Top SIEM Tools for Enhanced Security: Features, Comparisons, and Best Practices
Security Information and Event Management (SIEM) tools are now considered indispensable in contemporary cyber defense.

Top SIEM Tools for Enhanced Security: Features, Comparisons, and Best Practices
Table of Contents
In a world that depends on the web, cybersecurity is essential and needful for protecting confidential information as well as maintaining the integrity of systems and networks. Security Information and Event Management (SIEM) tools are now considered indispensable in contemporary cyber defense. They collect, analyze and manage security data from various sources in real-time, helping organizations detect threats proactively and respond to incidents.
Through this article, we intend to explore the field of SIEM solutions with a focus on the dominant tools available in the market today. It will help readers make informed decisions when it comes to their security infrastructure through exploring characteristics, making comparisons and discussing best practices.
They provide a centralized platform for monitoring and correlating security events, logs, and data from diverse sources such as network devices, servers, applications, and endpoints. This encompasses all parts of an organization; thereby allowing them to monitor abnormalities in behavior of users or even detect potential vulnerabilities before they are exploited by hackers.
SIEM Defined
Security Information and Event Management (SIEM) is a holistic approach to cyber security that combines Security Information Management (SIM) and Security Event Monitoring (SEM) functions into one solution. SIEM software gathers, aggregates, and evaluates data from various sources in an organization’s IT infrastructure such as network devices, servers, applications, endpoints and other sources of logs.
The main aim of SIEM is to offer timely awareness into occurrences or happenings related to security in order for an institution to effectively respond to threats faster. This involves the following core functionalities of SIEM platforms:
Log Collection: They are responsible for collecting log information from different systems within its setup. Logs come from firewalls’ records, intrusion detection system (IDS), antivirus programs among others.
Correlation and Analysis: After log data gets collected, it undergoes correlation by the system so as patterns can be identified which may suggest a possible security incident occurring thereby enabling rules to be applied which will enable this differentiation made between typical behaviour ad abnormality hence flagging any suspicious activities that can enhance further scrutiny on them.
ALERTING AND NOTIFICATION
SIEM tools generate alerts and notifications to security teams when there is a potential security threat. These alerts usually provide information about the occurrence, its seriousness, and what should be done to correct the situation.
INCIDENT RESPONSE
Incident response is facilitated by SIEM solutions as they contain workflows and playbooks that can be used for responding to a security incident. This includes automated response actions like blocking malicious IP addresses or isolating compromised endpoints.
Read More:- Key Cybersecurity Interview Questions in 2024
CRITERIA FOR EVALUATING SIEM TOOLS
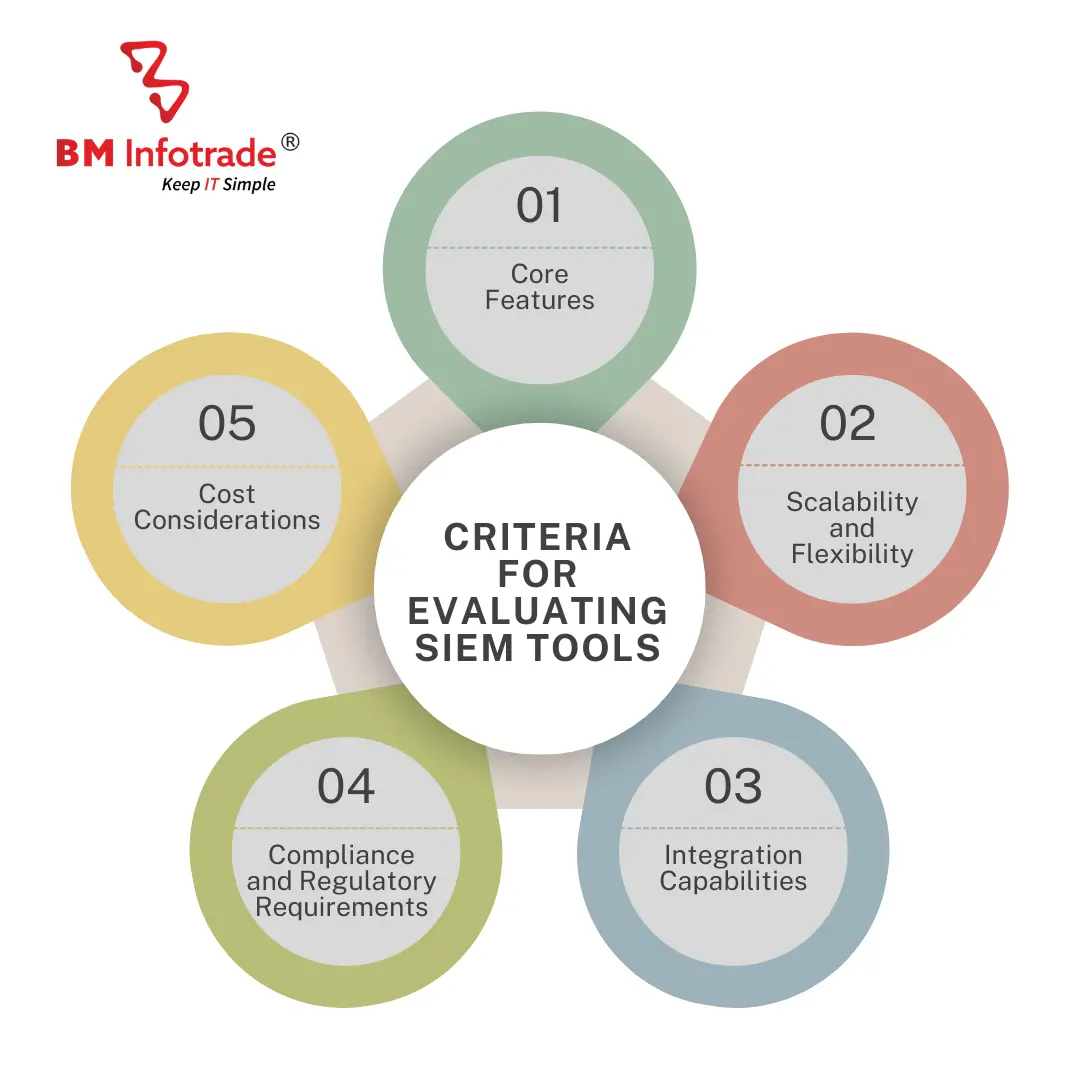
The right Security Information and Event Management (SIEM) tool should be chosen to support effective cybersecurity operations. When evaluating SIEM solutions, organizations must take into account several key factors in order to make an informed decision:
Core Features: Such core features include log collection, event correlation, real-time monitoring, alerting and incident response capabilities offered by SIEM tools. Ensure that the platform used aligns with your organization’s unique security requirements and goals.
Scalability and Flexibility: Consider scalability and flexibility of the chosen SIEM solution for accommodating your present organization needs as well as future ones. Among these considerations are data volume, number of devices, growth projections etc.
Integration Capabilities: Assess the SIEM system’s integration capabilities with other security tools and technologies currently in use in your IT infrastructure. Coordination between firewalls, endpoint protection software, threat intelligence feeds and other security products are important to ensure that you get the most out of your cyber security infrastructure.
Compliance and Regulatory Requirements: Make sure that the SIEM tool is compliant with industry standards such as GDPR, HIPAA, PCI DSS etc. Search for functions allowing compliance reporting, audit trails as well as privacy demands in data to prevent possible legal fines and penalties.
Cost Considerations: Evaluate total cost of ownership (TCO) of a SIEM solution including upfront licensing costs, implementation expenses, maintenance fees and continued operational costs. Consider elements like pricing models, support options and Return on Investment (ROI) to ascertain whether a SIEM solution is cost-effective over time.
Top SIEM Tools List
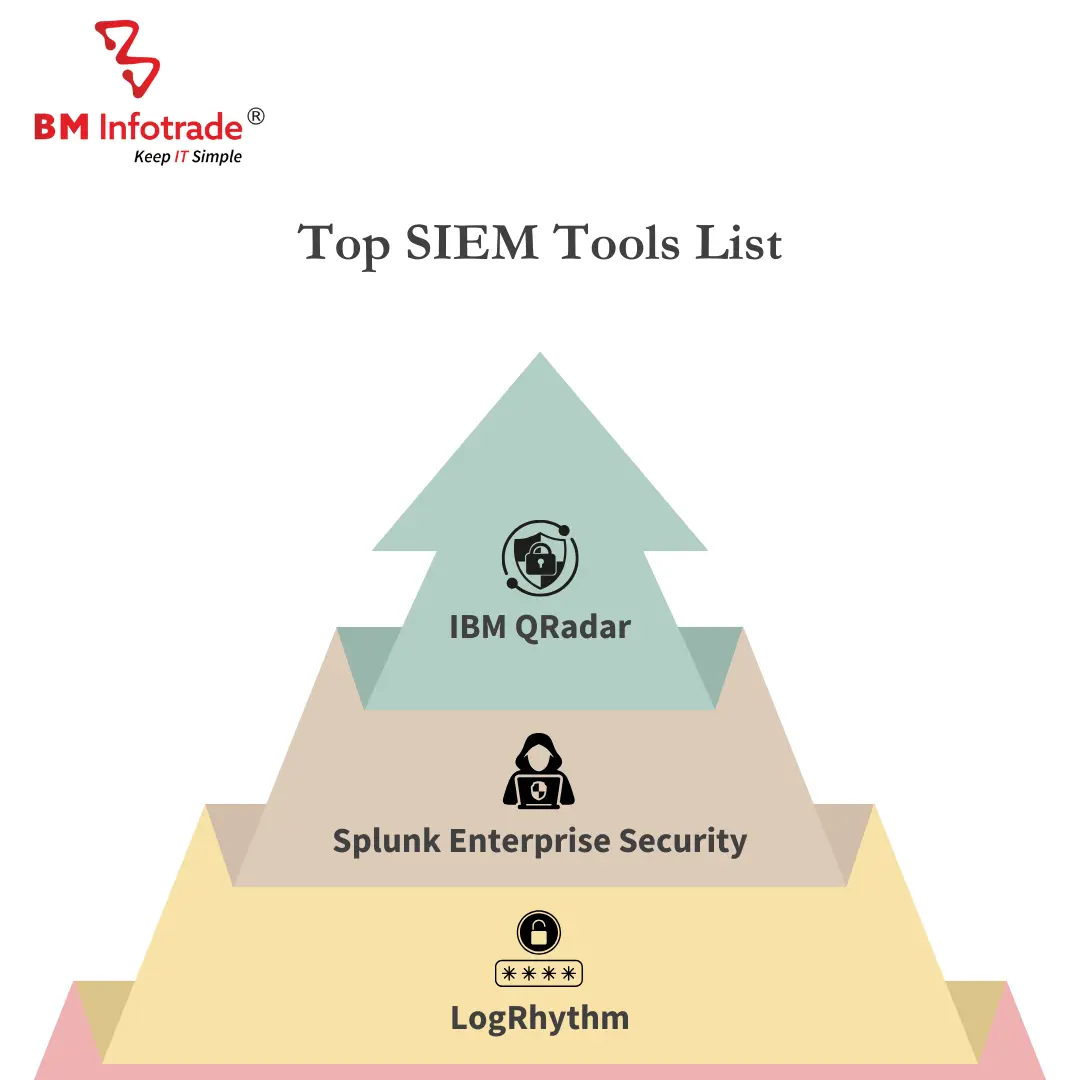
In today’s ever-changing world of cybersecurity there are several Security Information and Event Management (SIEM) tools that possess strong features for robustness, reliability and effectiveness. Here we’re going to delve into three of the topmost available SIEM tools on the market:
Splunk Enterprise Security: Splunk is famous for its strong analytic abilities and an interface that is easy to use. Splunk Enterprise Security provides sophisticated functionalities for real-time monitoring, threat hunting and incident response. Modularity in this case offers a platform that can be easily customized and integrated into already established security infrastructure. On the other hand, the wide range of apps and add-ons within splunk provide flexibility in meeting diverse protective requirements.
IBM QRadar: IBM QRadar is a scalable SIEM solution with excellent threat intelligence capabilities. In order to identify and prioritize security incidents, QRadar has advanced analytics, correlation and anomaly detection features. Enhancing such detection capability is QRadar’s built-in integration with IBM X-Force Threat Intelligence which allows proactive threatening hunting. This means that the dashboards are customizable while allowing for actionable insights into emerging threats.
LogRhythm: LogRhythm takes a unified platform approach combining SIEM, log management, as well as security analysis capabilities. Additionally, LogRhythm’s AI Engine uses machine learning algorithms to detect advanced threats in real-time. Furthermore, Its SmartResponse automation enables orchestration of all critical activities
It integrates with SmartResponse that automates the response actions, streamlining security operations. LogRhythm’s Threat Lifecycle Management (TLM) framework provides a coherent way of managing security incidents from their detection to resolution thus enhancing the overall state of cyber security.
Read More:- 5 Essential Cybersecurity Facts!
Conclusion
For contemporary dynamic cybersecurity landscape, Security Information and Event Management (SIEM) tools play crucial role in defending against evolving threats and protecting sensitive data. By examining leading SIEM solutions, their functionalities, comparisons, and industry best practices, organizations can enhance their defensive positions against all forms of threats.
To choose an appropriate SIEM tool requires considering key features like scalability integration capabilities; compliance adherence; cost effectiveness. The use of advanced SIEM platforms such as IBM QRadar, Splunk Enterprise Security or LogRhythm can improve the effectiveness of threat detection systems in organizations as well as incident response mechanisms and general cybersecurity resilience.
In relation to ever advancing cyber threats, being well versed with new trends is fundamental in SIEM technology. This will enable organizations to mitigate risks through adoption of best practices such as having strong SIEM solutions and promoting a culture of cybersecurity awareness and training for individuals within the organization.







Anshul Goyal
Group BDM at B M Infotrade | 11+ years Experience | Business Consultancy | Providing solutions in Cyber Security, Data Analytics, Cloud Computing, Digitization, Data and AI | IT Sales Leader