What is an intruder in cyber security: Navigating Threats
Intruder in cyber security: cyber security safeguards sensitive data, activities, and reputations in today's connected world.

What is an intruder in cyber security: Navigating Threats
Table of Contents
- Cyber Threat Types
- Evolution of Cyber Threats
- Statistics on Cyber Attacks
- What is an intruder: Intruder Profile
- Categories of Intruders
- Anatomy of an Attack
- Security Information and Event Management (SIEM)
- Endpoint Detection and Response (EDR)
- Future Trends and Challenges: AI and Machine Learning in Cyber Security
- Internet of Things (IoT) Security: Proliferation of IoT Devices
- Quantum Computing and Cryptography:
- Conclusion
Intruder in cyber security: cyber security safeguards sensitive data, activities, and reputations in today's connected world. Cyber security protects computer systems, networks, and data from unauthorised access or harmful attacks. Individuals, businesses, and governments depend on it.
Cybersecurity requires understanding the intruder—the hostile actor. Defenders can anticipate, recognise, and halt invaders by studying their aims, methods, and actions. This understanding helps security professionals predict cyber attacks and defend proactively.
Cyber security threats and intrusions are covered here. Intruder features, tactics, strategies, and detection and mitigation solutions are covered in this review to build a full cyber security foundation for digital environments.
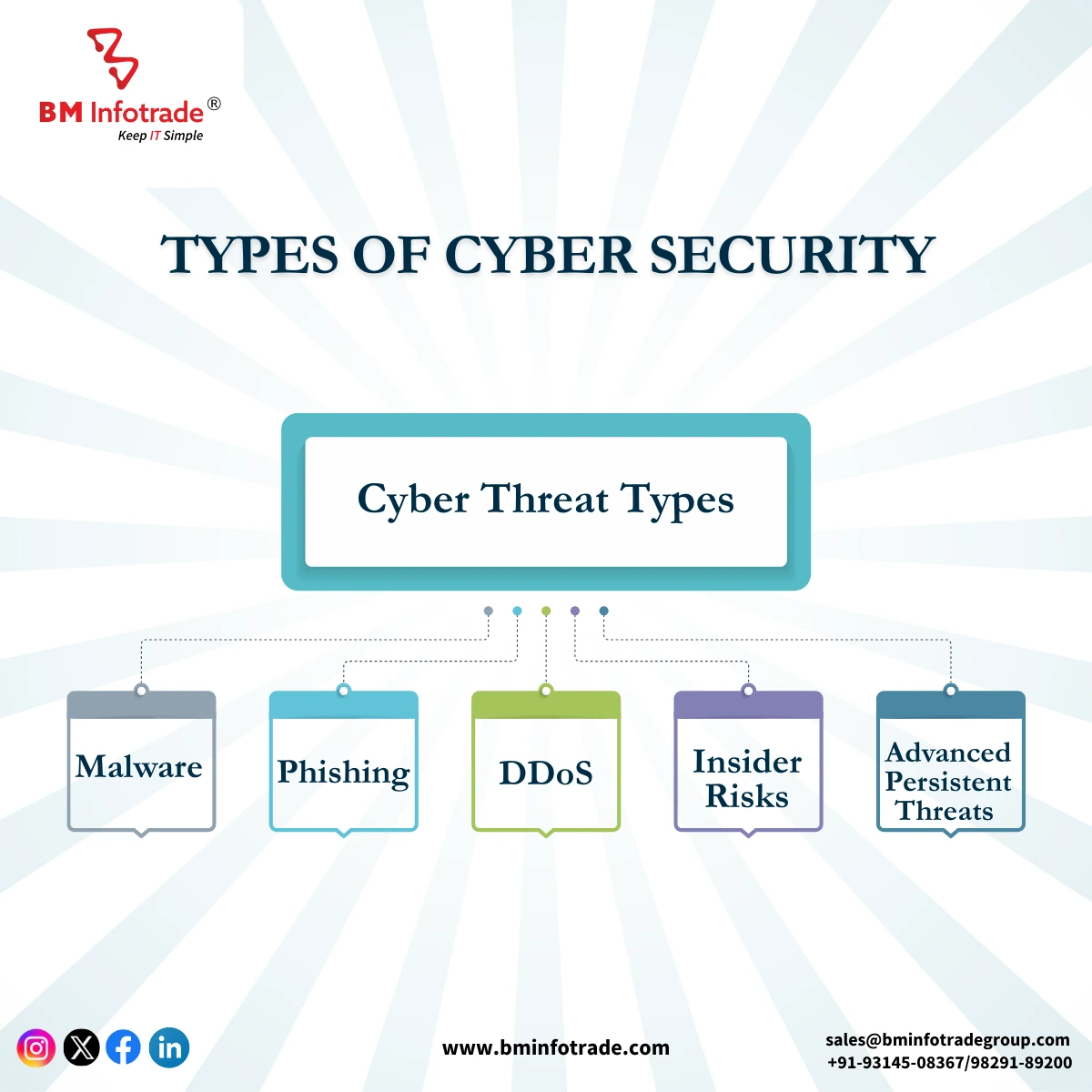
Cyber Threat Types
Malware: A wide range of software affect computers and networks as malware. Example: viruses, worms, Trojans, ransomware, and spyware. Malware spreads via email attachments, rogue websites, and external storage.
Phishing: Phishing attacks use fake emails, messages, and websites to steal passwords, credit card numbers, and personal information. These assaults spoof financial or political institutions and employ psychology to fool victims.
DDoS: Distributed Denial of Service (DDoS) assaults flood a server or network with traffic, disrupting online services. A botnet of infected devices is used to coordinate assaults that make the target inaccessible to authorised users.
Insider Risks: Employees who misuse access credentials to harm security are insider threats. Disgruntled employees leaking sensitive information, reckless conduct creating data breaches, and unwitting insiders being socially engineered are examples.
Advanced Persistent Threats (APTs): Professional threat actors with nation-state or organised criminal assistance conduct long-term cyber espionage as APTs. These attackers sneak into target networks, grab data, and seize control.
Read More: Concepts of Cyber Security: Protecting Information
Evolution of Cyber Threats
Cyber risks fluctuate with technology, attacker tactics, and geopolitical forces. Complex, organised operations by well-funded, determined opponents have replaced isolated instances by lone actors. Artificial intelligence, blockchain, and the Internet of Things introduce new attack avenues and increase cyber dangers.
Statistics on Cyber Attacks
Cyber attack statistics demonstrate the danger landscape and the necessity for strong cybersecurity. Industry organisations, government bodies, and cybersecurity corporations report a consistent growth in cyber attack frequency, sophistication, and financial impact across sectors. These data demonstrate the pervasiveness of cyber dangers, requiring proactive defences and persistent monitoring to limit risks.
What is an intruder: Intruder Profile
Motivations: Espionage, ideology, revenge, or financial gain may motivate cyberattackers. Understanding incentives helps forecast and reduce risks.
Skillset: Beginners employ ordinary tools, but programmers, cryptographers, and network penetration testers are competent.
Tactics, Techniques, and Procedures (TTPs): Intruders use TTPs to achieve their goals. Social engineering, exploit kits, zero-day vulnerabilities, and evasion tactics can overcome security and avoid discovery.
Categories of Intruders
Hackers: Technically skilled hackers exploit computer systems or network weaknesses for various objectives. There might be ethical hackers who properly report vulnerabilities or criminal hackers who exploit vulnerabilities for personal gain or publicity.
Script Kiddies: With low technological abilities, script kiddies use pre-packaged tools and scripts to execute cyber assaults without comprehending the mechanics. Although less skilled than other intrusions, script kiddies might nonetheless constitute a problem due to their easy access to automated attack tools.
State-sponsored actors: Cyber espionage, sabotage, and warfare are used by states to achieve geopolitical aims. These adversaries are stronger online owing to their advanced skills and resources.
Cybercriminals: For profit, cybercriminals steal data, perpetrate fraud, extort, and steal identities. They may steal data, perpetrate ransomware, credit card fraud, or online fraud on underground forums.
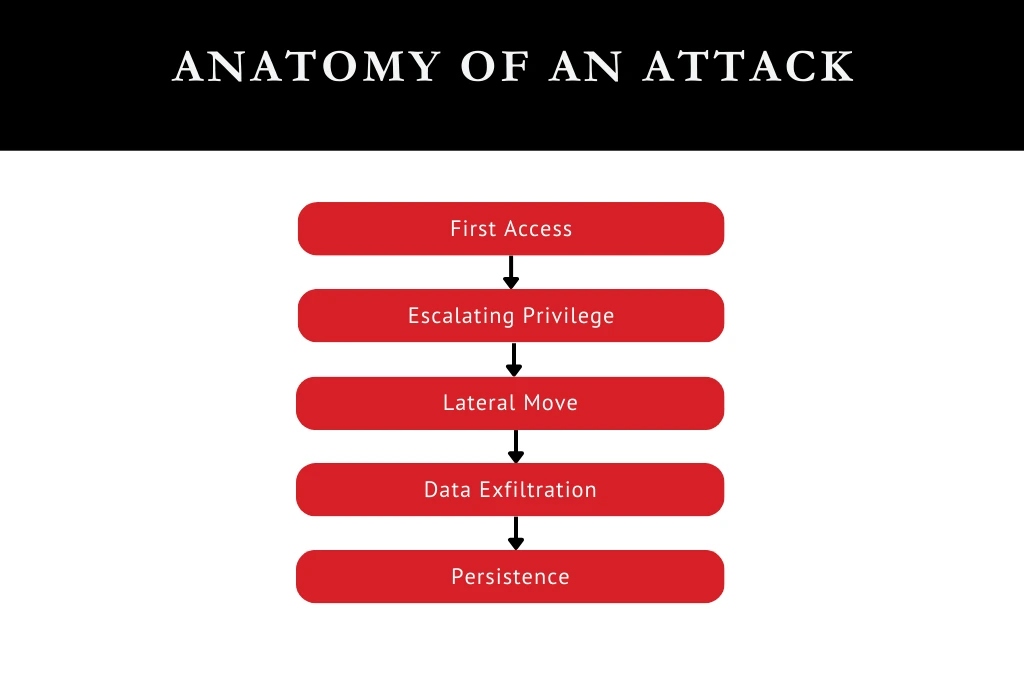
Anatomy of an Attack
Reconnaissance: Network infrastructure, software weaknesses, and employee credentials are scouted by intruders. Open-source information collection, port scanning, and network enumeration may be used in this phase.
First Access: Intruders use weaknesses to obtain initial access to the target network or system after reconnaissance. This may entail exploiting unpatched software vulnerabilities, misconfigured services, or poor authentication techniques to obtain network access.
Escalating Privilege: After gaining access, attackers increase their rights to dominate the target environment. They may attack more vulnerabilities or steal credentials to get access and move laterally in the network.
Lateral Move: Intruders travel laterally around the network, examining systems and compromising hosts to get access to important resources. In this phase, reconnaissance, privilege escalation, and backdoors or persistent techniques may be used to maintain access.
Data Exfiltration: After achieving their goals, intruders steal sensitive data from the target environment. This may entail copying data, stealing IPs, or obtaining passwords for future use. Stealth data exfiltration maximises breach impact and avoids discovery.
Persistence: Intruders use backdoors, rootkits, and other covert methods to stay in the target environment and avoid detection. They can maintain a network presence for future activities or exploit new resources over time.
Techniques for Detecting and Mitigating Intrusions: Intrusion Detection Systems (IDS)
Network-based IDS: Network-based IDS analyses packet headers and payloads in real time to detect harmful patterns or signatures. For extensive coverage and early intrusion detection, NIDS sensors are strategically placed across the network architecture.
Host-Based IDS (HIDS): Host-based IDS monitors servers, workstations, and endpoints for activity and integrity. Each host's HIDS agents monitor system logs, file integrity, and process activity for unauthorised access, malware infections, and suspicious behaviour.
Security Information and Event Management (SIEM)

Log Aggregation: SIEM solutions collect logs from network devices, servers, apps, and security appliances. SIEM provides enterprise-wide insight into security incidents and abnormalities by centralising log data.
Event Correlation: Event correlation enriches raw log data with contextual information to prioritise warnings and discover advanced threats in SIEM. To provide actionable insights and alarms, correlation rules and algorithms analyse event sequences, user behaviours, and threat intelligence feeds.
Read More: 5 Essential Cybersecurity Facts!
Endpoint Detection and Response (EDR)
Endpoint Viewability: EDR solutions allow security teams to detect and respond to threats throughout the endpoint landscape by providing real-time insight into endpoint activities, processes, and behaviours. To detect compromise, endpoint agents monitor system activity, file alterations, and network connections using telemetry data.
Threat-hunting: EDR helps security analysts discover risks by performing forensic investigations, analysing endpoint data, and identifying IOCs and attack patterns. Advanced analytics, machine learning, and threat intelligence in threat hunting reveal hidden dangers and eliminate security concerns before they worsen.
Network Segmentation: microsegmentation: Segmenting the network into smaller zones reduces cyber dangers and lateral movement. Application, user, and workload-based access limits in micro-segmentation decrease the attack surface and prohibit unauthorised access to vital resources.
User Training and Awareness
Security Awareness Programmes: To decrease human error in cyberattacks, user training and awareness initiatives educate cybersecurity, threat awareness, and social engineering. User training, phishing simulators, and interactive exercises assist identify and report unusual behaviour.
Vulnerability Management: Vulnerability checking: Scanning IT assets for known vulnerabilities, misconfigurations, and flaws that attackers may exploit is vulnerability management. Organisations may patch vulnerabilities and minimise security exposures proactively using automated vulnerability scanners that prioritise repair by risk severity.
Incident Response Planning:
Incident Response Framework: Incident response planning helps manage security breaches and cyberattacks. To respond to security incidents quickly and efficiently, teams create roles and playbooks and conduct tabletop exercises.
Future Trends and Challenges: AI and Machine Learning in Cyber Security
Threat Detection and Response: AI and ML are automatically analysing huge security data to detect patterns, irregularities, and new threats in real time.
AI adversaries: Threat actors' methods for evading detection and manipulating AI algorithms improve with AI and ML. In protecting against sophisticated attackers, adversarial machine learning and model poisoning attacks provide new cybersecurity difficulties.
Internet of Things (IoT) Security: Proliferation of IoT Devices
Internet-connected devices in households, companies, and critical infrastructure create new attack surfaces and vulnerabilities, complicating IoT ecosystem cybersecurity.
Design-Based Security: To prevent threats from insecure setups, default passwords, and lack of update procedures, IoT devices and systems must be designed with security measures.
Quantum Computing and Cryptography:
Quantum Computing Risks: Quantum computing may make cryptographic methods like RSA and ECC susceptible to quantum-enabled assaults that might break encryption and compromise sensitive data.
Post-QC Crypto: Standards are being established for quantum computing-resistant post-quantum cryptography. Post-quantum encryption safeguards digital data in the quantum age.
Read More:- Evaluating Cyber Security Companies: Pros and Cons
Conclusion
In conclusion, cybersecurity intruders and threats must be understood to protect digital assets and ensure organisation resilience against emerging cyber threats. Cybersecurity experts can prevent, mitigate, and respond to cyber assaults by understanding invader motives, tactics, and methods. Advanced technologies like AI and machine learning, together with legal and ethical standards, let organisations protect against cyber attacks while meeting regulatory obligations.
The rise of IoT devices, quantum computing, and hostile AI will impact cybersecurity in the future. Adapting to these developments needs ongoing learning, innovation, and collaboration across business, academia, and government agencies. In a linked and dynamic digital world, organisations may limit cyber threats by taking a proactive and forward-thinking approach to cybersecurity.







Anshul Goyal
Group BDM at B M Infotrade | 11+ years Experience | Business Consultancy | Providing solutions in Cyber Security, Data Analytics, Cloud Computing, Digitization, Data and AI | IT Sales Leader