Cyber Security; Importance, Types, Tips, and Examples?
Cyber security is essential, as we daily share our information online. The main work of Cyber Security is to protect our system from unauthorized users.

Cyber Security; Importance, Types, Tips, and Examples?
Table of Contents
Cyber security is essential in today's world, where we daily share our information online. This helps us protect our networks and data. The main work of Cyber Security is to protect our system from unauthorized access by hackers or Mischievous attackers.
More than 3 Billion fake emails were sent on a daily basis, to attack small and medium size businesses. To avoid these kinds of attacks you should have some basic knowledge about cyber security.
Read More : Software-World of Technology: Evolutionary History, types and application.
Top reasons why cyber security is important
Over 43% of cyber attacks targeted small businesses that don’t have proper information on cyber security or lack basic knowledge. These cybercrimes cost businesses more than $ 4.45 million in a year for the last 3 years. Also, most healthcare industries suffer from cyber attacks.
In all these cyber crimes 52% times human errors and system failures are responsible for data security breaches.
So you must understand the importance of cyber security.
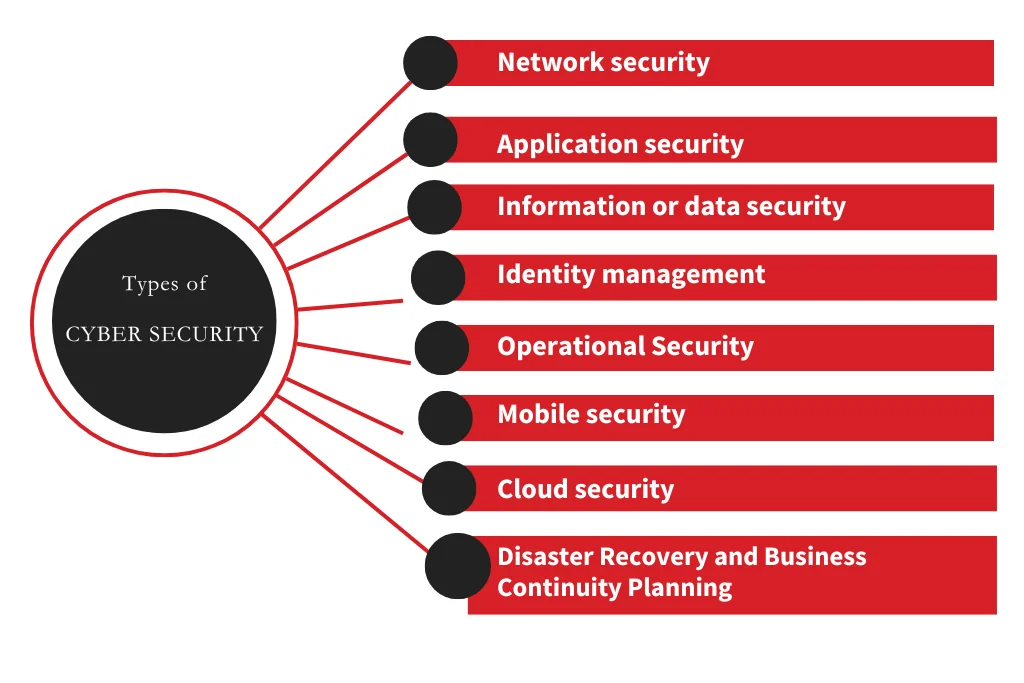
Types of cyber security that are commonly known.
Understanding types of cyber security helps us to know what kind of actions we should take to avoid cyber crimes. Let’s start with the most commonly known types of cybersecurity. 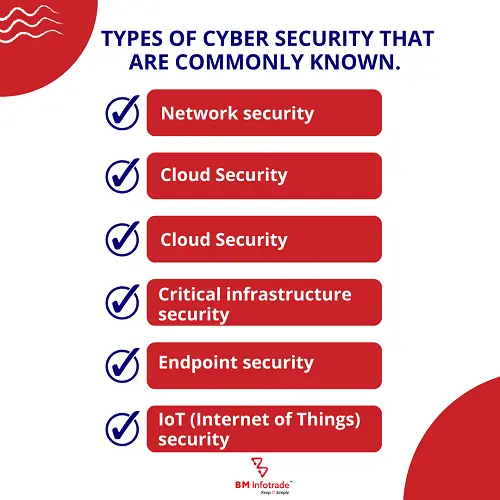
Network security
This cyber security type helps in protecting online systems, and networks.
Network security is important because most businesses use networks in their work. If network security is not properly implemented then it can be fatal. You can use a Firewall, or VPN (Virtual Private Network) in your network security.
You can also consider using Endpoint Security, IPS (Intrusion Prevention System), and IDS (Intrusion Detection System).
These tools can help you with network security. You should also be aware of using Free networks and public wifis because they don’t have security in them.
Application security
This security is to prevent unauthorized access and data breaches in applications. Most weaknesses are prevented during the development stages. But still, some vulnerabilities slip through them.
Application security is a good way to identify flaws. It can also give alerts to developers to fix issues in an application. Another benefit of using application security is that it protects web applications.
Web application security is a part of the application security. Web applications are constantly getting cyber attacks, and to avoid them, we need web application security.
It uses exceptional methods, tools, and ways to detect issues in software before anyone else can find them. It is to help small and medium-sized businesses so that they don’t face problems in the future.
Cloud Security
It helps us in protecting cloud-based systems and assets. Cloud security is necessary for data, infrastructure, and applications in the cloud.
Most Cloud service providers have security for their clients, they take all the security measures to prevent a cyber attack. However, you can also use third-party security methods and tools to protect your cloud system from disasters.
Critical infrastructure security
This is a special type of security in which we just don’t focus on digital systems and networks, we focus on infrastructure. Physical assets fall under the category of Critical infrastructure, which is very important to run digital systems.
In the United States, there is a concept of critical infrastructure known as CIP (Critical infrastructure protection). This concept is about preparation and response to incidents related to the Critical infrastructure of the nation.
Transportation, energy systems, water systems, public communications, food, and agriculture systems fall in the Critical infrastructure category.
Cyber attackers, aim to gain access to these infrastructures and unleash their attack. To avoid these types of situations we need Critical infrastructure security.
Read More : How cyber security works and the cost of cyber security.
Endpoint security
This is a process of securing and protecting endpoints like laptops, desktops, mobiles, and other devices that are connected to the corporate network.
These devices are most commonly used by hackers as an entry point in any business.
Every device or system we use can be used as an entry point, these endpoints are exploited to leak and steal data of an organization. Therefore, each and every device that is connected to the corporate network needs Endpoint security.
This Security gives a solution to this problem by examining files, when they enter. It compares them to a database of threat information stored in the Cloud.
Endpoint security can also provide security by application control. This can warn and stop users from accessing unsafe applications to avoid data leaks.
IoT (Internet of Things) security
This security is used to minimize vulnerabilities and secure IoT devices. IoT security focuses on the privacy of user data and helps IoT systems run smoothly.
It has three types of security measures, The first one is Network security which prevent unauthorized access and data leaks. Second is Embedded nano agents, Nano agents are tiny pieces of software that protect IoT (Internet of Things) devices directly on the devices themselves, ensuring their security. Third is Firmware assessment in which we evaluate the software that operates on IoT devices.
Cyber Security Tips you can use in your life
Cybersecurity is a very big word where you have to be very careful and cautious. But you can avoid most of the scams and cyber attacks in daily life just by following some tips.
-
Don’t click on links without thinking. First, inspect to ensure that the link you are opening is safe. To do that you have to check if this link comes from an authorized source or not.
-
You should use Two-factor authentication on your devices, by doing that you prevent attackers even if they get your password.
-
More than 3 billion fake emails are sent in one day, these emails are phishing scams, they try to be someone the recipient knows. You should avoid these kinds of emails.
-
Be updated to the latest versions of software because many software resolves their security issues in their new versions.
-
Always connect to a secure network and avoid public wifi or other unauthorized network.
-
You should always have a backup of your data it can be on the cloud or on a physical system. If your system gets hacked or data gets deleted you can always use your backup data.
Conclusion
In Conclusion, you should understand the importance of cyber security and have a basic knowledge of it. If you are a business you should consider having cyber security because there is no way to know when you get into a cyber attack. Having Cybersecurity can help you prevent data leaks, cyber-attacks, and unauthorized access.







Anshul Goyal
Group BDM at B M Infotrade | 11+ years Experience | Business Consultancy | Providing solutions in Cyber Security, Data Analytics, Cloud Computing, Digitization, Data and AI | IT Sales Leader