Cloud Security Challenges: Strategies for Modern Businesses
Identify key cloud security challenges faced by businesses and discover strategies to mitigate risks and enhance data protection in the cloud.

Cloud Security Challenges: Strategies for Modern Businesses
Table of Contents
Modern companies need cloud computing in today's fast-changing technologies. Cloud computing is unparalleled in scalability, flexibility, and efficiency. To secure their data and operations, organisations must overcome many security issues while transitioning to cloud infrastructures.
Cloud Security Challenges
The risks and limitations of cloud settings make cloud security problematic. These include data breaches, insider assaults, misconfiguration vulnerabilities, shared technology vulnerabilities, and compliance and regulatory obligations. Data breaches cost companies money, reputation, and legal trouble. Accidental or intentional insider attacks can harm crucial data and disrupt organisation. Errors in cloud settings can let hackers access critical systems and data. Technology vulnerabilities like infrastructure or resource difficulties might jeopardise several cloud tenants. GDPR, HIPAA, and PCI DSS hamper cloud security attempts.
Addressing Cloud Security Challenges
Companies require a comprehensive cloud security plan to tackle these issues. This includes identity and access management, encryption, continuous monitoring, secure development, network security policies, and disaster recovery. Addressing cloud security challenges and anticipating threats may help businesses leverage cloud computing while securing their digital assets and complying with laws.
Common Cloud Security Challenges
Cloud Vulnerabilities: Cloud security challenges are a major concern. APIs, misconfigurations, access limitations, and popular technology can cause vulnerabilities. While protecting cloud infrastructures, businesses confront data breaches, insider threats, DDoS attacks, misconfiguration vulnerabilities, shared technology vulnerabilities, and compliance and regulatory issues.
Understanding Cloud Security Challenges
Businesses moving to the cloud face security vulnerabilities that might affect data and resource confidentiality, integrity, and availability.
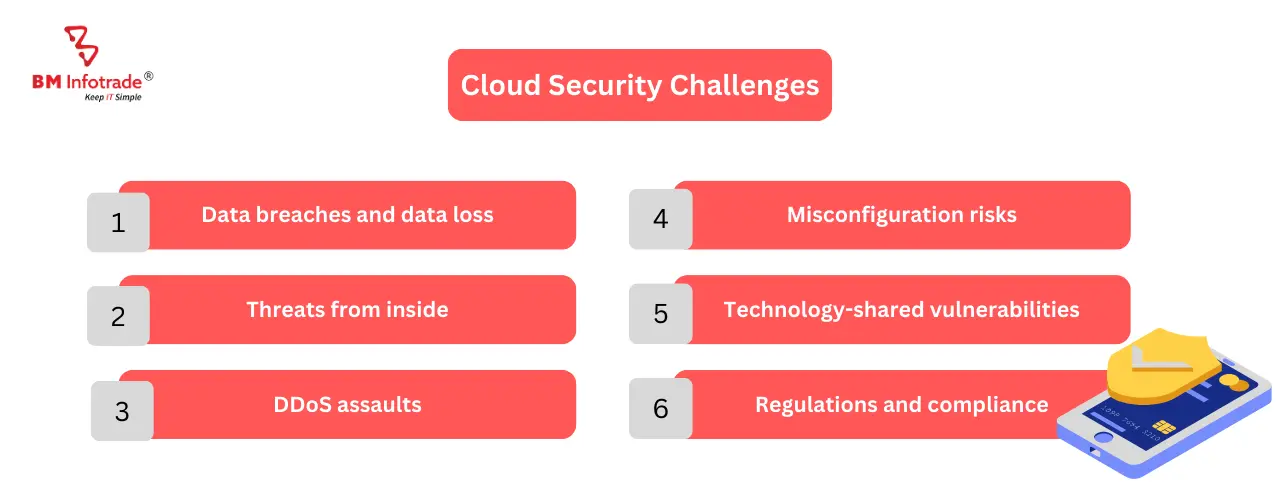
Data breaches and data loss
- Unauthorised cloud users may steal or leak sensitive data.
- Human errors, technological issues, and hackers can cause cloud data deletion, damage, or loss.
Threats from inside
- Malicious insider threats from workers, contractors, and partners with privileged cloud access harm cloud security.
- Threats include data exfiltration, sabotage, and unauthorised configuration modifications.
DDoS assaults
- DDoS attacks overwhelm cloud services with bandwidth, blocking legitimate users.
- Businesses may suffer delays and losses from DDoS assaults.
Misconfiguration risks
- Misconfigured cloud security settings and policies can expose systems and data to hackers.
- Misconfigurations can occur from human error, cloud security best practices ignorance, or cloud service provider security issues.
Technology-shared vulnerabilities
- Multi-tenant vulnerabilities exist in cloud systems due to shared infrastructure and resources.
- An exploitable vulnerability in virtualization platforms, hypervisors, or shared storage systems can undermine cloud services.
Regulations and compliance
- Industry-specific data protection, privacy, and security requirements apply to regulated businesses.
- Legal troubles, financial penalties, and reputation damage might result from violating regulations.
Read More: Architecture of Cloud Computing- Designs that change the world
Cloud security strategies
Businesses must adjust security methods to their needs and operations to reduce cloud security threats and protect sensitive data.
IAM implementation
- RBAC assigns roles and privileges to users to restrict access to sensitive data and resources.
- To prevent unauthorised access, use passwords, biometrics, or security tokens.
- Monitoring privileged accounts and restricting their access to critical systems and data decreases insider threats and unauthorised activities.
Encrypting Data
- Encrypting data during network transmission and cloud storage improves data confidentiality and integrity.
- Thorough key management processes—key production, distribution, rotation, and revocation—secure encryption keys and prevent unauthorised access.
Continuous Auditing and Monitoring
- Real-time SIEM systems monitor, correlate, and analyse security events and alerts to identify and respond to threats.
- IDS and IPS can detect and halt malicious activities, unauthorised access attempts, and network abnormalities to avoid security breaches.
Safe Development Methods
- Effective error handling, input validation, and output encoding reduce software application vulnerabilities.
- Security vulnerabilities are found and fixed via penetration testing, vulnerability scanning, and code reviews.
Setting up Network Security
- Isolated virtual networks with specific security settings and access restrictions safeguard cloud resources.
- Configuring NACLs and security groups allows organisations to implement network security policies and restrict access to authorised entities by granularly controlling inbound and outgoing traffic.
Cloud Provider Security
- Clarifying cloud service providers' and customers' security roles helps businesses implement security measures.
- Cloud security is improved by using cloud providers' encryption, identity management, and compliance certifications.
Disaster Recovery and Business Continuity Planning
- Regular data backups, offsite storage, and disaster recovery strategies enable companies to recover quickly from data breaches, disasters, and service disruptions.
- Reliable designs with redundant components, failover techniques, and automated failover procedures decrease downtime and ensure critical service availability.
Cloud Governance and Compliance
Cloud data must be protected by sophisticated compliance and governance structures as businesses use cloud services more.
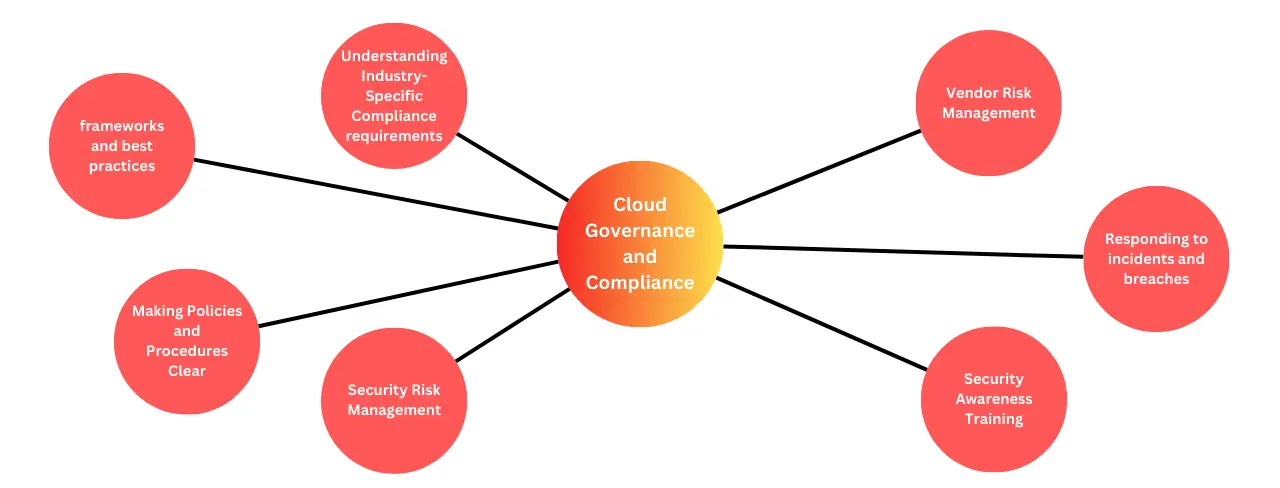
Understanding Industry-Specific Compliance requirements
- Compliance and regulation are industry-specific for healthcare, financial, and government companies.
- Examples: HIPAA for healthcare, PCI DSS for credit card processors, and GDPR for EU residents' data processors.
Cloud security frameworks and best practices
- The Cloud Security Alliance (CSA) Cloud Controls Matrix and Centre for Internet Security (CIS) guidelines provide cloud security best practices.
- These frameworks help businesses assess cloud security, identify vulnerabilities, and implement policies.
Making Policies and Procedures Clear
- Clear cloud use and security policies, processes, and standards assist assure organization-wide uniformity and responsibility.
- Policies should outline employee and stakeholder roles in data classification, access restrictions, encryption, incident response, and vendor management.
Security Risk Management
- Management of security risks and vulnerabilities that might harm cloud-based systems and data is security risk management.
- Risk management should encompass detection, investigation, evaluation, treatment, and ongoing monitoring and review to address security risks and vulnerabilities.
Vendor Risk Management
- Outsourced data and service security requires assessing and managing third-party cloud service provider and vendor security threats.
- Organisations should do thorough due diligence, assess vendor security controls and processes, and establish contractual agreements and SLAs to mitigate vendor risks.
Responding to incidents and breaches
- Security incidents and data breaches may be detected, responded to, and recovered promptly with incident response procedures.
- Incident response plans should cover roles, escalation, communication, and post-event analysis and remediation.
Security Awareness Training
- Regular security training and education raises staff understanding of cloud security issues, best practices, and policies.
- Phishing awareness, password hygiene, data protection, and incident reporting training should empower staff to improve security.
Training and Awareness for employees
Effective cloud security requires strong technology controls personnel knowledge and attentiveness. Maintaining a safe cloud environment requires personnel training to identify and respond to security risks.
Security Awareness Training
- Security awareness training should include areas like:
- Detecting phishing and social engineering
- Good password hygiene and multi-factor authentication
- Knowledge of data categorization and management
- Reporting suspicious activity or security events
- Regular training, workshops, and simulated phishing exercises promote security awareness and culture in the organisation.
Training and Access Controls by Role
- Workers get job-specific security training to comprehend and fulfill their obligations.
- RBAC reduces data breaches by restricting employees' access to sensitive data and systems by job function.
Ready for an incident
- Training staff on incident response processes helps them handle security issues and data breaches.
- Regular tabletop exercises and drills evaluate incident response plans, highlight areas for improvement, and prepare for real-world security issues.
Constant Security Awareness
- Security knowledge must be reinforced and updated to reflect new threats and technology.
- Internal communication channels, newsletters, and security alerts advise staff about new dangers, best practices, and security rules.
Cloud Access Security
- Cloud access security controls and secures cloud-based resources, applications, and data to avoid data breaches.
- Strong access controls, authentication, and user identity management systems enforce least privilege access and restrict sensitive data access.
DLP Measures
- Protecting sensitive cloud data from inadvertent or purposeful exposure requires staff data loss prevention training.
- DLP systems that monitor, categorise, and secure sensitive data against unauthorised access, sharing, and exfiltration improve data security and regulatory compliance.
Security Incident Reporting and Response
- A security incident reporting culture encourages employees to report suspicious activity and security issues immediately.
- Clear reporting protocols and private reporting channels help organisations investigate and respond to security events without disrupting business activities.
Read More: Cloud Security: Keep your data safe and sound!
Conclusion
In conclusion, modern enterprises must navigate cloud security hurdles to protect their data, apps, and infrastructure. Organizations must manage cloud security threats as they use cloud computing to boost innovation, scalability, and cost effectiveness.
Cloud security challenges include risks and weaknesses that organizations encounter while implementing cloud services. The concerns include data breaches, insider attacks, misconfiguration vulnerabilities, shared technology vulnerabilities, and compliance and regulatory issues. Data breaches may cost companies money, reputation, and data. Accidental or intentional insider hazards can compromise cloud data confidentiality, integrity, and availability. Misconfigurations in the cloud might expose sensitive data and systems to unauthorised access. Technology vulnerabilities like infrastructure or resource difficulties might jeopardise several cloud tenants. GDPR, HIPAA, and PCI DSS rules complicate cloud security and need industry-specific laws.
These difficulties require a complete cloud security strategy that includes identity and access management, data encryption, continuous monitoring, safe development processes, network security controls, and disaster recovery planning. Businesses may reduce cloud computing risks and secure their assets and sensitive data by deploying strong security measures and monitoring developing threats.







Anshul Goyal
Group BDM at B M Infotrade | 11+ years Experience | Business Consultancy | Providing solutions in Cyber Security, Data Analytics, Cloud Computing, Digitization, Data and AI | IT Sales Leader