IPS and IDS Explained: Key Differences and How They Protect Your Network
As the world becomes more digitalised, it is apparent that cyber threats are on the rise and one’s network needs to be protected now more than ever.

IPS and IDS Explained: Key Differences and How They Protect Your Network
Table of Contents
As the world becomes more digitalised, it is apparent that cyber threats are on the rise and one’s network needs to be protected now more than ever. Intrusion Prevention Systems (sometimes referred to as IPS) and Intrusion Detection Systems (also called IDS) stand out among other safety-critical security technologies aimed towards mitigation of harmful activities towards computing systems. But though both aim at ensuring network security for a security system, their objectives are quite different. This blog will address the differences as well as similarities between IPS and IDS, the methods of implementation of both, and their reasons for existence in a secure network.
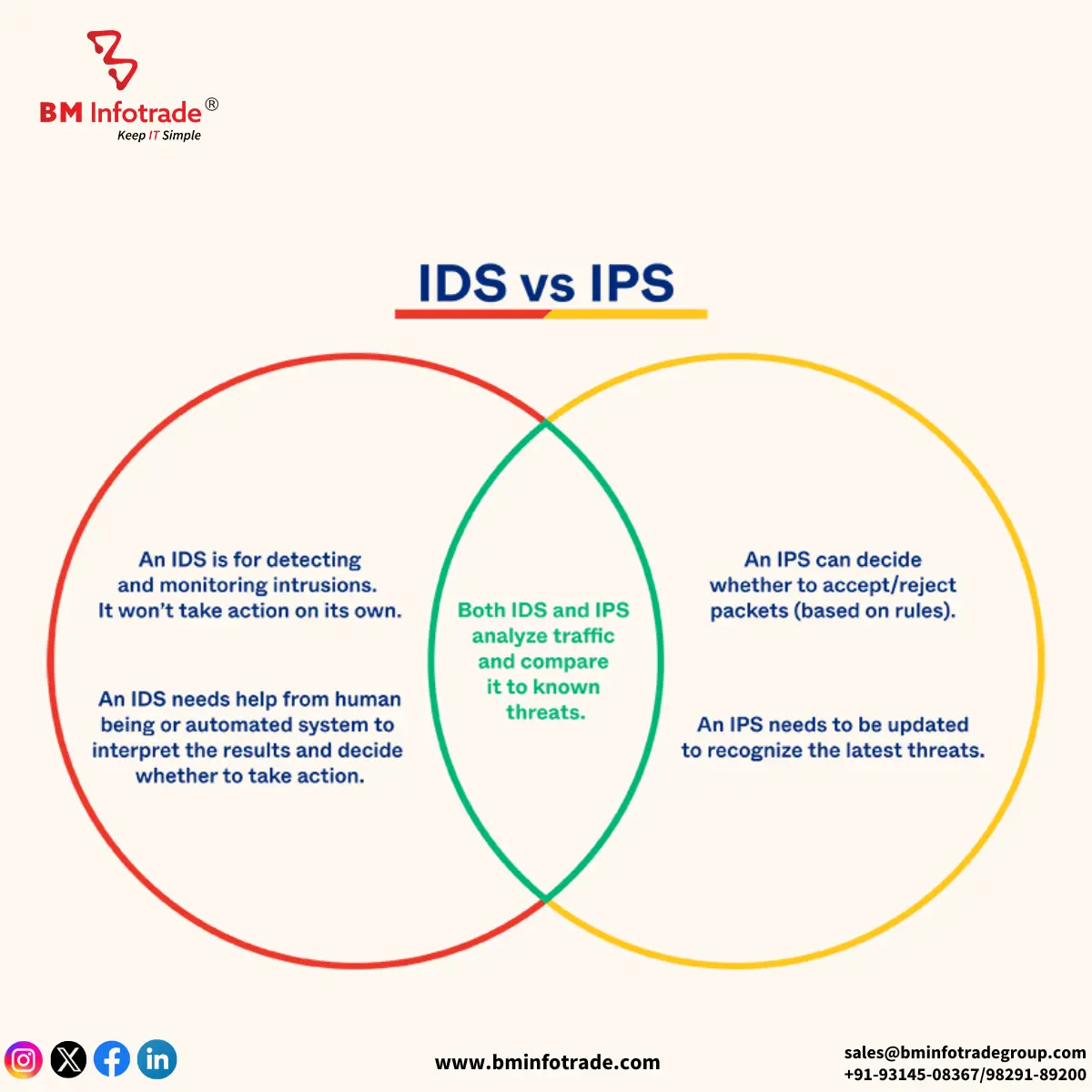
What is an Intrusion Detection System (IDS)?
An Intrusion Detection System, referred to as an IDS, is a network-based security device that is devised to recognize and give warnings of growth in nefarious activity in the protected networks. IDS is a device that is always monitoring and inspecting the network activity looking for unusual and unauthorized activities, in real-time. The IDS rather can detect suspicious and/or potentially harmful activity, analyze the situation and inform the network operators through alarms, reports or reorganizing the system but they do not intervene.
-
Passive Monitoring: In this type of system, expeditionary actions are prohibited i.e. there is no attempt at blocking a threat, the IDS only identifies a threat.
-
Alert Generation: A set of actions has to be taken e.g. informing users etc., when such hot events are identified so they don’t get out of hand.
-
Log Analysis: NetOps, or IDS in this case logs everything that is happening in the network and all the information is also kept somewhere. This is important so that forensic analysts can piece together what has happened; where and how the attack took place and where the damage was caused.
What is an Intrusion Prevention System (IPS)?
Intrusion Prevention System is a more enhanced type of network security that not only identifies threats but also eliminates them actively. As with Intrusion Detection System (IDS), IPS also performs real time analysis of network traffic, but unlike IDS, IPS not only detects a threat but also takes preventive measures by blocking or minimizing the threat.
-
Active Response: No threats are left unattended concerning insecurity, there are active measures whereby abusive packets are dropped, and degrading traffic from dubious IP addresses is cancelled.
-
In-line Operation: An IPS strategically sits at the point where traffic flows so that there is immediate traffic inspection and interaction when packets are being processed.
-
Automated Protection: Using IPS network administrators are not required to override every time there is a detector of a threat upon witnessing there has been a threat.
Key Differences Between IPS and IDS
-
IDS: Like a camera, it detects suspicious activities on the network and merely sounds the alarm, since there are no ill effects to prevent.
-
IPS: Takes a more assertive action against all detected threats. In addition to a warning, all such threats noticed will be blocked or at least neutralized where they can do The most harm.
-
IDS: Can be termed as passive in that it examines information of the traffic but does not in any way meddle with the traffic being progressed.
-
IPS: Executes a policy inside a corporate network and checks the data packets so that th
-
IDS: Looks for activity requiring the attention of a network administrator.
-
IPS: Makes automatic changes to the network configuration, to eliminate or prevent the observed threats.
-
IDS: Has very little effect on the performance of the network because it acts as a passive sensor and only looks and studies the traffic.
-
IPS: This is one such measure that can have latency because addressing and making changes to the traffic is done as and when the traffic is being forwarded.
-
IDS: Most appropriate in circumstances where only a minimal response is required for a passive detection of activity – Small networks or those which make most if not all of their investigations of an insider threat.
-
IPS: Most suited in a scenario of large network systems, or highly sensitive context in unduly high seeing that a concerted effort must be made in guarding against external attacks.
How IDS and IPS Work Together
Even though nothing is ever perfect IDS and IPS separate systems seamlessly fit in together in a security-in-depth environment. For better network defences, most organizations will equally combine the usage of the two systems. This is done by:
-
Early detection (IDS): There might be early indications which suggest that the threats are very likely to occur and this is when detection systems seek to monitor. There might be no imminent scope for a counter detection solution like the situation radical.
-
Immediate Prevention (IPS): As a protection measure, IPS immediately prevents or reduces any attacks or risks and stops them from getting any further into the networks.
This mode enables detection and fast response that enables companies to protect themselves from many forms of cyber threats.
Why IDS and IPS Are Important to the Security of the Network
Continuous Monitoring and Mitigation
IPS and IDS collaboratively work in the erosion control activities in such a way that detection and incidence response is indeed in real-time. However, using IPS organizational policies aims to block an attack before it leads to any damage whereas IDS captures all suspicious activities for further investigation.
Countering Actionable Threats
Cyber threats changes with time, as new technology comes up, chances are some malicious people will come up with new strategies on how to cause harm. With however both IDS and IPS, very few cases are likely to go undetected as their primary aim is to find ways to capture these new levels of offensive attacks.
Legal and Prevention Issue
To protect the data collected especially sensitive data, most industries are subject to compliance requirements. Such logs and alerts generated by the IDS are essential in helping achieve compliance. Additionally, the use of IPS makes certain that the outlined policies about public, private & sensitive details are adhered to by restricting intruders from overstepping the defined limits.
Defence in Depth
One security solution alone is often never enough. Organizations will enhance their preparedness against attacks by integrating IDS and IPS as part of the wider security strategy. IDS is intended to detect stealthy insider or external threats, while IPS prevents such externally initiated and direct attacks.
Challenges of Implementation of IDS and IPS
Even though IDS and IPS can change the standard tools used for network security, they are not without problems as well as major benefits:
-
False Positives/Negatives: Both systems rely on patterns or rule based methods. This may lead to false positive (normal but marked as a threat activity) or false negative (threat activity goes undetected). Proper configuration and continuous updates are important in order to solve this problem.
-
Network Latency: IPS systems also create latency, particularly when there is a need to inspect and monitor live traffic. There is a need of implementation and optimization for networks that demand a high speed and low latency performance.
-
Management Complexity: Allocation of resources and expertise towards monitoring and maintenance of IDS and IPS systems is warranted. Network administrators are expected to actively manage the response by analyzing alerts, signature updating and performing system validation activities.
Read More:- Top SIEM Tools for Enhanced Security: Features, Comparisons, and Best Practices
Conclusion
Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) are considered to be the building blocks of today’s network security systems. IDS is primarily concerned with the detection of threats or bringing timely alerts, action is what bypasses all potential threats to the property in real-time hence it is termed IPS. Jointly they offer a complete umbrella cover for any threats and insecurities on the network through active monitoring and response discovered in the shortest time possible.
With the ever-growing and improving interconnectivity of the world, at least deploying such features of IDS and IPS devises organizations in addressing the sharing and emerging threats and risk management of their networks.







Anshul Goyal
Group BDM at B M Infotrade | 11+ years Experience | Business Consultancy | Providing solutions in Cyber Security, Data Analytics, Cloud Computing, Digitization, Data and AI | IT Sales Leader