The usefulness of VAPT in Cyber Security, Tools, and Testing.
Explore the role of VAPT in cybersecurity, including its benefits, essential tools, and testing methodologies to enhance your organization's security posture.

The usefulness of VAPT in Cyber Security, Tools, and Testing.
Table of Contents
VAPT, also known as vulnerability assessment and penetration testing, is a basic need in today’s digital world; it helps companies, websites, applications, and other systems to find flaws in their network or system.
VAPT is an amazing approach to cyber security. It is very necessary to know it and find solutions for our cyber security vulnerabilities.
It ends vulnerabilities and strengthens security in the system. VAPT’s security audit is done by a series of processes that involve various tools and methods.
VAPT what is it?
VAPT Testing is a process of scanning for weaknesses/vulnerabilities in a system and removing them. This process contains two parts, first is Vulnerability assessment, in which the process finds flaws in their codes. It also shows the location of vulnerable code.
In the second part, we see penetration testing, by which we try to determine and exploit the vulnerabilities. We also determine if some unauthorized person has access or if some other kind of bad activity is possible.
This assessment and testing is a continuous process, which a business should consider conducting to find out weaknesses in their system. Most large-scale businesses conduct VAPT and remove their flaws for better performance.
This procedure can be performed automatically as well as manually. Most of the companies prefer to do this procedure automatically because the automatic procedure is less time-consuming.
Read More : Basics of Network Technologies: Benefits of Networks
How can you do VAPT testing?
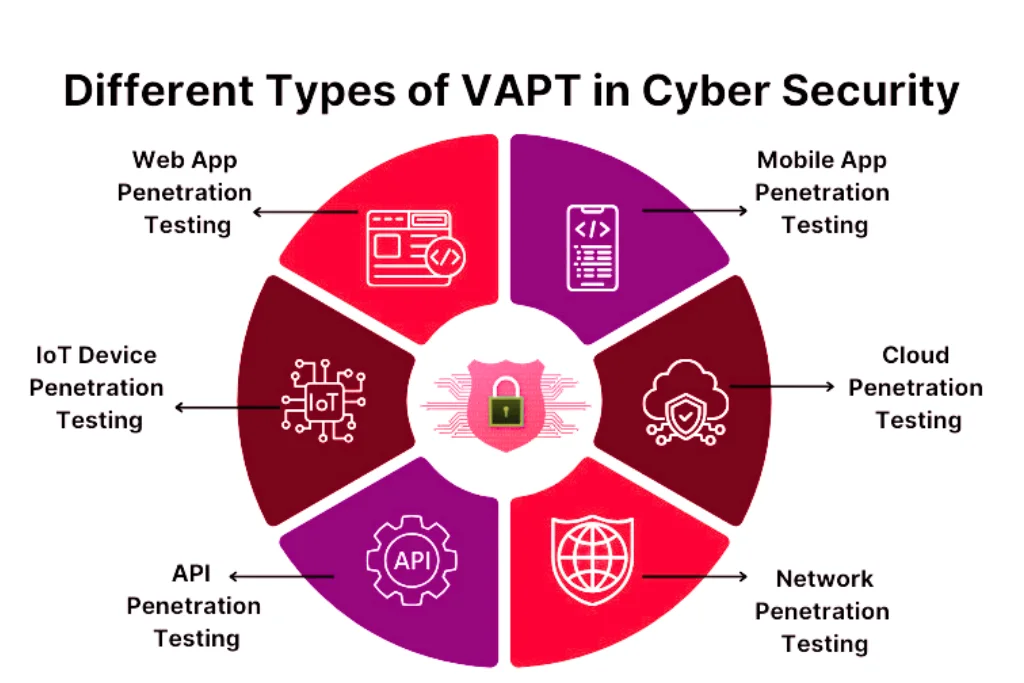
Different types of vapt testing help in analyzing systems.
Types of VAPT testing:
Network Penetration Testing
Network penetration testing is a real-life attack simulating a cyberattack against your system. It helps to discover the vulnerabilities that can be exposed to hackers. This testing involves various hacking methods to identify weaknesses in your security system. These tests are real methods and approaches that hackers use against your system.
There are four major steps that this testing should take.
- Planning
- Testing
- Accessing networks
- Analysis
These four steps are generally used in network penetration testing, by which we can see the security of a network or system. It's an ideal way to simulate a cyberattack.
It is one of the most used and effective ways for security checking against cyber attacks.
Web Application Penetration Testing
A web application penetration test is a simulation in which we attack the system externally and internally to determine the security of the system. By doing this, we identify loopholes and vulnerable routes in applications.
Web application pen testing also assesses existing security policies for any vulnerability.
This process is conducted in three major steps
-
Configuring your testing
-
Executing (External and internal penetration tests)
-
Analyzing the test
As the name suggests, this testing is generally used to analyze the cyber security of the website. The main work of this testing is finding weaknesses in web applications.
Read More : Why Cloud Computing is Necessary, it meaning and virtualization
Mobile Penetration Testing
In the present time, mobile applications are used for many purposes like commercial, healthcare, banking, education, and more. The application holds very important and sensitive details about the user. To avoid getting your data leaked, we need good cyber security. We also want to know whether our security is doing its work or not. To do this, we need mobile penetration testing.
The main purpose of this testing is to find out if the application is leaking confidential data or not.
Mobile Penetration testing includes testing of mobile apps such as:
-
iOS Penetration Testing for iOS apps
-
Android penetration testing for Android apps
-
Hybrid Apps
-
Progressive web app (PWA)
API Penetration Testing
API, also known as Application Programming Interface penetration testing, is a vital part of any security infrastructure. Because, as you know, an API enables two different systems to communicate with each other and work together.
Many companies have various APIs that allow their employees to interact with other tools and data.
API penetration testing is the best way to ensure the security of APIs.
Cloud Penetration Testing
Cloud penetration testing includes the same testing as we mentioned above but it works on cloud-native systems. This security testing analyzes the cloud computing environment. The common threats a cloud-based system faces are security vulnerabilities, data breaches, malware/ransomware, and supply chain vulnerabilities.
It mainly finds the vulnerabilities in a cloud-based system that hackers could use. It also determines whether the cloud provider’s security is up to measure or not.
Some companies hire a third-party security firm that performs testing on the company’s cloud infrastructure.
The following are cloud penetration testing methods:
- Transparent box testing
- Semitransparent box testing
- Opaque box testing
Which Testing tools in Open source can be useful for VAPT in cyber security?
As companies and the Digital world grow, data breaches also grow with it. Data breaches are one of the most problematic things for a business. It is a huge problem. Data breaches can scatter the image of a company and lose the trust of customers.
VAPT can help you avoid data breaches. To help you with that you can use VAPT testing tools in Open source.
Best performing VAPT Testing tools in Open source:
Wireshark
Wireshark is a free and open-source analyzer that can perform VAPT. It is also used for software analysis and network troubleshooting. This tool was originally named Ethereal, but the name was changed in 2006 because of some trademark issues. But still, this is one of the most popular network analyzers in the world.
This tool helps ethical hackers analyze the patterns and systems of malicious software.
Wireshark has key features:
-
Live view of packets arriving
-
Color-coded identification in packets (also can be customized)
Nmap
Nmap is an Open-source network scanner that was created by Gordon Lyon. this tool is used for monitoring and discovering hosts in network connections. The Nmap tool is available free of charge. You can also download it.
Nmap has key features:
-
It is used for probing computer networks
-
Also used for Host Discover and service
-
Detection of operating system
Metasploit
Metasploit initially came in 2003. As you can understand, this is a computer security tool that helps in VAPT.
It has framework processing exploit code against a remote target machine. It is open source and it uses Metasploit in making and validating the exploit code.
Conclusion
In conclusion, vulnerability assessment and penetration testing (VAPT) is a security procedure used by companies and organizations to analyze their cyber security. VAPT was developed and designed to test and analyze the overall security.
If you work in the cyber world, then you should consider VAPT to your system so that you can analyze your cyber security and eliminate the weakness in your system.








Anshul Goyal
Group BDM at B M Infotrade | 11+ years Experience | Business Consultancy | Providing solutions in Cyber Security, Data Analytics, Cloud Computing, Digitization, Data and AI | IT Sales Leader