DSPM versus CSPM: Key Differences and Choosing the Right Approach
Understand the key differences between DSPM and CSPM to choose the right approach for securing your cloud environments effectively.

DSPM versus CSPM: Key Differences and Choosing the Right Approach
Table of Contents
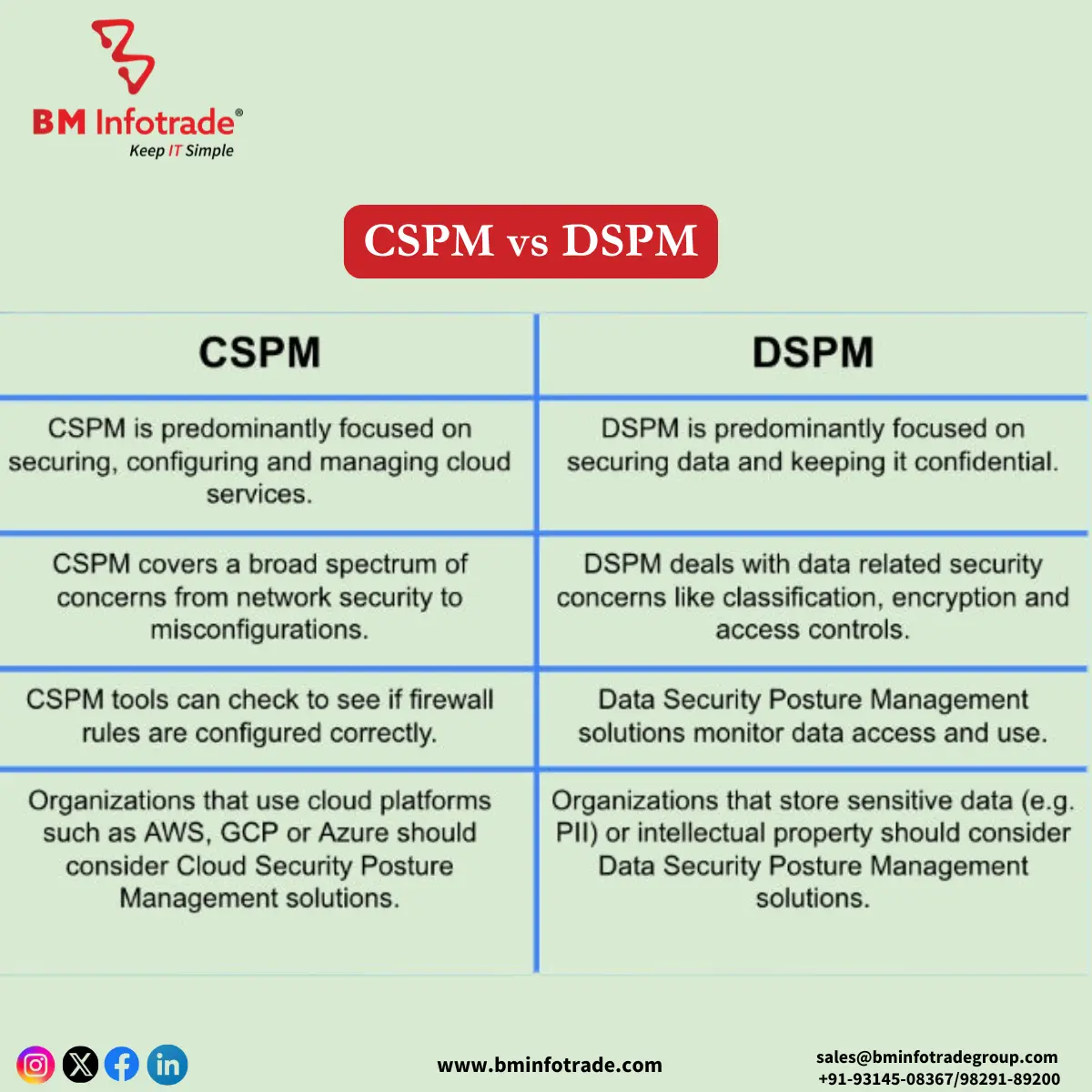
In recent years, many organizations have designed self-predictive tools for the security and compliance of their cloud deployments. Two popular tools in this space are DSPM (data security posture management) and CSPM (Cloud security posture management). Although both are meant to enhance security, the two features have different functions. The following article looks at the prominent features of DSPM and CSPM, including how they are implemented and what factors to consider when selecting the right strategy for your organization.
What is DSPM (Data Security Posture Management)?
DSPM focuses on organizations with large amounts of sensitive customer information within the cloud. It pinpoints where the data of concern resides, how exposed the data might be, and whether such data adheres to regulatory bodies and internal policies.
Key Features of DSPM
-
Data Discovery: Identifies sensitive information in multi-cloud and hybrid environments in an automated fashion.
-
Risk Analysis: Evaluate risks about data location and data accessibility.
-
Compliance Assurance: Enforces organisations protecting data as per GDPR, HIPAA or CCPA compliance.
-
Data Access Monitoring: Monitors the access to sensitive information including the appropriateness of that access.
DSPM is particularly important for companies that manage excessive volumes of sensitive data like banks or healthcare providers. The objective of its implementation is to make sure that sensitive information is properly secured and responsibly managed.
Read More:- What are Cloud Databases? Features, Benefits, and Use Cases
What is CSPM (Cloud Security Posture Management)?
CSPM (Cloud Security Posture Management) responds to the misconfigurations and security risks in the cloud environment by adopting a wider approach that ensures risk mitigation. It looks at the general security posture rather than at discrete data.
Key Features of CSPM
-
Configuration Management: Identifying, detecting, or bringing into correct use opted-into services by internal users and other properties such as VM.
-
Threat Management: Includes forecasting incidents and the attack vectors they may utilize.
-
Regulatory Control: Implements pre-checks for ISO 27001, ISO 31000, PCI DSS Secure configuration and others onto SaaS services.
-
Remediation: Provides numerous resolution measures and described actions to eradicate security flaws.
CSPM is the mechanism and way forward for organisations whose aim is to cut across all the possible changing approaches to create a stronger security perimeter. It prevents events of breaches that arise from oversights such as open sharp ports or too many permissive access control settings.
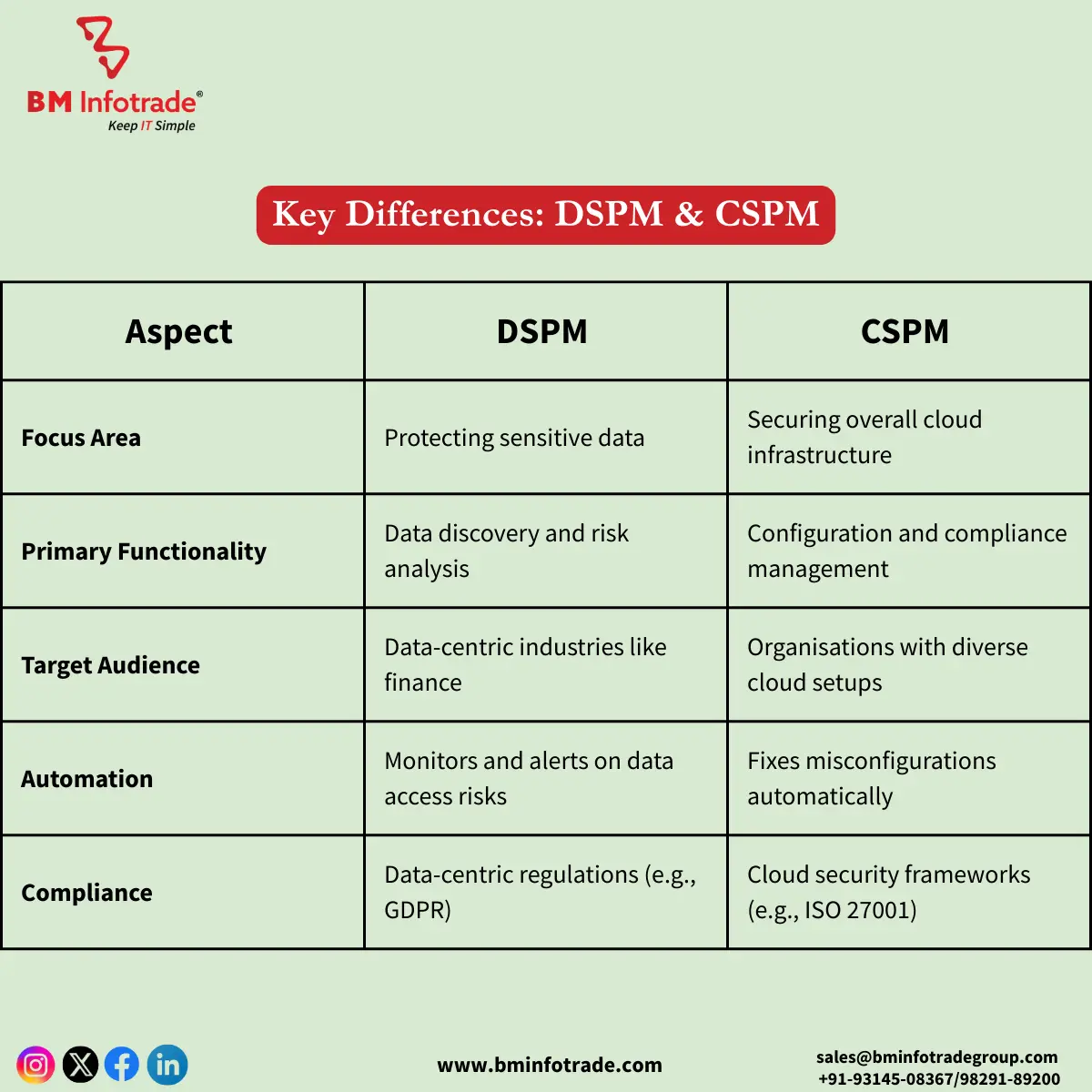
Key Differences Between DSPM and CSPM
While DSPM and CSPM share the goal of improving cloud security, their approaches and scopes differ significantly. Here are the main distinctions:
When to Use DSPM
-
Sensitive Data is a Priority: If your business manages numerous sensitive data,(like customer PII’s en masse) Health records or finance-related information, then in that case, DSPM is a necessity.
-
Regulatory Compliance: Sectors that are heavily regulated like GDPR or HIPAA will find it useful since DSPM is highly focused on data security and compliance.
-
Preventing Data Breaches: As DSPM is capable of access surveillance and abnormality detection it is a useful device for curtailing inside threats and data breaches.
When to Use CSPM
-
Comprehensive Cloud Security: For organizations that are using more than one cloud application (e.g. Amazon, Microsoft, Google), CSPM makes it easier for such organizations to have consolidated and secured infrastructures.
-
Avoiding Misconfigurations: Breaches occur due to cloud misconfigurations, which happen to be among the leading causes of breaches that occur. CSPM provides automatic diagnosis and remediation of these vulnerabilities and hence allows peace of mind whilst using the technology.
-
Cloud Infrastructure Protection: CSPM is a cloud security solution that provides protection and compliance with specific cloud security requirements. Automated compliance management was vital for enterprises with complex cloud architecture.
Can DSPM and CSPM Work Together?
DSPM and CSPM are not competitive, hence the short answer for both can work together in harmony. This integration is a strategy used together with CSPM to achieve strong and reliable multi-cloud security.
How They Complement Each Other:-
-
Integrative Perspective: DSPM gives the information concerning sensitive data whereas CSPM safeguards the infrastructure that contains this sensitive data.
-
Multilayered Security: While DSPM centres on the ‘what’ ( the data), and CSPM deals with the ‘where’ (the cloud infrastructure), there is security assurance.
-
Increased Compliance: They each assist respective organizations to achieve compliance with cloud-specific and data regulations.
Example Use Case
A financial services company could utilize the CSPM protection of multi-clouds while using DSPM specifically for customer financial data protection. This tool integration ensures data safety while enabling compliance with industry standards.
Choosing the Right Approach
In choosing between Two approaches, DSPM and CSPM, it is important to factor in the organizational needs, the cloud structure, and security concerns. Here are some factors to bear in mind:
1. Type of Data
-
If sensitive data is considered the core of your business model( health records,’ or financial affairs), then DSPM should not be polished.
-
If your company does not remain dependent on data services but rather offers global-enhanced operations, CSPM is effective for them.
2. Regulatory Standards
-
Governments across the globe have placed restrictions and guidelines on data (GDPR, HIPAA) calling for the need for DSPM.
-
Security measures and frameworks imposed for cloud services (PCI DSS, ISO 27001) call for CSPM.
3. Finance and Resources
-
Rarely adopting advanced tools, for example, DSPM solutions can be relatively cheap for small businesses usually focusing on data.
-
CSPM tools are well-suited for large companies that are handling complex environments within the cloud.
4. Organisational Objectives
-
Use DSPM when the goal of the company is directed towards the privacy of sensitive data.
-
Use CSPM when the company has large-scale computing focusing on more elements beyond data only.
Implementation strategies
-
Do Security Audit: This involves reviewing the existing cloud access and identifying areas that need fixing.
-
Set some Targets: Where one decides on implementing either DSPM, CSPM, or both, several clear purposes have to be targeted.
-
Budget for adequate Training: To be successful here, train your personnel on how to use the respective tools.
-
Regular Monitoring: Regularly assess the performance of both your DSPM and CSPM solutions to address the ever-evolving threats.
Read More:- NAT and Firewall Explained: Key Differences and Their Role in Network Security
Conclusion
One does not have to reject one choice or the other when it comes to DSPM or CSPM. Both are crucial and complement each other when it comes to securing the cloud in its way. By comprehending the distinct needs of the organization, one can utilize these tools to make the cloud safe and compliant.
Do not forget that in the case of DSPM and CSPM, it is also possible to integrate both into a single model. A model integrating both virtually guarantees complete protection of focused or sensitive data and the cloud systems providing that data.







Anshul Goyal
Group BDM at B M Infotrade | 11+ years Experience | Business Consultancy | Providing solutions in Cyber Security, Data Analytics, Cloud Computing, Digitization, Data and AI | IT Sales Leader