Access Control in Cybersecurity: Definition, Types and Best Practices (2025)
Access control in the field of information security and physical security is a very important aspect. It’s a basic concept that allows only authorized individuals to access certain resources whether digital or physical.
Access Control in Cybersecurity: Definition, Types and Best Practices (2025)
Table of Contents
Access control in the field of information security and physical security is a very important aspect. It’s a basic concept that allows only authorized individuals to access certain resources whether digital or physical. Access controls are mechanisms used to protect confidential data, and physical rooms, and enable the right use of resources. This article will look into the meaning of access control, its significance, and different types of access control systems.
What is Access Control?
Access Control is a selective restriction of entry to premises or other resources. In this context, it means coming into contact with something by consuming it or entering it for example using it as intended. Access control systems refer to combinations of methods and technologies applied when managing who can gain access to particular resources under which conditions.
Importance of Access Control
In broader terms, access control ensures that only legitimate users can do specific things or have certain data accessed by them alone. This is essential in both physical security where buildings, rooms, or other spaces are controlled from being accessed by others and in cyber security where networks, data as well as systems may be accessed.
This results in:
-
Security: Guards against unauthorized penetration of sensitive information and assets.
-
Efficiency: Only the authorized staff can enter certain areas or view some data hence streamlining operations and lowering human error risks.
-
Audit & Accountability: Provides an audit trail for what was opened when which is indispensable for auditing purposes.
Types of Access Control
Access control can be categorized into various types, each with its methodologies and use cases. The main types of access control are:
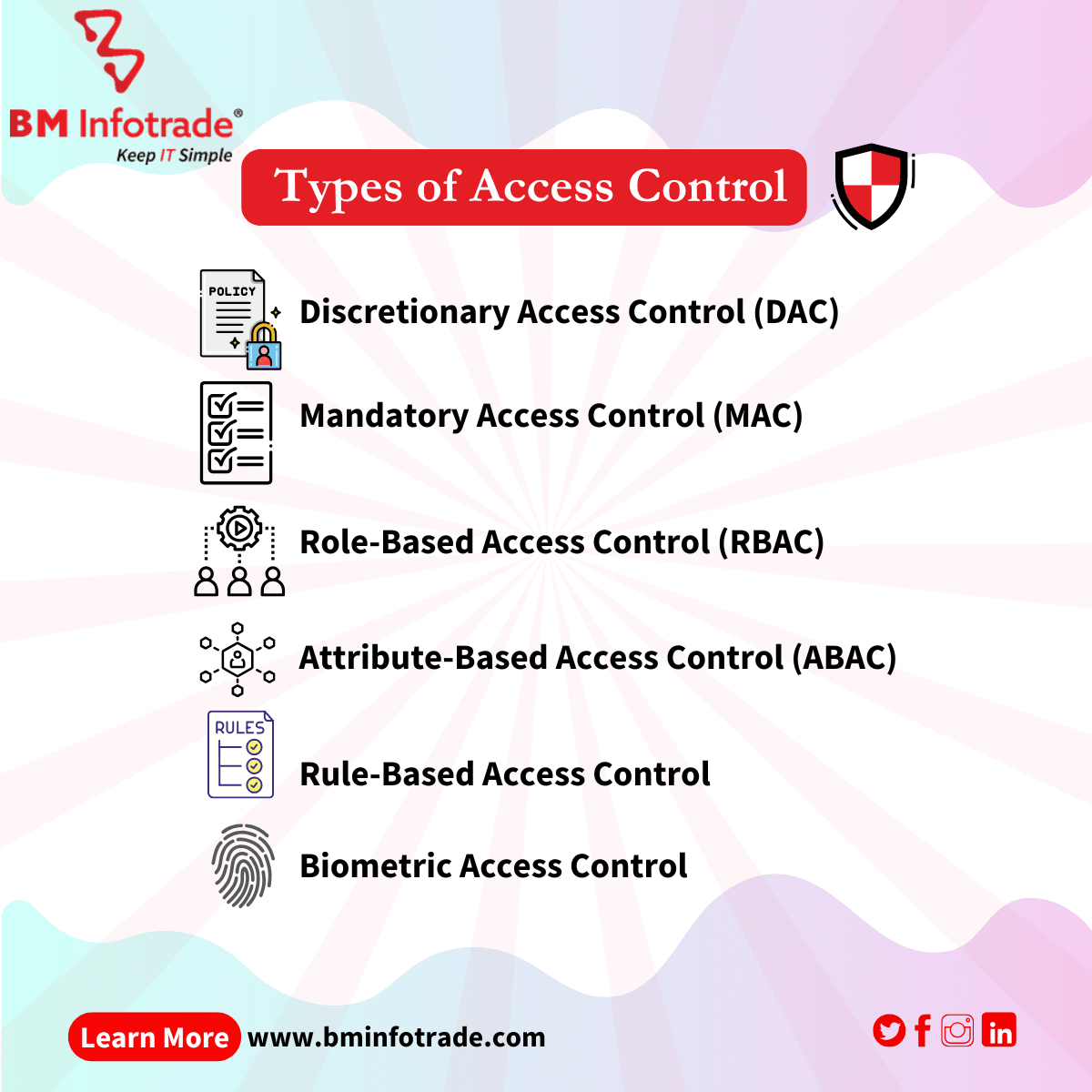
1. Discretionary Access Control (DAC)
Discretionary Access Control (DAC) refers to an access control system whereby either the owner/administrator (in case of resource protection) defines policies governing those allowed to access the resource while other users try getting in at their own risk according to him/her/it.
Features of DAC:
-
Flexibility: Can allow additional users
-
User-based: based on user identities
-
Common with File Systems: Usually found in file systems whereby users can give permission levels for their files and folders
Advantages:
-
Easy implementation and management
-
The high degree of flexibility available for the owner
Disadvantages:
-
Less secure since it depends on the user’s discretion
-
If permission is wrongly assigned, then security breaches can occur
2. Mandatory Access Control (MAC)
Mandatory Access Control (MAC) is a more stringent type of access control model where access rights are regulated by a central authority based on multiple levels of security. It does not allow users to selectively choose or change an object’s policy rather these policies are enforced at the system level.
Features of MAC:
High Security – Enforced strict centrally made policies.
Classification Levels – Different levels of sensitivity such as confidential, secret, and top secret determine access rights.
Advantages:
-
High level of security provision.
-
Centralized control minimizes incidents of hacking.
Disadvantages:
-
Not as flexible as DAC.
-
May be hard to manage and implement.
3. Role-Based Access Control (RBAC)
Role-Based Access Control (RBAC) is an access control mechanism that assigns permission based on the roles within an organization. Instead of assigning permissions to individual users, it assigns them to different roles, and users are assigned to these roles based on their responsibilities.
Features of RBAC:
-
Role-based: Access is based on roles rather than individual users.
-
Scalability: As roles change within the organization, it becomes easier to manage.
Advantages:
-
Simplifies management of permissions.
-
Easy audit and enforcement of access policies.
Disadvantages:
-
Role explosion: In large organizations, there can be numerous roles that make management complex.
-
Inflexibility: It may not easily accommodate the specific access needs of individuals.
4. Attribute-Based Access Control (ABAC)
Attribute-based access Control (ABAC) is a model that provides access based on attributes such as user attributes, resource attributes, and environmental attributes. Compared to RBAC, ABAC allows for a more granular level of access control
Features of ABAC:
-
Dynamic and Contextual: Multiple attributes can be considered when making decisions about granting access.
-
Granularity: Fine-grained access control is provided by this model.
Advantages:
-
Highly flexible and adaptable to various scenarios.
-
Supports complex and dynamic access requirements.
Disadvantages:
-
Can be complex to implement and manage.
-
Requires comprehensive attribute management.
5. Rule-Based Access Control
Access policies are applied by Rule-Based Access Control through a set of rules defined by system administrators. These rules specify conditions under which access is granted or denied.
Features of Rule-Based Access Control :
-
Rule-based: Administrators configure rules that determine access rights.
-
Dynamic: Changes in rules are possible whenever necessary.
Advantages:
-
Provision of clear-cut concise policy statements concerning accessibility issues.
-
Flexible enough to meet all situations.
Disadvantages:
-
Complexity increases with more numbers or rules being in place.
-
Rules must be thoroughly understood because they need constant management.
6. Biometric Access Control
Biometric Access Control is a system that uses biological attributes to identify and make access decisions. Some commonly used biometric identifiers include fingerprints, facial recognition, retina scans, and voice recognition.
Features of Biometric Access Control:
-
Unique Identification: Characteristics are unique to an individual only
-
Non-transferable: This means that one person cannot lend his/her access rights to another person
Advantages:
-
High level of security due to unique identifiers.
-
Difficult to forge or replicate.
Disadvantages:
-
Privacy concerns with biometric data storage.
-
Can be expensive to implement.
Implementing Access Control Systems
Implementation of an effective access control system requires meticulous planning and consideration of the specific needs of the organization. These are some steps that can help in implementing access control systems:
-
Assess Needs: Identify what resources need protection and the level of security required.
-
Choose Right Type: Determine which type of access control is appropriate for the organization.
-
Develop Policies: Create clear access control policies that define who has access to what resources.
-
Implement Technology: Deploy necessary hardware and software for enforcing access control policies.
-
Monitor and Audit: Continuously review log files to see If there is any breach into your system by unauthorized persons.
Review and Update Periodically reshape your approach toward controlling traffic in terms of changes in both threats as well as organizational requirements”
Access control is a key part of physical as well as digital security, providing a way to protect valuable assets from unauthorized intrusions. Understanding Different Types Of Access Control Systems (Discretionary, Mandatory, Role-Based, Attribute-Based, Rule-Based, And Biometric) helps organizations Choose The Appropriate Approach That Matches Their Security Needs. By employing strong mechanisms that enforce these rules organizations can protect their assets, ensure compliance, and improve efficiency in operations.




![Cloud Licensing and Compliance Made Easy [All-in-One Bundle]](https://bminfotrade.com/assets/upload/blog/21851766642757.png)

Anshul Goyal
Group BDM at B M Infotrade | 11+ years Experience | Business Consultancy | Providing solutions in Cyber Security, Data Analytics, Cloud Computing, Digitization, Data and AI | IT Sales Leader