Next-Generation Cybersecurity Trends
Cybersecurity is evolving with groundbreaking trends like AI, blockchain, and zero-trust models, as technology advances. With the rise of sophisticated cyber threats, these innovative solutions are essential to safeguarding organizations in today’s complex digital landscape.

Next-Generation Cybersecurity Trends
Table of Contents
- Why Next-Generation Cybersecurity is Crucial
- Key Next-Generation Cybersecurity Trends
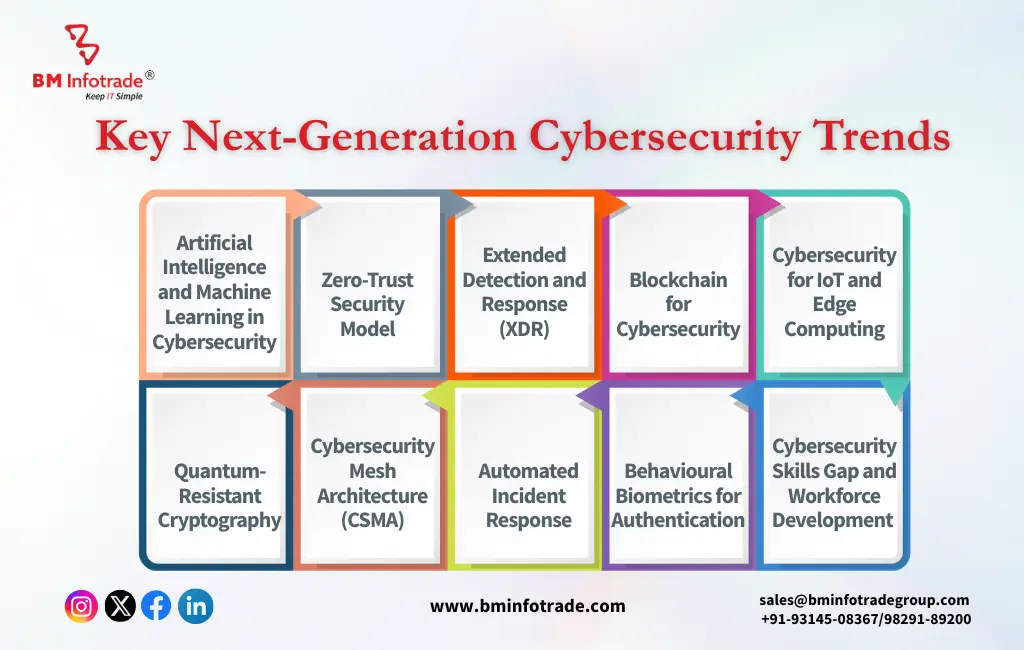
- 1. Artificial Intelligence and Machine Learning in Cybersecurity
- 2. Zero-Trust Security Model
- 3. Extended Detection and Response (XDR)
- 4. Blockchain for Cybersecurity
- 5. Cybersecurity for IoT and Edge Computing
- 6. Quantum-Resistant Cryptography
- 7. Cybersecurity Mesh Architecture (CSMA)
- 8. Automated Incident Response
- 9. Behavioural Biometrics for Authentication
- 10. Cybersecurity Skills Gap and Workforce Development
- Preparing for the Next Generation of Cybersecurity
- Conclusion
The evolution of technology has developed new prospects for doing things but has equally opened doors to more advanced cyber threats. Consequently, Cybersecurity is becoming more advanced. The focus on next-generation cyber security trends is powered by newer technologies such as AI, machine learning, blockchain, zero trust architecture and others. In this article, we look into these trends, their implications as well as how organizations can be flexible enough to guarantee themselves stronger cyber protections.
Why Next-Generation Cybersecurity is Crucial
There have been a lot of developments lately in moving towards remote work, cloud computing, IoT devices, and 5G connectivity which have affected broadening the attack surface for cybercriminals. Orchestrated assaults targeting the organizations’ cyber systems have been reported, ranging from ransomware, phishing, attacks on the supply chain, and even zero-day vulnerabilities. Because attackers use advanced strategies, traditional security measures can no longer be relied upon and appropriately effective measures must be devised.Endpoint protection example.
Read More: NAT and Firewall Explained: Key Differences and Their Role in Network Security
Key Next-Generation Cybersecurity Trends
1. Artificial Intelligence and Machine Learning in Cybersecurity
AI and ML are not revolutionizing industries anymore, they are now must-have use cases across various areas like cybersecurity. The reason is, that these technologies help organizations look through mountains of data in real-time which in turn allows faster threat detection and response to these threats.
Benefits:
- 1. Finding deviations and forecasting the attempted threats.
- 2. Automating algorithms and reducing human-based manual repetition.
- 3. AI-based automation to lessen the resolution time for the incidents.
Real-World Example: Companies like Darktrace have created cybersecurity platforms that use AI to identify unusual traffic flow within networks, triggering alerts for potential breaches.
2. Zero-Trust Security Model
The concept of zero-trust revolves around the notion of not fully trusting anyone inside or outside the network and verifying every request that is made. ZT architecture and approach enhance security within today's complexities, especially peripheral ones.
Key Features:
- 1. Every device, user and system is continuously authenticated.
- 2. Access Policies are implemented step by step at varying levels.
- 3. Minimize lateral movement by enabling micro-segmentation.
Adoption: For instanc,e Google has introduced zero-trust frameworks e.g. BeyondCorp.
3. Extended Detection and Response (XDR)
Extended detection and response (XDR) is an advanced expansion of endpoint detection and response (EDR). It offers a comprehensive perspective and responds to threats across end users, networks and even cloud environments.
Advantages:
- 1. Coverage across multiple security layers.
- 2. Complex threats are identified and neutralised faster.
- 3. Ready to integrate with existing tools for operational continuity.
Future Potential: Adopt multi-cloud solutions, XDR will be the critical component of complete security.
4. Blockchain for Cybersecurity
What sets blockchain technology apart is the incredible level of data integrity and transparency which makes it a robust tool in cybersecurity.
Applications:
- 1. Managing identities securely.
- 2. Battling fraud in online transactions.
- 3. Decentralized information storage to ensure safeguards against threats.
Example: Civic is one of the blockchain-based identity solutions that eliminates the need for an intermediary by offering safe and decentralized means of identifying users and businesses.
Read More: Understanding Blockchain: A Revolution in Digital Transactions
5. Cybersecurity for IoT and Edge Computing
The expansion of IoT and edge computing has come with new weaknesses. These new distributed networks need new cybersecurity strategies to keep them secure.
Challenges:
- 1. No unified standard security protocols for IoT devices.
- 2. Difficulty in providing security due to low processing resources.
Solutions:
- 1. Use of less resource-intensive encryption methods.
- 2. Automatic threat analysis and response via AI edge security solutions.
6. Quantum-Resistant Cryptography
The emergence of quantum computing could make traditional encryption less reliable. The quantum cryptography postulates the development of encryption techniques that can resist quantum attacks.
Current Efforts:
- 1. NIST and other organizations are working on the standardization of quantum-resistant algorithms.
- 2. Use of hybrid cryptographic methods to mitigate risks during adoption.
7. Cybersecurity Mesh Architecture (CSMA)
CSMA is a decentralized security framework which protects people's identities, endpoints and applications regardless of their location.
Features:
- 1. Aggregates multiple security technologies into an inclusive solution.
- 2. Allows for consistent enforcement of policies across environments.
Importance: Considering current work models are moving towards hybrid, this allows CSMA to be scalable and flexible in its security.
8. Automated Incident Response
Given that cyber attacks are on the rise and are growing in sophistication, automated incident response emerges as an important aspect of next-generation cybersecurity.
How It Works:
- 1. Artificial intelligence studies occurrences and decides on a suitable countermeasure.
- 2. Cuts down the attack response time reducing the extent of the damage caused by the threat.
Tools in Use: Solutions such as SOAR embed built-in workflows to improve handling of the incidents.
9. Behavioural Biometrics for Authentication
Passwords seem to be gradually being replaced by behavioural biometrics as they enable users to act without relying on any factors. These types of systems are able to authenticate users by analyzing how they type move the mouse or touch the screen.
Advantages:
- 1. Decreases the dependence on fixed passwords.
- 2. Improves the level of security by making cheating very hard.
Future Applications: further security layers can be provided by embedding behavioural biometrics within multi-factor authentication.
10. Cybersecurity Skills Gap and Workforce Development
The increasing need for professionals in the security industry has encouraged the existence of a skills gap in most regions which needs to be filled to address the challenges of tomorrow.
Initiatives:
- 1. Upgrading Sessions and certifications like CISSP and CEH.
- 2. Enhancement of collaboration between the education sector and the business sector.
Future Outlook: Filling in the skills gap will allow businesses to be active against the new threats which may arise.
Preparing for the Next Generation of Cybersecurity
While these tendencies seem to dominate the narrative regarding the future of cybersecurity, threat mitigation should be fully immersed within a chain of defined actions:
1. Invest in Advanced Technologies
Implementing systems such as artificial intelligence, blockchain technology, and XDR offers enormous increased benefits for security measures, as well as optimization of general processes.
2. Implement a Zero-Trust Framework
The shift towards a zero-trust framework should be embraced in order to manage the challenges associated with a hybrid model of work.
3. Focus on Employee Training
Training employees with cybersecurity policies and practices increases the chance of minimizing human error which may in turn compromise security.
4. Collaborate with Industry Partners
Alliances with cybersecurity vendors and membership in one or several threat intelligence-sharing organizations can be beneficial.
5. Stay Compliant with Regulations
Protection from prosecution for the majority of the clients is based on the principles of compliance with industry standards and legal frameworks such as the GDPR, CCPA, and ISO 27001.
Read More: What is Ransomware? How It Works and Steps to Protect Your Data
Conclusion
The sphere of cybersecurity is continuously expanding and changing due to the rapid development of technology and the enhanced competence of actors threatening cyberspace. Some of the next-generation cybersecurity trends which include but are not limited to, AI-enabled threat detection, security systems based on blockchain technology, and zero-trust architectures, are worth considering if an organization wishes to ensure that its critical resources are protected in the 21st century. By integrating these advanced tools, organizations can not only protect their networks but also prepare for the coming challenges.







Anshul Goyal
Group BDM at B M Infotrade | 11+ years Experience | Business Consultancy | Providing solutions in Cyber Security, Data Analytics, Cloud Computing, Digitization, Data and AI | IT Sales Leader