The Role of SOC Experts in Enhancing Organizational Security
Explore the critical role of SOC experts in strengthening organizational security through effective monitoring, threat detection, and incident management.

The Role of SOC Experts in Enhancing Organizational Security
Table of Contents
In today's fast-changing digital world, protecting organisational assets and data is crucial. As cyber attacks become more sophisticated and frequent, organisations need a strong Security Operations Center (SOC) to improve security. Monitoring, identifying, responding to, and mitigating security issues is centralised in the SOC.
The Security Operations Centre (SOC) has grown as organisations use more linked systems and digital platforms. A SOC manages and responds to security events to protect vital information assets' confidentiality, integrity, and availability. SOC experts are crucial to organisational security, and this introduction will discuss their function in the current cybersecurity scenario.
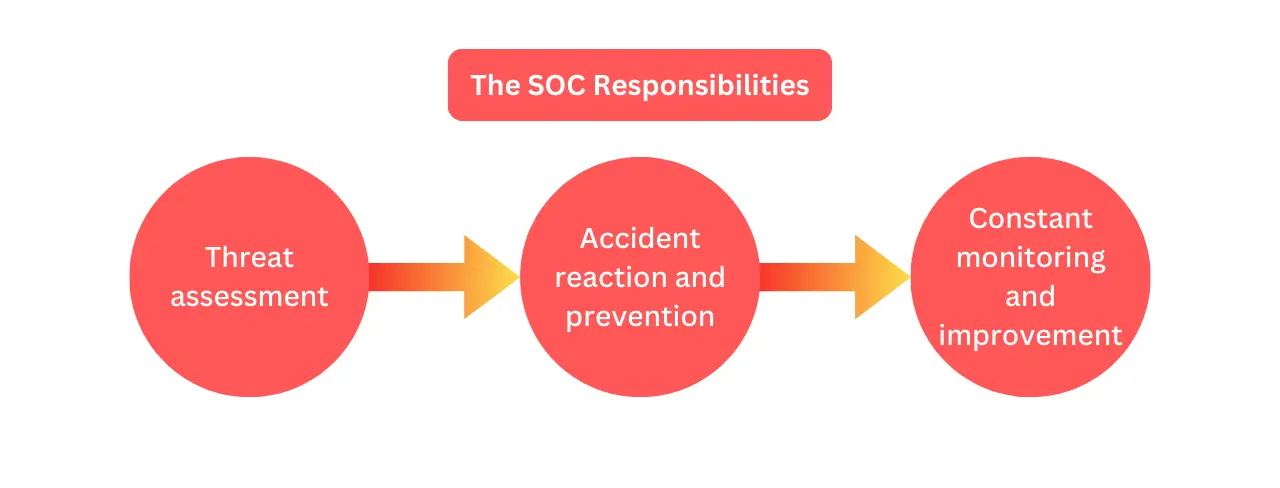
The SOC Responsibilities
Read More: SOC Interview Questions: What to Expect and How to Prepare in 2024
Threat assessment
SOC experts analyse security warnings from numerous sources in real time while doing their (SOC Responsibilities). To discover security concerns, examine network activity, system logs, and other data. SOC workers discover organisational infrastructure abnormalities and vulnerabilities using modern security techniques and technology.
SOC experts analyse hazards to strengthen SOC Responsibilities. This comprises identifying prospective occurrences, understanding harmful actor methods, and measuring organisational asset damage. To enable the organisation to address new security threats, timely and reliable information is provided.
Accident reaction and prevention
SOC experts design and implement incident response strategies as part of their SOC Responsibilities. The SOC leads a rapid and coordinated security incident response. This involves isolating impacted systems, containing the event, and restoring regular operations.
SOC experts update incident response plans based on historical occurrences to satisfy SOC Responsibilities successfully. This iterative technique helps organisations anticipate and respond to cyber threats.
Constant monitoring and improvement
Continuous organisational security enhancement is central to SOC Responsibilities. SOC experts regularly examine, audit, and evaluate security to identify improvements. This proactive method entails monitoring cyber risks, knowing new attack avenues, and changing security measures.
The Cyber Incident Response
Technical knowhow
SOC experts must be technically proficient in Cyber Incident Response. This includes using advanced security tools like SIEM systems to monitor and analyse security occurrences. SOC specialists must also grasp network protocols and cyber threats to identify and respond to security problems.
SOC experts must refresh their expertise to keep up with the changing threat landscape for Cyber Incident Response. Technical competence helps SOC teams quickly and properly understand security data for proactive threat detection and response.
The ability to analyse and solve problems
SOC experts' analytical and problem-solving skills determine Cyber Incident Response success. These duties need quick decision-making under pressure. SOC specialists must analyse complicated data to identify trends, assess security occurrences, and develop appropriate responses.
SOC experts train and simulate to improve Cyber Incident Response. These exercises reinforce the significance of analytical and problem-solving abilities by helping them respond quickly and decisively to real-world security crises.
Cooperation and communication
SOC experts need good communication and teamwork skills for Cyber Incident Response. Clear and timely communication between the SOC team and other cross-functional teams supports coordinated security incident response.
Read More: Top SIEM Tools for Enhanced Security: Features, Comparisons, and Best Practices
Detection of Threats
SIEM systems
SIEM systems are crucial to Threat Detection in a Security Operations Center (SOC). These advanced platforms aggregate and analyse log data from the organization's network. SOC experts use SIEM technologies to analyse trends, abnormalities, and probable compromise indications, improving their threat detection.
SOC experts install and fine-tune SIEM systems to meet the organization's security needs to improve Threat Detection. This proactive strategy equips the SOC to detect and respond to known and undiscovered threats in real time.
IDPS systems detect and prevent intrusions
SOC experts use Intrusion Detection and Prevention Systems (IDPS) in Threat Detection to strengthen the organization's defences. These systems monitor network and system activity using signature-based detection and behavioural analysis to detect intrusions.
To optimise IDPS Threat Detection, SOC experts update and increase the system's signature databases as known threats change. Behavioral analysis also helps the SOC discover and neutralise developing cyber threats.
EDR systems detect and respond
SOC experts use EDR solutions to protect organisation devices as part of Threat Detection techniques. Real-time endpoint visibility from EDR solutions lets SOC personnel notice and respond to suspicious device behaviour.
SOC experts build and maintain these systems to gather and analyse endpoint data to improve Threat Detection through EDR. This proactive monitoring helps the SOC discover and neutralise threats early on, averting security incidents.
Threat intelligence platforms
SOC experts use threat intelligence systems for successful Trojan Threat detection. To give contextual information about emerging risks and prospective adversaries, these systems combine and analyse data from numerous sources, including external feeds.
Information Security Monitoring Tools
Threat detection with AI/ML
The advancement of Security Monitoring Tools has seen a considerable incorporation of AI and ML in Security Operations centers. Security Monitoring Tools use these sophisticated capabilities to automatically analyse large datasets for trends, abnormalities, and security concerns.
SOC experts use complex algorithms that adapt and learn from past data to improve Security Monitoring Tools with AI and ML. This adaptive method allows Security Monitoring Tools to learn and improve, offering a stronger defence against more complex cyber attacks.
Cloud security issues and solutions
With the rise of cloud infrastructure, Security Monitoring Tools have grown to handle cloud security issues. SOC experts use cloud-specific technologies to monitor cloud assets' security.
Cloud Security Monitoring Tools include real-time log analysis, identity and access management monitoring, and anomaly detection to address cloud security issues. SOC experts may use Security Monitoring Tools to protect cloud data and apps using this customised strategy.
Remote workers' concerns
Remote teams in the modern workplace require Security Monitoring Tools to adapt to their problems. SOC experts deploy systems that provide remote access visibility, providing security monitoring of distant employees' endpoints and networks.
SOC Team Structure
Cyberthreats become more complicated
Increasing cyber threat complexity requires a well-defined and adaptable SOC Team Structure. Modern cybersecurity threats are varied; thus, SOC experts collaborate within specialised positions. Threat analysts, incident responders, and security engineers make up the SOC Team Structure, each offering their own abilities to the organization's defence.
SOC Team Structures should have clear communication and duties to combat complex cyber threats. This organisational design lets SOC experts work together, exchange ideas, and respond quickly to security issues.
Lack of cybersecurity experts
Organizations struggle to find experienced cybersecurity personnel. Since demand for competent SOC experts exceeds supply, SOC Team Structure must be optimised for efficiency. Cross-training team members, automating when possible, and encouraging ongoing learning and development are examples.
To address the scarcity of trained experts in the SOC Team Structure, organisations may collaborate with educational institutions, industry alliances, and professional development programmes. Organizations may better manage cybersecurity risks by investing in their SOC Team Structure.
Combining security with usability
SOC experts must balance security and user ease while creating an efficient SOC Team Structure. Organizations must ensure that strict security standards do not hamper productivity or user experience. The SOC Team Structure must contain responsibilities for user education, communication, and feedback to provide a collaborative security strategy that meets organisational goals.
Best Practices for Organisational Security

Regular SOC team training and growth
Security Operations Centre (SOC) teams must be continuously trained and skilled, according to Best Practices for Enhancing Organizational Security. SOC experts must monitor new threats, technologies, and attack channels as cybersecurity changes. SOC teams learn to adapt to the ever-changing cybersecurity environment through regular training, workshops, and industry conferences.
A systematic training program including hands-on exercises, simulated cyber-attack scenarios, and certifications can reinforce Best Practices for Enhancing organizational Security. SOC experts' technical skills and team culture of continual learning and development improve with this method.
Collaboration with outside cybersecurity communities
Collaboration with external cybersecurity communities is essential to Best Practices for Enhancing Organizational Security. To share threat intelligence, insights, and best practices, SOC experts should participate in industry conferences, information-sharing platforms, and collaborative projects. This collaborative strategy gives the SOC access to a wider network of knowledge and strengthens cyber defences.
To promote best practices for enhancing organizational security, organisations might encourage SOC experts to join industry-specific information-sharing groups, attend conferences, and contribute to open-source cybersecurity initiatives. Strong relationships with external cybersecurity communities increase the organization's resistance to emerging threats.
Using threat intelligence in security operations
To achieve Best Practices for Enhancing Organizational Security, threat intelligence must be integrated into everyday security activities. SOC experts should aggressively use threat intelligence feeds, IoCs, and contextual information to improve threat detection and response.
Case Studies
SOC experts handle successful occurrences
Success stories from Security Operations Center (SOC) professionals reveal effective cybersecurity tactics. These SOC teams showed their threat detection, incident response, and mitigation skills. Organizations may benefit from SOC experts' security breach prevention methods by studying particular instances.
Organizations may anonymize and disseminate information of prior security occurrences to explain SOC team actions in case studies. Analyzing these examples helps improve incident response strategies, threat detection, and cybersecurity resilience.
Security breach lessons
Comparing successful security breaches Case Studies can help organisations strengthen their defences. SOC experts help identify root causes, weaknesses, and improvement opportunities after an event. These Case Studies can help organisations understand security breaches and prevent future ones.
While maintaining anonymity, sharing security breach case studies helps organisations learn from mistakes and vulnerabilities. This open approach promotes continual cybersecurity progress, as prior instances inform security plans.
Organisational continuous improvement techniques
To complete Case Studies, organisations can share their cybersecurity improvement experience. Case Studies show how organisations and SOC experts have introduced new technology, refined procedures, and altered tactics to handle increasing cyber threats. Organizations share success stories to build knowledge and inspire others to develop.
Organizations may document their cybersecurity posture evolution in case studies demonstrating continual progress. Advanced security technology, SOC team restructuring, and proactive threat detection may be used. Case Studies inspire organisations to improve cybersecurity resilience and maturity.
Read More: What is soc in cyber security: Roles and Importance.
Conclusion:
Security Operations Centre (SOC) expertise are essential to organisational security in the face of growing cyber threats. SOC Team Structure and Threat Detection are the foundation of a strong cybersecurity system. As seen in the Case Studies, SOC experts are crucial to incident management, security breach learning, and ongoing improvement.
Advanced Security Monitoring Tools help the SOC notice and respond to attacks faster. Artificial intelligence and machine learning improve Security Monitoring Tools and promote proactive and adaptive cybersecurity. Modern organisational structures require customised Security Monitoring Tools to address cloud security and remote work issues.
To maximise outcomes, organisations must prioritise Best Practices for Enhancing Organizational Security. This requires frequent SOC team training, communication with external cybersecurity groups, and threat intelligence integration into security operations. These Best Practices can help organisations build a resilient cybersecurity posture that proactively defends against shifting threats.
As organisations traverse online, SOC experts and their varied SOC Responsibilities are crucial. By adopting new technologies, encouraging cooperation, and learning from triumphs and failures, organisations can empower their SOC teams to lead organisational defence and guarantee a robust digital future.







Anshul Goyal
Group BDM at B M Infotrade | 11+ years Experience | Business Consultancy | Providing solutions in Cyber Security, Data Analytics, Cloud Computing, Digitization, Data and AI | IT Sales Leader