Cyber Mitigates Threats- Lock it down, protect it up.
This blog explores effective strategies to mitigate cyber threats by securing systems and protecting sensitive data. Discover practical tips to enhance your cybersecurity.

Cyber Mitigates Threats- Lock it down, protect it up.
Table of Contents
As more cybercriminals turn to methods that can successfully evade detection and make it simple to target high-value targets, there has been a noticeable increase in threat volume and sophistication in recent years. Threat actors are increasingly focusing on IoT devices, and the prevalence of ransomware and threats involving the theft of credentials is also rising. Furthermore, some cybercriminals are relocating their infrastructure to the cloud in an effort to blend in with reputable services.
All of these trends indicate that your organization must have a successful strategy for reducing cyber security risks if you don't want to put it at risk of being left behind by the constantly changing threats from the threat landscape of today. Here are eight crucial tactics for enhancing security and reducing the impact of successful attacks, including using a risk assessment tool.
Businesses can now more effectively reach their target audiences, streamline processes, gather and analyze data, and do other things thanks to evolving technologies. However, the risk of being targeted by cybercriminals and other threat actors is also rising as organizations continue to prioritize digital transformation. According to the Internet Crime Report 2021 published by the Federal Bureau of Investigation, the US could have lost more than $6.9 billion due to cybercrimes over the previous year. Successful organizations place a high priority on threat mitigation to combat these risks to their operations and clients.

Read More: 5 Essential Cybersecurity Facts!
Start Threat Mitigation Today
No company is completely safe from the threat of a cyber-attack in this era of unrestricted connectivity and digital communication technologies. An effective security profile must include threat mitigation because it gives companies the methods and tools they need to recognize, address, and eliminate network threats. In order to ensure that the appropriate security solutions and systems are in place, Acrisure Cyber Security services connect organizations with the appropriate people. These services offer resources and support for business across all industries. We can guide you toward efficient threat identification and mitigation. Additionally, Acrisure Cybersecurity Insurance safeguards your company and covers your liability in the event of a data breach, ensuring that your business can continue to operate.
Cyber security risks and mitigation?
The process of reducing the overall risk or impact of a cybersecurity threat involves the use of security policies and procedures. Risk mitigation in the context of cybersecurity can be divided into three categories: prevention, detection, and remediation. Your organization's cybersecurity risk mitigation strategies will need to evolve to keep a competitive edge as cybercriminals' tactics become more sophisticated.
The tools, procedures, and methods businesses employ to lessen the severity or seriousness of a potential data breach or other cyberattack are referred to as threat mitigation (also known as cyber risk mitigation or cyber-attack mitigation).
Threat Mitigation: What Is It?
The term "threat mitigation" (also known as "cyber risk mitigation" or "cyber-attack mitigation") refers to the methods, procedures, and tactics employed by businesses to lessen the severity or impact of a potential data breach or other cyber-attack. As a result, threat mitigation can be divided into three main components or methods:
Prevention
Threat prevention techniques aim to lessen the possibility of a successful cyberattack by locating and fixing any system security flaws. Instead of reacting to incidents after they have already happened, prevention focuses on thwarting threats before they can be carried out.
Detection
The process of keeping an eye on a company's security ecosystem in order to spot any malicious activity taking place on its networks is known as threat detection. To give the organization the ability to react swiftly and forcefully when suspicious activity is discovered, detection must be combined with other mitigation measures.
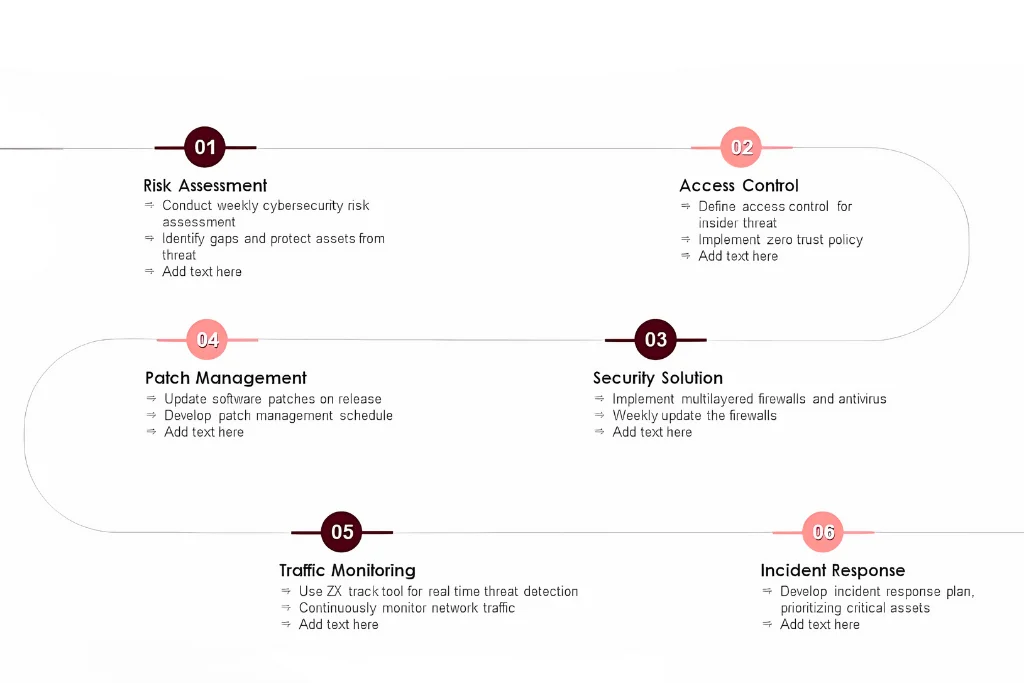
Remediation
Threat remediation addresses threats that have been discovered, correcting or lessening the threat's impact, and eradicating it from the system. As a threat response, remediation entails techniques for containing and limiting network damage.
Risk evaluation
Creating a clear picture of the organization's network, assets, and controls is the first step in any threat mitigation strategy. This picture should also include any known security vulnerabilities, the likelihood that they will be exploited, and the potential impact they could have on the company. A threat mitigation plan can be built roughly on the basis of a list of these potential vulnerabilities and the threat vectors that could be used to exploit them.
Using the appropriate security
Due to the wide variety of contemporary threat vectors, network security solutions also need to be equally varied. A variety of security measures, such as the following, will likely be necessary to establish a comprehensive security profile:
Endpoint Security
Endpoints, or end-user gadgets like laptops, desktop computers, mobile phones, tablets, servers, virtual computing environments, and internet of things (IoT) gadgets, frequently stand in for the most open attack points in the IT world. It can be extremely difficult to fully account for every network endpoint in an organization given the growing risks posed by shadow IT. It is advised that IT departments instead put a strong emphasis on efficient access protocols and employee training. IoT devices and other non-standard endpoints should have their firmware analyzed for any potential flaws that might go unnoticed.
Software for firewalls and antivirus
For modern businesses, firewalls and antivirus software are two essential types of network security. In order to prevent unauthorized network access, firewalls filter incoming data according to predetermined criteria, scan samples of data as they pass through the system, and compare the results to a database of known threats. The file is where antivirus software operates.
Threat identification
Businesses cannot simply respond to threats as they materialize, given the high stakes involved in cyber security. Threat detection adopts a more aggressive stance, actively seeking out threats and inspecting the devices, networks, and applications of a company for any potential flaws. IT teams can address potential security gaps without having to wait for threat actors to take the initiative by keeping an eye on network traffic and usage. Advanced security tools are available to provide real-time monitoring capabilities, allowing security personnel to quickly examine enormous amounts of data flowing through the network.
Read More: How cyber security works and the cost of cyber security.
Conclusion
These threats typically refer to a malicious attempt to either steal data or harm or disrupt assets by gaining unauthorized access to systems, networks, or resources. Businesses frequently use methods collectively known as "cyber threat analysis" to spot, address, and get ready for potential threats.




![Cloud Licensing and Compliance Made Easy [All-in-One Bundle]](https://bminfotrade.com/assets/upload/blog/21851766642757.png)

Anshul Goyal
Group BDM at B M Infotrade | 11+ years Experience | Business Consultancy | Providing solutions in Cyber Security, Data Analytics, Cloud Computing, Digitization, Data and AI | IT Sales Leader