5 Types of Cyber Security: Protecting Your Digital Assets
Securing a computer network from unauthorized intruders who could be either targeted attackers or opportunistic malware is done through Network Security which means securing their networks.

5 Types of Cyber Security: Protecting Your Digital Assets
Table of Contents
In a world that continues to be more connected, digital assets should be protected with utmost care. For an individual or even a corporate group to protect sensitive information from the wrong intentions of other parties they recognize cyber security as an extremely vital tool. To safeguard against the ever-changing risks found within today’s digital environment it is important to know about the 5 Types of Cyber Security. In this blog, we will discuss these five critical types and how they help you guard your digital realm.
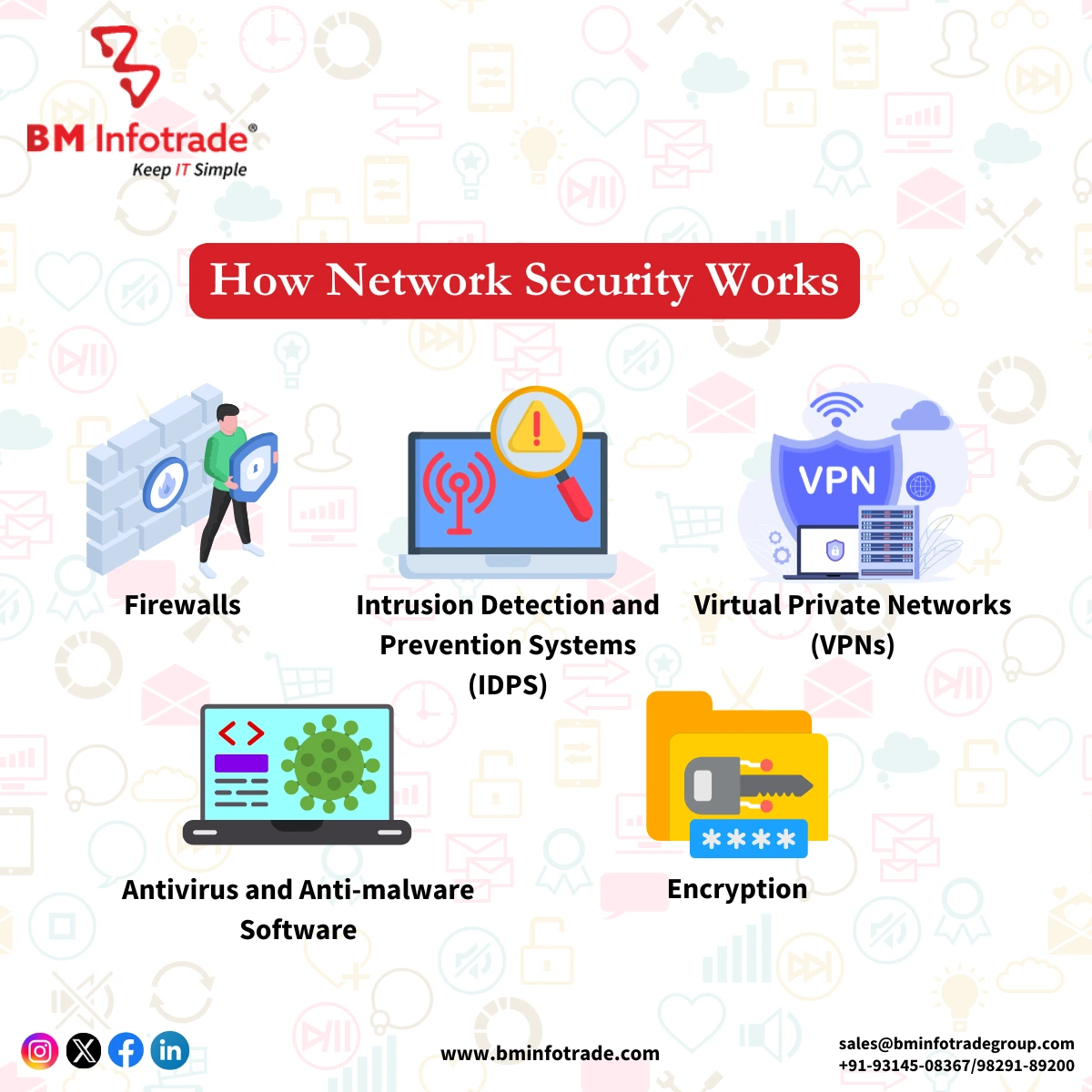
Network Security
Securing a computer network from unauthorized intruders who could be either targeted attackers or opportunistic malware is done through Network Security which means securing their networks. This entails implementing hardware and software technologies for preventing unauthorized access, misuse, or alteration of the network.
Key Aspects of Network Security:
-
Firewalls: They are a barrier between trusted internal networks and untrusted external networks.
-
Intrusion Detection Systems (IDS): Monitor traffic on the network for any suspicious activities.
-
Virtual Private Networks (VPN): Provide secure remote access into the network.
Network Security is crucial in protecting the infrastructure that connects your devices together and ensures data transmission securely.
Application Security focuses on making sure that software tools and gadgets remain free from harm. Compromised applications can become an entry point for cyber criminals hence security measures need to be put throughout software development life cycle.
Key Aspects of Application Security:
-
Encryption: It is meant to secure data by converting it into another form where it can only be understood if you have the decryption key.
-
Secure Coding Practices: This makes sure that vulnerabilities are reduced when developing software applications.
-
Regular Updates and Patches: These fix any loopholes in the software resulting in the avoidance of its manipulation.
By prioritizing Application Security, organizations can protect their software from being a gateway for attacks, thus safeguarding sensitive information held in them.
Information Security
Information Security, which is sometimes referred to as “InfoSec” is aimed at ensuring that data is available, kept confidential and remains without changes when it is in transit or stored. This type of security ensures sensitive information is handled securely, preventing unauthorized access or disclosure.
Key Aspects of Information Security:
-
Data Encryption: Unauthorized users cannot read the data.
-
Access Controls: Forbidding people within an organization from accessing or using particular details.
-
Data Backup and Recovery: In case of a breach this ensures that the lost information can be replaced.
Information Security is central to any cybersecurity strategy because it involves protecting unauthorized access to or breaches of data.
Cloud Security
Cloud Security has become vital in cyber security as cloud services continue to grow in adoption. It involves protecting data, applications, and infrastructures involved in cloud computing, ensuring that cloud-based assets are secure from threats.
Key Aspects of Cloud Security:
-
Data Encryption: Safeguarding personal information stored on the cloud.
-
Identity and Access Management (IAM): Manages resource access by different people in the cloud.
-
Compliance Management: Ensures compliance with industry regulations for providers who operate through clouds.
Cloud Security is necessary for organizations using cloud services since it guarantees them digital asset security while they remain in the clouds.
Endpoint Security includes securing individual devices such as computers, smartphones and tablets connected to a network. Cyber threats could enter through each endpoint hence there is a need to provide strong security measures around them.
Key Aspects of Endpoint Security:
-
Antivirus Software: These protect against malware attacks and viruses on devices.
-
Device Management: Controls and oversees the security of devices connected to the network.
-
Endpoint Detection and Response: It provides continuous monitoring and response against potential dangers on endpoints.
If there is a strong Endpoint Security in place, organizations can ensure that all devices accessing their network are secure thus reducing the risk of breaches.
Conclusion
It is important to understand the 5 Types of Cyber Security when developing a comprehensive cybersecurity strategy. Each type focuses on various aspects of digital protection to ensure that your networks, applications, information, cloud services, and endpoints are safe. In view of constantly changing cyber threats, keeping abreast with them as well as being proactive in efforts for cybersecurity will enable you protect your digital assets and maintain system integrity.







Anshul Goyal
Group BDM at B M Infotrade | 11+ years Experience | Business Consultancy | Providing solutions in Cyber Security, Data Analytics, Cloud Computing, Digitization, Data and AI | IT Sales Leader