SAP Cyber Security: Protecting Your Enterprise Systems from Modern Threats
SAP Cyber Security: Protecting Your Enterprise Systems offers insights into securing SAP systems against modern threats, focusing on vulnerabilities, best practices, and tools to ensure data safety and compliance.

SAP Cyber Security: Protecting Your Enterprise Systems from Modern Threats
Table of Contents
With the use of SAP systems in managing various enterprise operations, there is a need for organizations to consider SAP Cyber Security as a vital component. Thus, amidst increasing cyber threats and data breaches, protecting your SAP environment is very important. On this note, this article will discuss about why you should not underestimate the importance of SAP cyber security, popular vulnerabilities and best practices to shield your business systems.
Understanding SAP Cyber Security
SAP (Systems, Applications and Products) is a renowned ERP (Enterprise Resource Planning) software that companies around the world use for their operations, such as finance, human resource management, logistics and supply chain management. However, due to the sensitive nature of data handled by these systems, they are also susceptible to cyberattacks.
The term “SAP Cyber Security” can be defined as the set of procedures and methods aimed at protecting against unauthorized access to SAP Systems as well as data breaches among other forms of cyber threats. These steps guarantee confidentiality, integrity and availability of information stored or processed within these environments.
Common Vulnerabilities in SAP Systems
Beware! Although solidly built with many functionalities; it does not make them invincible against attacks. Understanding common weaknesses would be crucial when it comes to securing your own SAP environment.
-
Unpatched Systems: As with any software package, patches are released regularly by SAP for remediation purposes. Yet several organizations tend not to apply these patches making their systems vulnerable to probable attacks.
-
Weak Access Controls: Poor access controls may result in unauthorized penetration into private data. This can include poor password policies lack of two-factor authentication (2FA), and insufficient user role management among others.
-
Lack of Encryption: Data transmitted via networks between different components may be intercepted by criminals if no strong measures like encryption are put in place thus causing data breaches.
-
Insecure Custom Code: When custom-developed codes are implemented without proper review or testing processes within its framework they end up bringing vulnerabilities into an organization.
-
Outdated SAP Security Configurations: Failure to update security configurations in line with the latest SAP recommendations can leave systems vulnerable to attacks.
The Importance of SAP Cyber Security
This makes it clear why ignoring the significance of SAP Cyber Security could be detrimental. There are major consequences that come with a breach in an SAP system ranging from loss of money to defamation and lawsuits. As businesses continue on the path towards digital transformation, they become increasingly susceptible to cyber threats; as such, strong cyber security measures have never been more important.
Key reasons why SAP cyber security is essential include:
-
Protection of Sensitive Data: Financial records, information about employees and customer details are some highly confidential data stored by most SAP systems. Thus, securing this information is very vital for retaining trust and compliance with legislations like GDPR and HIPAA.
-
Ensuring Business Continuity: Cyber-attacks may disrupt business operations causing downtime and financial losses. This means that effective measures should be taken into consideration by all organizations to protect their environments against these incidents.
-
Compliance with Industry Regulations: A lot of industries have strict regulations regarding the protection of data. Strong practices for safeguarding against cyber-attacks enable companies to follow these regulations without fines or any other penalties being imposed.
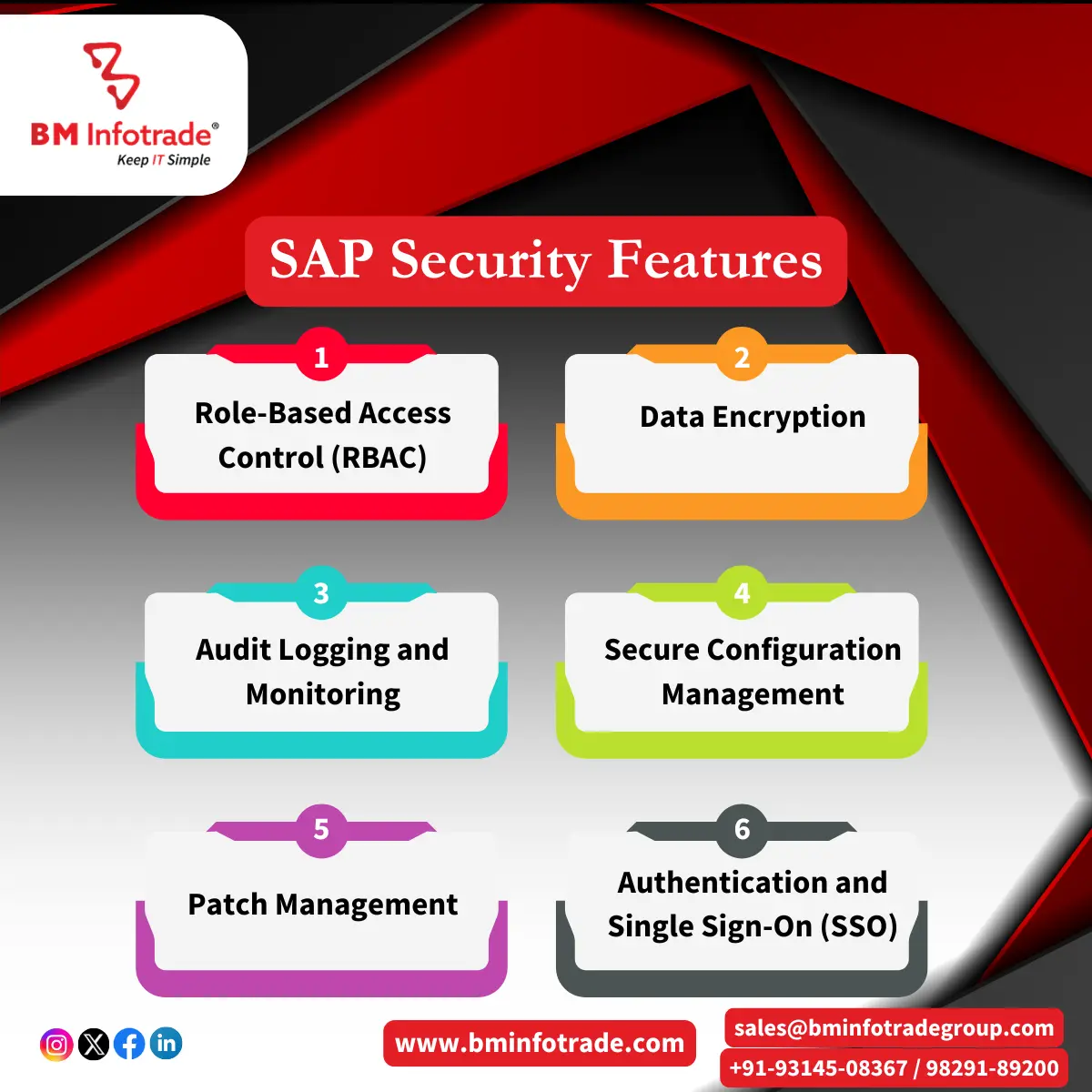
Best Practices for SAP Cyber Security
To adequately protect your own organization’s system from modern-day threats one has to take an all-encompassing approach towards SAP cyber security. Some of the best practices which can be considered include:
Regularly Update and Patching Your Systems
Keeping your enterprise’s systems updated is vital since the regular application of released security patches supports known vulnerabilities thereby reducing the prospects for exploitation.
Implement Strong Access Controls
Enforce strict access controls by using strong, complex passwords and implementing two-factor authentication (2FA). Additionally, ensure that user roles and permissions are carefully managed to minimize the risk of unauthorized access.
Encrypt Sensitive Data
To prevent interception or unauthorized access, encrypt data at rest and in transit for the protection of sensitive information. SAP has various encryption options that can be customized to meet the needs of your organization.
Conduct Regular Security Audits
The goal of regular security audits is to pinpoint possible vulnerabilities within the SAP environment. Such audits should consider custom code review, security configuration review and user access controls.
Utilize SAP Security Solutions
These include solutions like SAP Identity Management and SAP Enterprise Threat Detection which can help organizations detect, monitor and respond to threats immediately as they happen.
Educate and Train Employees
Many security breaches are due to human error such as not recognizing phishing attacks or weak password selection among others, therefore employees must be trained on best practices related to SAP system security so that risks can be minimized.
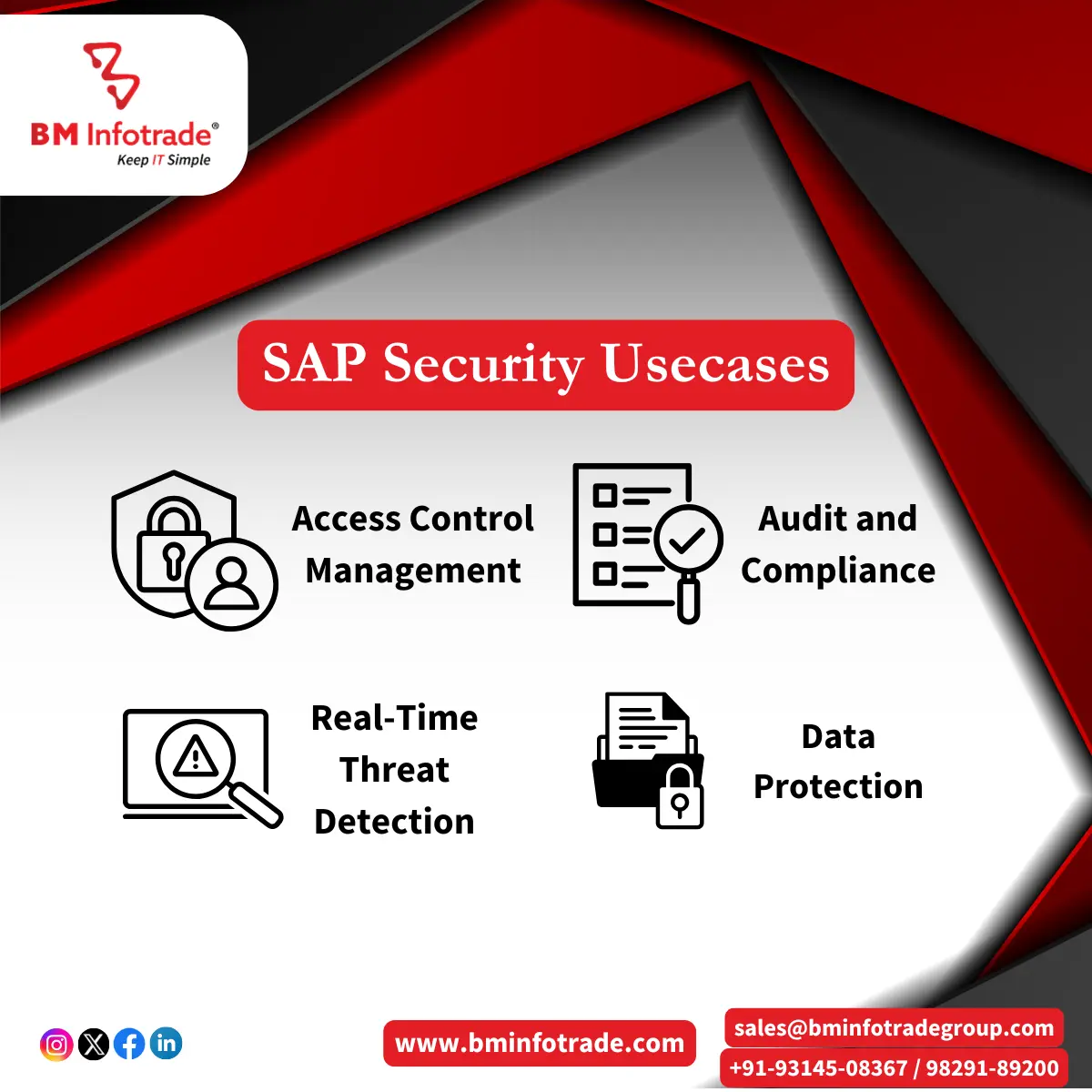
The Role of Continuous Monitoring in SAP Cyber Security
It may consist of real-time monitoring of system activity for potential threats and responses in the form of continuous monitoring; this is an essential aspect of cyber security for Sap systems worldwide. Implementing continuous monitoring allows organizations to:
-
Identify Unusual Activities: Organizations can quickly identify any suspicious or odd activity by tracking system activities.
-
Respond to Threats in Real-Time: Continuous monitoring makes it possible for organizations to respond as threats occur thereby reducing the potential impact from a breach.
-
Maintain Compliance: Sustainable compliance through visibility into the effectiveness of security controls is facilitated by continuous monitoring.
Conclusion
In summary, SAP cyber-security forms a major component within the broader organizational safety strategy. As businesses advance upon evolving cyber threats, they must move towards proactive measures aimed at safeguarding their SAP systems. Through the implementation of these recommendations set out in this blog post firms stand a chance to reduce cyber-attacks hence protecting sensitive information. Investing in SAP cyber security not only protects your enterprise systems but also ensures business continuity and compliance with industry regulations. Stay ahead of cyber threats and protect your SAP environment with robust security measures.




![Cloud Licensing and Compliance Made Easy [All-in-One Bundle]](https://bminfotrade.com/assets/upload/blog/21851766642757.png)

Anshul Goyal
Group BDM at B M Infotrade | 11+ years Experience | Business Consultancy | Providing solutions in Cyber Security, Data Analytics, Cloud Computing, Digitization, Data and AI | IT Sales Leader