of Shift Left approaches to meet such requirements as HIPAA.
-
Financial Services: Financial institutions, including banks and fintechs, work on preventative security for the constant threats to the financial systems from advanced cyber attacks.
Why Shift-Left Security Matters Today
As applications grow in scale and dimension, and with the increase in cyber threats, there is an evident need for taking the bull by the horns. A change in perspective. A change in control. Traditional approaches are simply not fit for the ever-evolving landscape of threats of the present day. Shift-Left Security is not only about bringing about a risk reduction; it also helps embed security in a cultural shift that utilizes agile and DevOps practices and is therefore the lifeblood of any progressive cybersecurity strategy going forward.
Shift-Left Security is changing how companies think about and execute their cybersecurity approach. It makes sure every application is built with better security and at lower costs because security issues are handled early in the application lifecycle. Though there are some challenges, the overall long-term advantages will more than makeup for the upfront costs involved with implementing the shift left methodology.
In the face of changing and increasing cyber threats, organizations that adopt Shift-Left Security principles in their design process will be at the forefront in terms of protecting their digital assets and remaining competitive even in an ever more integrated ecosystem.






Anshul Goyal
Group BDM at B M Infotrade | 11+ years Experience | Business Consultancy | Providing solutions in Cyber Security, Data Analytics, Cloud Computing, Digitization, Data and AI | IT Sales Leader