How to Spot a Phishing Attack in Under 10 Seconds
Learn how to quickly identify phishing attacks in under 10 seconds by spotting common red flags like suspicious links, fake sender details, and urgent messages designed to steal your data.

How to Spot a Phishing Attack in Under 10 Seconds
Table of Contents
In the breakneck world of the 21st-century online, more than ever before, it is necessary to be safe on the Internet. Since the need to detect phishing attacks is now an everyday requirement, learning how to recognize phishing emails will help you to avoid making expensive errors. Cybersecurity awareness in Oman: Since cybersecurity has been increasing in Oman, it is important to create awareness in Oman to secure personal and business data. As reported recently, phishing involves 33% of security incidents associated with the cloud. This is a guide by BM InfoTrade Pvt. Ltd., which will demonstrate to you easy and quick ways of identifying a phishing attack.
Contact:- sales@bminfotradegroup.com +919314508367 +919829189200
Understanding the Basics of Phishing
Phishing is another trick that cybercriminals often use to impersonate credible bodies that gain them access to vulnerable data. Phishing in Cyber Threats 2026 is an IT threat that has developed AI-driven attacks, which are more difficult to identify. According to statistics, a 1,265 percent growth in phishing by generative AI was made. This would mean an increase in risks to individuals and businesses in Oman, as phishing attacks have already been witnessed in millions in early 2026.
To combat this, start with quick visual cues. Here's an example of a typical phishing email:
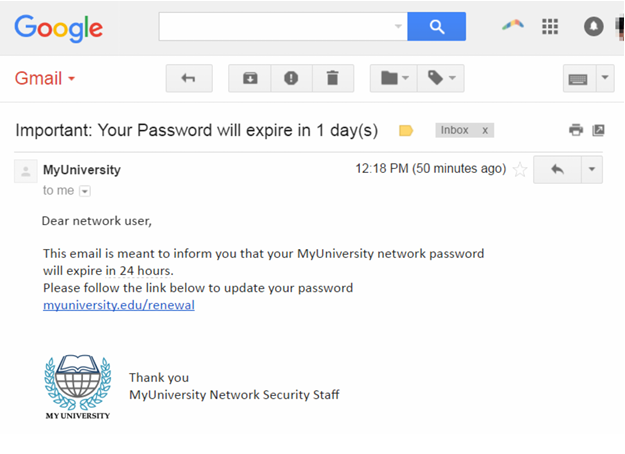
Email Security Tips: Quick Checks in Seconds
Let's break it down into fast, actionable steps. Aim to spend no more than 2-3 seconds on each.
1. Check the Sender's Email (2 Seconds): Authoritative emails belong to official domains. When the address appears suspicious, such as support@amaz0n.com rather than “amazon.com”, the deal is not genuine. It is fundamental in the process of detecting phishing emails.
2. Scan for Urgency or Threats (2 Seconds): The panic created by phishing usually mimics that the accounts will be suspended. or "Act now!" You are hardly ever pressured by real companies.
3. Hover Over Links (2 Seconds): It is advisable to hover over your link before clicking to get the actual URL. In case it is not the same as what is displayed, delete the email.
4. Look for Grammar Errors (2 Seconds): Bad spelling or inept phraseology speaks volumes. Professional bodies have their messages edited.
Here's another example highlighting these issues:
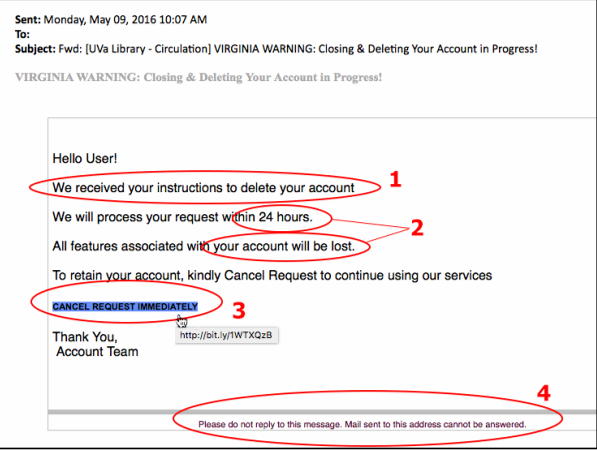
Examples of Phishing and Scam Emails | UVA Information Security And one more for reference:

These email security tips can help you avoid falling victim.
Phishing Prevention for Businesses in Oman
In the case of businesses, business phishing prevention goes beyond personal care. Introduce employee education, particularly in October, which is National Cyber Security Awareness Month. Block threats with such tools as firewalls and antivirus software from trusted providers. In Cyber Threats 2026, supply chains and ransomware are advanced attacks on businesses.
Your IT Security Checklist for Daily Protection
Follow this simple IT security checklist:
● Activate the 2-factor authentication of every account.
● Filter email to mark suspicious messages.
● Always upgrade programs to counter exploits.
● Report phishing suspicion to such agencies as CERT-In in Oman.
This checklist works well together with business phishing prevention and provides full protection.
Conclusion: Stay Safe with BM Info Trade
The art of these tricks will enable you to deal with phishing attacks with confidence. It should be remembered that cybersecurity awareness in Oman is increasing, and some proactive measures are crucial.
Need to bring your security to a new level? We are specialists in security solutions relating to cybersecurity, 24x7 SOC, and antivirus systems at BM InfoTrade Pvt. Ltd. Register an account and get access to individualized dashboards, instant threat notifications, and buy high-quality services. To protect your business, visit bminfotrade.com/ or contact us to get started.
Contact:- sales@bminfotradegroup.com +919314508367 +919829189200
Frequently Asked Questions (FAQs)
1. What is the first step in identifying phishing emails?
Begin by validating the email domain of the sender. Unless it is similar to the official one, it is probably a scam. This is a fast inspection that only requires a few seconds and is crucial to safety.
2. How does cybersecurity awareness in Oman help against phishing?
Education of users about threats is made through such campaigns as National Cyber Security Awareness Month. In Oman, where attacks are on the increase, awareness would mitigate risk through safe online behaviors.
3. What are the key email security tips for beginners?
Never click on suspicious links, check on sender information, and install antivirus software. Such fundamentals ward off the majority of phishing without the use of sophisticated technology.
4. Why is phishing prevention for businesses important in Cyber Threats 2026?
Companies are victims of targeted attacks resulting in breaches of data. Risks can be reduced by 90 percent through training staff and firewalls, which protect operations.
5. What's included in a basic IT security checklist?
Add frequent updates, tough passwords, and scanning of email. Include multi-factor authentication in order to prevent unauthorized access.
Contact:- sales@bminfotradegroup.com +919314508367 +919829189200


![Cloud Licensing and Compliance Made Easy [All-in-One Bundle]](https://bminfotrade.com/assets/upload/blog/21851766642757.png)


Anshul Goyal
Group BDM at B M Infotrade | 11+ years Experience | Business Consultancy | Providing solutions in Cyber Security, Data Analytics, Cloud Computing, Digitization, Data and AI | IT Sales Leader