Cloud Security: Keep your data safe and sound!
Explore vital strategies for cloud security to safeguard your data in the cloud, ensuring compliance and protection against cyber threats.

Cloud Security: Keep your data safe and sound!
Table of Contents
Meaning of cloud security: Security for cloud computing systems is the focus of the cyber security field known as "cloud security." This pertains to safeguarding the confidentiality and security of data across platforms, applications, and infrastructure that are based online. Whether a person, a small- to medium-sized business, or an enterprise uses these systems, both the cloud service providers and the users are responsible for securing them.
Through constantly active internet connections, cloud providers host services on their servers. Customers' trust is essential to their business, so they use cloud security measures to protect and safeguard customer data. The client also has a small amount of control over cloud security, though. A successful cloud security solution requires an understanding of both aspects.
What is security in the cloud?
The technology, protocols, and best practices that safeguard cloud computing environments, cloud-based applications, and cloud-stored data collectively constitute cloud security. Understanding exactly what needs to be secured as well as the system components that must be managed is the first step in securing cloud services.
The majority of backend security vulnerability development is in the control of cloud service providers. Clients should concentrate primarily on proper service configuration and safe use habits in addition to selecting a security-conscious provider. Clients should also confirm that any end-user networks and hardware is properly secured.
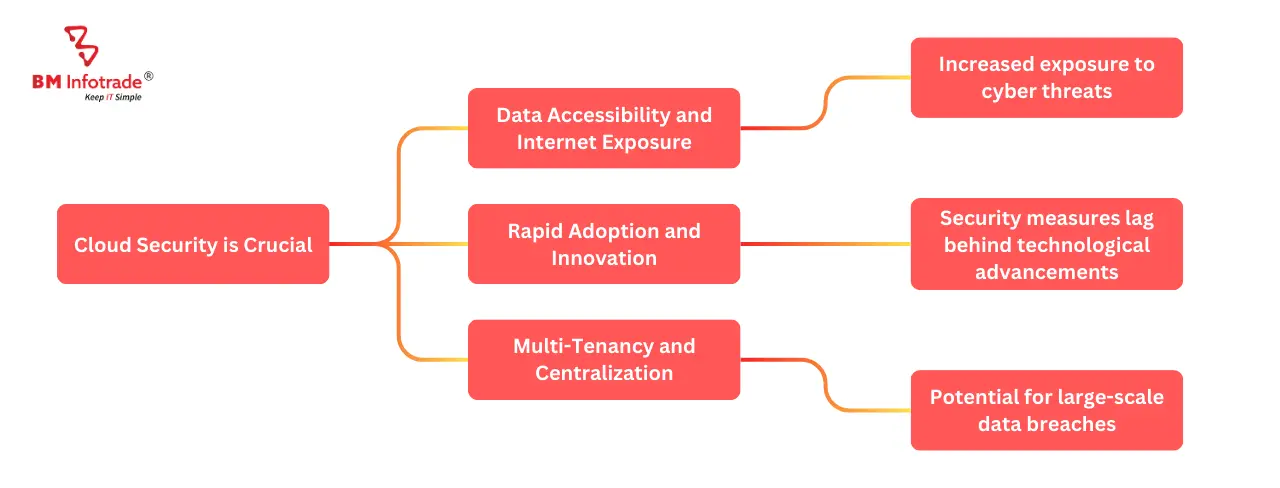
Reasons why cloud security is crucial
Read More: Cloud Security Challenges: Strategies for Modern Businesses
Business and personal data, as well as security, were local in the 1990s. Data would be stored on enterprise servers if you worked for a company and on the internal storage of a PC at home. Everyone has had to reevaluate cyber security as a result of the introduction of cloud technology. Your data and applications might be accessible via the internet at all times while bouncing between local and remote systems. That information may be stored anywhere if you use Salesforce software to manage your customers or Google Docs on your smartphone. As a result, protecting it is more challenging than when it was simply a matter of preventing unauthorized users from accessing your network. Although it requires changing some old IT habits, cloud security has become more commonplace.
Prioritizing comfort over security:
The use of cloud computing in both the workplace and at home is rapidly expanding. Innovation has made it possible for new technology to be implemented more quickly than industry security standards can keep up, increasing the burden on users and providers to take accessibility risks into account.
Storage with multiple tenants and centralization:
On a 24/7 web-based connection, every component—from core infrastructure to small data like emails and documents—can now be located and accessed remotely. It could be extremely dangerous for all this data to be gathered on the servers of a few big service providers. Threat actors can now target huge data centers with multiple organizations and cause massive data breaches.
Two main perspectives are used to secure cloud computing components
Third-party providers offer various cloud service types as building blocks for the cloud environment. You may control the service's components to varying degrees depending on the type of service:
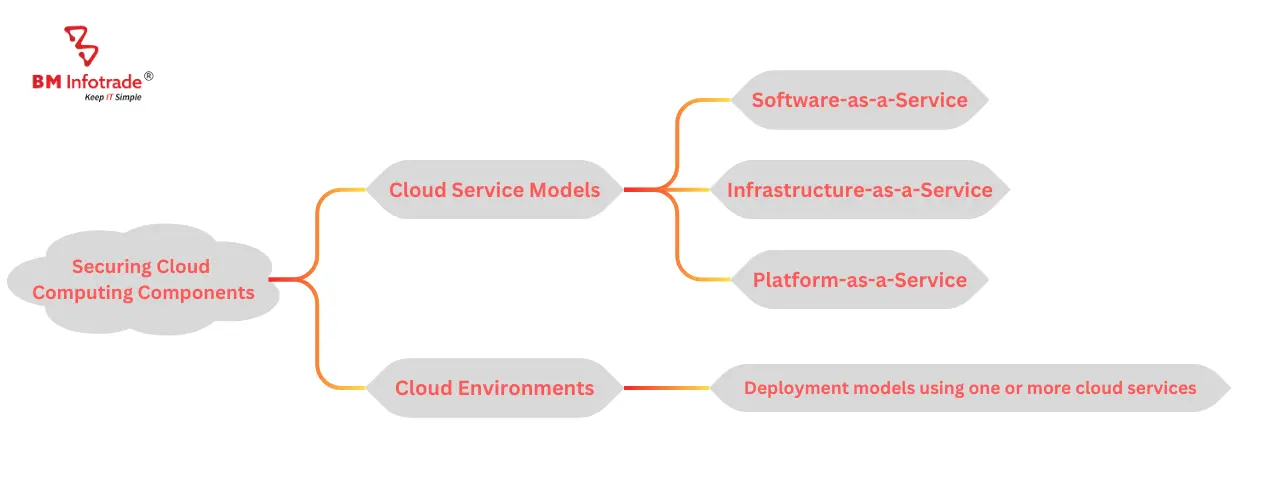
The management of the physical network, data storage, data servers, and computer virtualization frameworks is at the heart of every third-party cloud service. The service is delivered to clients so they can access it remotely by virtue of being virtualized on the provider's servers and delivered over their in-house managed network. In order to provide clients with access to their computing needs from anywhere with internet connectivity, hardware and other infrastructure costs are offloaded.
Clients have access to applications that are solely hosted and run on the provider's servers through Software-as-a-Service (SaaS) cloud services. Applications, data, runtime, middleware, and the operating system are all managed by providers. Clients' only responsibility is obtaining their applications. Google Drive, Slack, Salesforce, Microsoft 365, Cisco WebEx, and Evernote are a few examples of SaaS.
Platform-as-a-Service cloud services give users a place to host the development of their own applications. These applications are then run on provider servers in a client-specific "sandboxed" environment. The operating system, middleware, and runtime are managed by providers. The management of client applications, data, user access, end-user devices, and end-user networks is the responsibility of the client. Examples of PaaS include Windows Azure and Google App Engine.
Clients who use Infrastructure-as-a-Service (IaaS) cloud services can house the majority of their computing, right down to the operating system, on hardware and remote connectivity frameworks. Only core cloud services are managed by providers. All of the components that are stacked on top of an operating system, such as applications, data, runtimes, middleware, and the OS itself, must be secured by clients. Clients must also manage user networks, end-user devices, and access rights. Examples of IaaS include Amazon Web Services, Google Compute Engine (GCE), and Microsoft Azure (AWS).
Cloud environments are deployment models in which a system for end users and organizations is created using one or more cloud services. Between clients and providers, these divide management duties, including security.
The cloud environments that are in use today are:
- Multi-tenant cloud services are what make up public cloud environments, where clients share a provider's servers with other clients, much like an office or coworking space. These are third-party services that the provider manages to provide clients with access to online.
- The use of a cloud service that gives the client exclusive access to their own cloud is the foundation of private third-party cloud environments. Typically, an outside provider owns, manages, and operates these single-tenant environments offsite.
- Private in-house cloud environments, which run from their own private data center, are also made up of single-tenant cloud service servers. In this instance, the cloud environment is managed by the company directly, allowing for complete element setup and configuration.
The use of two or more cloud services from different providers is included in multi-cloud environments. Any combination of public and/or private cloud services may be used for these.
Hybrid cloud environments combine one or more public clouds with a private third-party cloud and/or onsite private cloud data center.
Read More: Architecture of Cloud Computing- Designs that change the world
Conclusion:
There is no question that cloud computing is the way of the future, and there is also no question that cyber security will remain essential. When you consider all of these factors, you can see how cloud security is the next step in IT evolution, as the volume of data and associated risks grow, laws like the GDPR make security enforceable, and new IoT technologies undermine it.





![Cloud Licensing and Compliance Made Easy [All-in-One Bundle]](https://bminfotrade.com/assets/upload/blog/21851766642757.png)
Anshul Goyal
Group BDM at B M Infotrade | 11+ years Experience | Business Consultancy | Providing solutions in Cyber Security, Data Analytics, Cloud Computing, Digitization, Data and AI | IT Sales Leader