Concepts of Cyber Security: Protecting Information.
Explore the fundamental concepts of cyber security aimed at protecting your information from various threats. This guide covers essential strategies and best practices to enhance your security posture.

Concepts of Cyber Security: Protecting Information.
This hyper-connected digital world where information travels freely and transactions happen at the speed of light requires the safety of critical data and systems. Today, cyber security is essential to the safety and integrity of our digital infrastructure. This article explores the basics of cybersecurity and how they protect data in the digital age.
Digital innovations have made our lives easier and more efficient. The digital revolution has many perks, from online banking and e-commerce to social networking and telecommuting. However, this digital interconnection has exposed us to many cyber hazards, from harmful software to sophisticated hacker operations.
Cyber attacks can cause financial losses, reputational damage, and national security dangers. Global organizations and small businesses alike face ongoing threats to their digital assets, making cybersecurity a top priority.
This blog will teach readers about cyber security basics and give them the tools to protect their data. Cybersecurity's progress, the threat landscape, and key principles like the CIA triangle (confidentiality, integrity, and availability) and defense will be examined.
Table of Contents
Understanding Cyber Security
Cybersecurity involves methods, technologies, and processes that safeguard digital systems, networks, and data from unauthorized access, modification, and destruction. The entire method protects information assets from malware, phishing attempts, and data breaches.
Cyber security covers many areas, including:
- Network Security: Security of communication lines and infrastructure that enable data flow between organizations.
- Endpoint Security: Cybersecurity for PCs, cellphones, and tablets.
- Data security: protecting sensitive data throughout its lifecycle.
- Application security: Preventing hostile actors from exploiting software applications.
- Cloud Security: Cloud security protects cloud-hosted data and applications from unauthorized access and breaches.
- Physical security: protecting data centers, server rooms, and other vital infrastructures.
Read More: Cyber Security: Importance, Types, Tips, and Examples?
Evolution and Importance
Cyber threats are becoming more sophisticated and frequent; thus, cyber security has changed quickly. Cybersecurity began with perimeter defense, using firewalls and antivirus software to combat external threats.
However, as cyber threats have become more complicated and focused, cyber security has become more proactive and holistic. Cybersecurity nowadays emphasizes threat intelligence, risk assessment, and real-time monitoring to detect and respond to cyberattacks.
Cybersecurity is crucial since a cyberattack can be disastrous. Cybersecurity incidents can cause long-term financial losses, regulatory penalties, reputational damage, and legal liability.
Cyber security is more important than ever as companies use digital technologies to do business and provide services. Organizations may defend their assets, reputation, and customer and stakeholder trust by investing in cyber security.
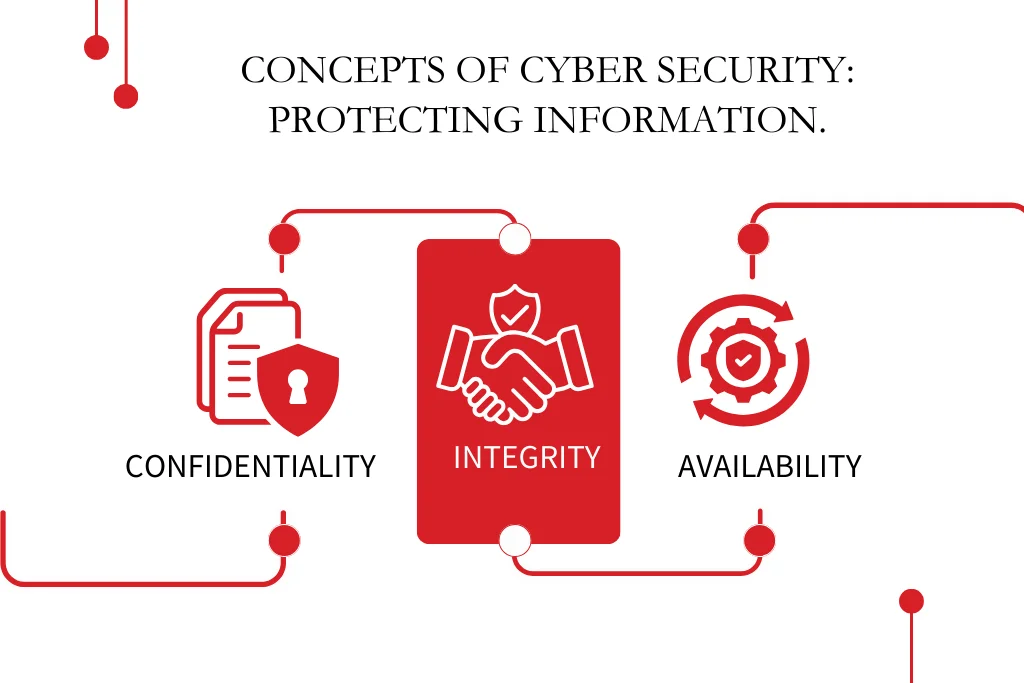
Key Goals
The CIA trio summarises cyber security's main goals:
- Confidentiality: Protecting sensitive data from unauthorized access.
- Integrity: Preventing data tampering to maintain accuracy.
- Availability: Data and systems must be available and working without disturbance or downtime.
Cyber security goals beyond the CIA triad include:
- Authentication: Users and devices are authenticated to prevent unauthorized access.
- Authorization: Granting user roles and permissions-based access.
- Non-repudiation: Ensure no one can refute their conduct or transactions.
- Resilience: Redundancy, backups, and disaster recovery strategies build cyber resilience.
Threat Landscape
Types of Cyber Threats
Malware:
- Definition: Malicious software that invades, damages, or steals data from computers.
- Examples: Computer viruses, worms, Trojans, ransomware, and spyware.
Phishing:
- Definition: Tricking people into giving over passwords or financial information.
- Examples: Spear, SMS, voice, and email phishing are examples.
Distributed Denial of Service:
- Definition: Coordinated attacks that overload a network, server, or website with traffic, blocking legitimate users.
- Examples: Amplification attacks (DNS, NTP) and botnet-based DDoS attacks.
Inner Threats:
- Definition: Threats from employees who misuse their access credentials to damage security.
- Examples: Internal enemies, incompetent workers, third-party contractors.
Social Engineering:
- Definition: Psychological manipulation to get someone to reveal secret information or take security risks.
- Examples: Pretexting, baiting, tailgating, quid pro quo.
Impact of Cyber Threats
- Financial losses via theft, fraud, or extortion.
- Negative reputational impact on customers, partners, and stakeholders.
- Data protection law violations result in fines, litigation, and sanctions.
- Operations interruption: Downtime, productivity losses, and business disruption.
- The theft or unauthorized disclosure of proprietary information, trade secrets, and intellectual property.
Real-World Examples
WannaCry: Ransomware
May 2017.
Impact: Infected hundreds of millions of computers globally, disrupting and costing money.
Method: Used a Windows SMB protocol vulnerability to spread and encrypt files, requiring ransom.
Equifax Data Breach:
July 2017.
Impact: Leaked 147 million consumers' names, Social Security numbers, and credit card information.
Method: Exploited Apache Struts vulnerability to access Equifax's systems and steal data.
NotPetya Cyberattack:
In June 2017,
Global organizations lost billions of dollars due to disruptions.
Spread quickly through infected software updates, encrypting files, and crippling systems.
Fundamentals of Cyber Security
Confidentiality, Integrity, and Availability (CIA Triad)
Confidentiality:
Secures sensitive data for authorized users or systems.
Through encryption, access controls, and data classification.
Integrity:
Maintains data integrity by preventing unauthorized changes.
Managed by checksums, digital signatures, and file integrity.
Availability:
Makes sure data and systems work when needed, without interruption.
Redundancy, fault tolerance, and disaster recovery are used.
Defense in Depth
Layered Security:
- Protects against various cyber threats with numerous layers of defense.
- Network firewalls, IDS, antivirus, and endpoint encryption are examples.
Least Privilege:
- Reduces user rights to the minimum needed for work.
- Restricting sensitive resource access mitigates security breaches.
Patch Management
Regular updates:
- Updates software, operating systems, and firmware with security fixes.
- Fixes vulnerabilities and minimizes cyberattack risk.
Scan for vulnerabilities:
- System and application weaknesses are identified and assessed.
- Allows proactive vulnerability correction before exploitation.
Encryption
Encrypting Data:
- Generates ciphertext from plaintext using cryptographic techniques.
- Unreadable to unauthorized outsiders protects data confidentiality.
TLS: Transport Layer Security
- Encrypts client-server data for internet communication.
- Uses HTTPS for safe web browsing.
Security Awareness Training
Staff Education:
- Increases awareness of cyber dangers, phishing assaults, and security best practices.
- Helps staff spot and report questionable activity.
Simulations of Phishing:
- Simulates real-world phishing assaults to assess staff awareness and response.
- Helps increase security and raise awareness.
Incident response and management
Identifying incidents:
- Monitors, logs, and analyses network and system activities to detect and confirm security incidents.
Mitigation and containment:
- Isolates impacted systems, disables compromised accounts, and implements temporary remedies to mitigate security problems.
Forensic Analysis:
- Determines security events' causes, gathers information and draws conclusions to prevent them.
Cyber Security Measures and Best Practices
Strong Passwords and Authentication
Complex Passwords:
- Encourage strong, complicated, brute-force-resistant passwords.
- Combining capital, lowercase, digits, and special characters is advised.
MFA: Multi-factor authentication
- Security is improved by requiring numerous verifications before accessing accounts or systems.
- Usually requires a password, security token, or biometric data.
Secure Network
Firewalls:
- Network traffic should be monitored and controlled by perimeter firewalls.
- Set firewall rules to allow or block traffic based on security policies.
IDPS: Intrusion detection and prevention
- Check network and system activity for malicious or policy violations.
- Block or notify administrators of questionable activity automatically.
Secure Endpoints
Antivirus/Antimalware:
- Endpoints need antivirus and anti-malware software and regular updates.
- Scan and eliminate malware to avoid infections and data breaches.
Endpoint Encryption:
- Endpoint data should be encrypted to prevent theft or loss.
- Use full-disk or file-level encryption for organizational needs.
Data Backup and Protection
Classifying Data:
- Classify sensitive and organizationally important data.
- Secure and restrict data access depending on classification.
Backup data regularly:
- Create regular backups of key data and systems.
- For data loss or system failure, store backups off-site in secure locations.
Security Awareness Training
- Inform staff on phishing and how to spot suspicious emails, links, and attachments.
- Show common phishing methods and red flags.
Social Engineering Awareness:
- Train staff to spot and avoid cyberattacker social engineering.
- Stress the significance of confirming sensitive information or access credentials.
incident response and management
Incident Response Plan:
- Create and maintain a security incident response strategy including roles, responsibilities, and processes.
- Set escalation, communication, and incident classification criteria.
Consistent Testing and Exercise:
- Tabletop exercises and simulated incident response drills can test the incident response plan.
- Post-exercise debriefings and evaluations reveal flaws and growth opportunities.
Compliance and Regulations
GDPR (General Data Protection Regulation)
Data Protection Principles:
- Organizations must process personal data legally, fairly, and transparently.
- Mandates data acquisition for specific, legal objectives with data reduction and storage time limits.
Data Subject Rights:
- Allows individuals to view, correct, and delete their data.
- Demands express consent for data processing and data portability.
The HIPAA law
PHI: Protected Health Information
- Sets EHR and sensitive health information protection guidelines.
- Covered entities and business associates must protect PHI using administrative, physical, and technical measures.
Required Breach Notification:
- Ensures affected persons, HHS, and the media are notified of PHI breaches.
Payment Card Industry Data Security Standard
Protecting Cardholder Data:
- Specifies payment card data security during transmission, processing, and storage.
- Sets network segmentation, encryption, access, and vulnerability management controls.
Verifying security and compliance:
- Regular security testing and assessments are needed to verify PCI DSS compliance.
- Include annual assessments, penetration testing, and periodic vulnerability.
Another Regulatory Framework
SOX:
- Regulates financial reporting and corporate governance to prevent accounting fraud and safeguard investors.
- Regulates financial data access, integrity, and retention.
FISMA: Federal Information Security Management Act
- Security guidelines for federal government computer systems and sensitive data.
- Federal agencies must create, implement, and manage information security.
Compliance Issues and Considerations
Complexity and Range:
- Managing numerous regulatory regimes is difficult and resource-intensive for international companies.
- Must carefully interpret regulatory requirements and follow organizational policies.
Constant Monitoring and Reporting:
- Security controls and activities must be monitored, assessed, and reported continuously to ensure compliance.
- Organizations must document, audit, and file regulatory compliance.
Emerging Trends and Technologies in CyberSecurity
Artificial Intelligence and Machine Learning
Threat Detection and Prediction:
- Analyzing massive data sets with AI and machine learning algorithms to uncover cyber threat tendencies.
- Provides proactive threat identification and prediction to reduce hazards before they arise.
Analytics on behavior:
- Using AI-powered behavioral analytics to identify suspicious user behavior and insider risks.
- Improves suspicious activity and behavior detection.
Blockchain technology
Decentralized Security:
- Using blockchain's decentralized design to improve supply chain management and identity verification security.
- Data manipulation and fraud are reduced via tamper-proof records and open audit trails.
Smart Contract:
- Smart contracts on blockchain networks automate and enforce secure transactions and agreements.
- Reduces disputes and fraud by eliminating intermediaries and ensuring confidence.
IoT Security
Device Verification/Encryption:
- Securing IoT devices and communications using robust authentication and encryption.
- Blocks unauthorized access, data breaches, and device manipulation.
Security Frameworks:
- Create and implement industry-wide IoT security standards and frameworks.
- Provides security best practices for IoT device manufacturers, service providers, and end users.
Cloud Security
Cloud-Native Security:
- Protecting cloud data and workloads with cloud service provider-built security tools and controls.
- Contains encryption, access limits, and automatic threat detection.
Zero-Trust Architecture:
- Zero-trust cloud security, where identity verification and least privilege are used to access resources.
- Reduces insider risks and lateral mobility by never assuming trust and verifying access.
Issues and Considerations
Integrating Complexly:
- Integrating new technologies into IT settings requires careful preparation and execution.
- Security solution adoption requires compatibility, interoperability, and scalability.
Cyber Skills Gap:
- Cyber security specialists who can grasp and execute new technologies are in limited supply.
- Building and retaining a skilled workforce requires training and professional development.
Cybersecurity Challenges
Cyber Threat Complexity
Sophistication:
- Advanced tools like artificial intelligence and encryption are helping cybercriminals hide.
- To respond to changing threats, cyber security defenses must evolve.
Variability:
- Malware, phishing, ransomware, and insider threats make it difficult to defend against all attack vectors.
- Needs a multilayered cyber security strategy to combat various threats.
Lack of Cybersecurity Experts
Skills Gap:
- Cyber security personnel with threat detection, incident response, and secure coding skills are few.
- Increases vulnerability as organizations struggle to fill cyber security responsibilities.
Attracting and keeping:
- Competition from other businesses, pay expectations, and restricted career growth prospects make cybersecurity talent recruitment and retention difficult.
- To retain competent workers, companies must invest in training and development.
Rapidly changing tech landscape.
Complexity:
- Complexity and variety in IT environments make security risk visibility and control difficult due to constant technological innovation.
- Cybersecurity strategies must be monitored, assessed, and adjusted to address new threats and vulnerabilities.
Infrastructure and Legacy Systems:
- Due to their vulnerabilities and lack of contemporary security controls, legacy systems and infrastructure offer security concerns.
- Organizations must combine IT modernization with legacy system integration and migration.
Threats from inside
Evil Insiders:
- Malicious insiders can steal data, destroy systems, or spy as they abuse their access credentials.
- To detect and mitigate insider threats, it needs proactive monitoring, user behavior analytics, and access controls.
Negligent Workers:
- Employee mistakes like phishing schemes or data mismanagement can potentially cause security issues.
- Promoting security awareness and compliance requires regular security awareness training and education.
Conclusion
In conclusion, cyber security fundamentals are essential for digital data protection. To protect assets and preserve stakeholder trust, organizations must prioritize cyber security as the threat landscape evolves and digital technologies become more prevalent. Organizations may reduce cyber threats by understanding confidentiality, integrity, and availability, implementing defense in-depth tactics, and using best practices like robust authentication and incident response planning. GDPR, HIPAA, and PCI DSS compliance is vital for legal and regulatory compliance and data protection and privacy. As new technologies change cyber security, organizations must stay watchful, adapt to new problems, and invest in the resources and knowledge needed to stay ahead of developing threats. In an increasingly interconnected world, cyber security must be proactive and holistic to navigate the digital landscape and secure information assets.







Anshul Goyal
Group BDM at B M Infotrade | 11+ years Experience | Business Consultancy | Providing solutions in Cyber Security, Data Analytics, Cloud Computing, Digitization, Data and AI | IT Sales Leader