What types of assessments and evaluations are used in cyber security training?
Learn about various kinds of assessments and evaluations commonly used in cybersecurity training

What types of assessments and evaluations are used in cyber security training?
Remaining ahead of possible hazards is vital in the rapidly changing field of cybersecurity. Continuous learning and re-training are obligatory to keep up with the ever- evolving world of cyber security. Therefore, cyber security professionals should have abilities for identification, mitigation, and response against various types of security issues. As such examinations are conducted as a yardstick for ascertaining whether given cyber training programs have the right competencies among their students. It will concentrate primarily on some forms of appraisals and evaluations that are critical in cyber security training.
The Importance of Assessments in Cybersecurity Training

Before delving into the various types of tests, it is vital to grasp why assessments are important in cybersecurity training. These appraisals serve different objectives:
1. Verification of Skills: They can be used to gauge how far trainees have gone.
2. Detecting Weaknesses: It is a process that identifies areas where learners are not strong.
3. Application in Real Life: The reason behind this is to make sure that students can apply their knowledge practically.
4. Certification: In many cases certified industry certifications require them.
Knowledge-Based Assessments
Knowledge-based evaluations are designed to measure the intellectual comprehension of cybersecurity principles. They are mostly composed of:
1. Multiple Choice Questions (MCQs): These appear regularly in cyber security certifications or training programs and can range from primary through to advanced levels.
2. True/False Questions: Answers to such questions would confirm whether one has understood simple concepts within seconds.
3. Short Answer Questions: Short answer questions are those that require detailed responses where issues beyond simply understanding a given subject matter are involved.
Practical Hands-On Assessments
In cybersecurity training, practical hands-on assessments are one of the most important aspects as they usually duplicate real-life situations. Some of them include:
1. Lab Exercises: This may be done by instructing students to do certain activities under some controlled conditions like building an intrusion detection system or setting up firewalls that mimic some real challenges that a learner may face shortly after employment and become helpless without anyone’s assistance.
2. Capture the Flag (CTF) Competitions: The CTF competitions work towards validating hands-on skills such as flag capturing through solving cyber-security challenges. As such, these contests might feature elementary assignments and multi-tiered problems that grow more complicated with each level.
3. Red Team/Blue Team Exercises: In this situation, red teaming is for the sake of simulating attacks while blue teaming represents defense. Hence these exercises allow those being trained to understand offensive and defensive strategies in cyber security.
Read More: What is an intruder in cyber security: Navigating Threats
Simulation-Based Assessments
Simulations provide a controlled environment where trainees can practice responding to cybersecurity incidents. Types of simulation-based assessments include:
1. Cyber Range Exercises: It could be described as a mock-up cyber environment that emulates real-life networks and systems. It is here that trainees can practice defending against attacks in a real-life scenario.
2. Incident Response Simulations: Participants are required to handle simulated cyber incidents like dealing with hacked websites, this helps them see how they would respond to real-world cyber security breaches.
Performance-Based Assessments
Performance-based assessments evaluate how well trainees can apply their knowledge and skills in practical situations. These assessments include:
1. Real-Time Problem Solving: They require learners to resolve issues within some set deadlines and then rate their final results based on accuracy and speed of response.
2. Case Studies: These are detailed cybersecurity incident scenarios where learners analyze and make responses. This tests their analytical skills as well as decision-making abilities.
Continuous and Formative Assessments
Continuous and formative assessments are used throughout the training process to provide ongoing feedback and improvement. These assessments include:
1. Quizzes: Regular quizzes help reinforce learning and ensure that trainees retain information.
2. Peer Reviews: Trainees review each other’s work, providing feedback and insights. Thus, collaborative learning is promoted among the students.
3. Self-Assessments: This allows the learner to evaluate his or her understanding and progress towards achieving certain objectives to know areas needing further improvement.
Summative Assessments
Summative assessments are done at the end of a training initiative to evaluate the overall learning and competency. They include:
1. Final Exams: A comprehensive examination that covers all the material taught during the training program.
2. Project Work: It entails an activity where trainees merge what they had learned all along in the course period.
3. Certification Exams: These are exams offered by industries such as CompTIA, Cisco, (ISC)² among others, which are required to confirm one’s knowledge and skills formally
Soft Skills Assessments
Individuals working in cybersecurity require more than just technical expertise; soft skills are also important. The evaluations carried out in this area include:
1. Communication Skills: Evaluations that test how well learners can simplify technical details to be understood by others.
2. Teamwork and Collaboration: Assessments that measure how effectively individuals work within groups, which is vital for job functions requiring collaboration.
Automated Assessments
Automated assessments have become more common with technological advancements. They consist of:
1. Automated Testing Tools: Tools that automatically check code for security flaws.
2. AI-Based Assessments: These are methods where artificial intelligence evaluates trainee performance and offers personalized feedback.
Emerging Trends in Cybersecurity Assessments
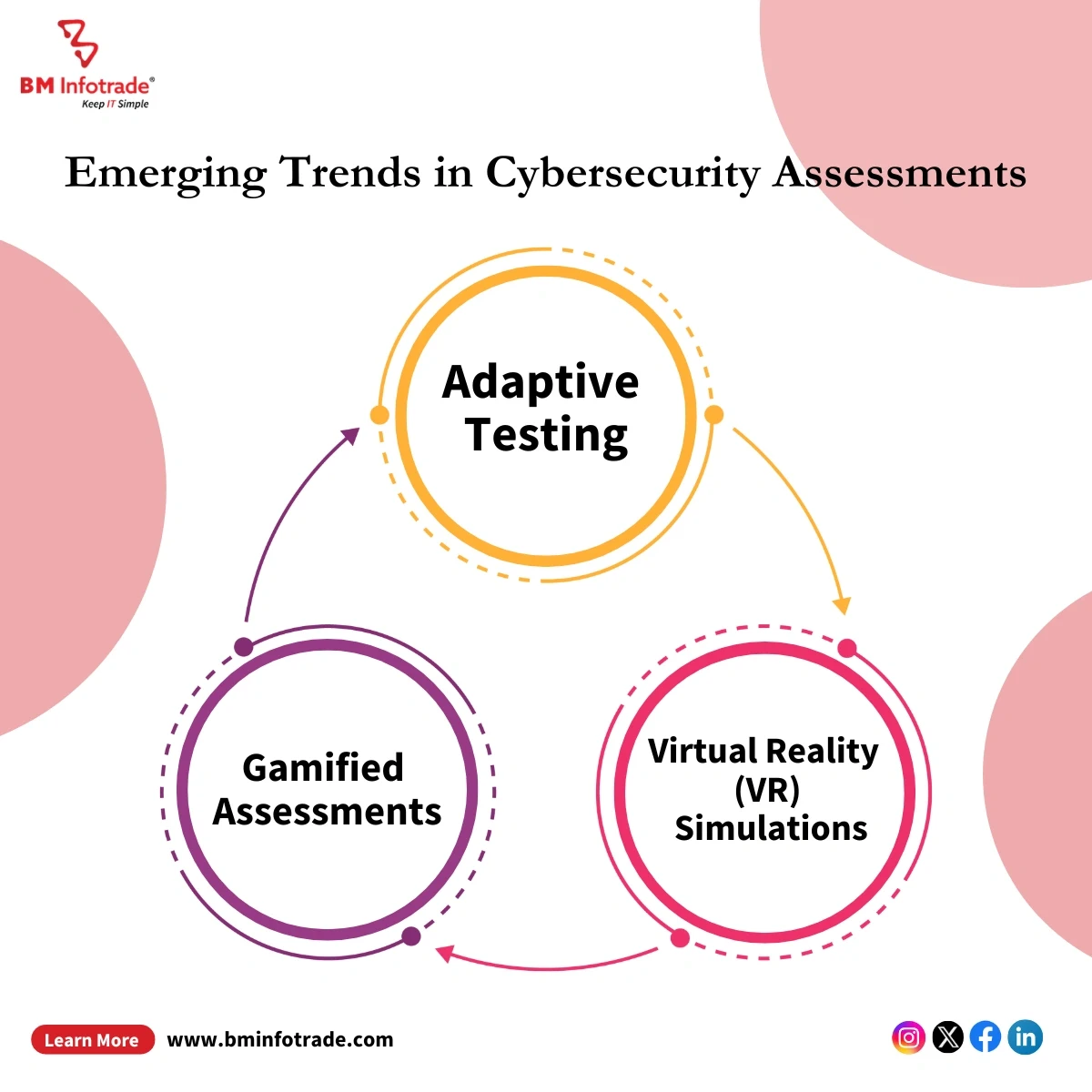
The field of cybersecurity is always changing, and so too should assessment strategies. Some emerging trends include:
1. Adaptive Testing: It is about appraising how well examinees performed and then adjusting their complexity accordingly.
2. Gamified Assessments: The incorporation of elements similar to those found in video games into evaluation tools makes them more fun-filled and thus motivating.
3. Virtual Reality (VR) Simulations: Highly immersive virtual environments provide lifelike experiences during training sessions thereby making them interactive as well as realistic.
Conclusion
Effective cybersecurity training cannot take place without --assessments and evaluations. This includes certification for participants who complete the programs after their completion, ensuring they gain relevant knowledge while being tested on their ability to apply it in real-life situations. Each type of assessment, whether it is knowledge-based or a practical simulation, plays an important role in preparing students to be comprehensive cybersecurity professionals. The methods of assessment will change with the growth of the field so that cybersecurity experts will never lack the latest expertise to counter emerging threats.
Various forms of assessment can be used in cyber security training programs to ensure well-rounded skills development and equip professionals for effective protection of digital assets within a highly complicated cyber environment.







Anshul Goyal
Group BDM at B M Infotrade | 11+ years Experience | Business Consultancy | Providing solutions in Cyber Security, Data Analytics, Cloud Computing, Digitization, Data and AI | IT Sales Leader