Cloud cryptography- expanding opportunities with cloud
Cloud cryptography encrypts data stored in the cloud, adding a high level of security and preventing a data breach.

Cloud cryptography- expanding opportunities with cloud
Table of Contents
Cloud cryptography encrypts data stored in the cloud, adding a high level of security and preventing a data breach. Utilizing encryption techniques, data used or kept in the cloud is secured. Users can securely access shared cloud services because cloud providers encrypt all of the data they store.
Data processing and storage in cloud computing environments require a specific set of security measures, known as cloud cryptography. Encryption and secure key management systems are used to provide data privacy, integrity, and confidentiality.
What is Cloud Cryptography, and how does it operate?
The encryption of data kept in a cloud service is known as cryptography in cloud computing. When data is encrypted, it is changed to appear different until a legitimate user logs in and accesses the "plaintext" (which is the real version of the data). Plaintext is converted into ciphertext, a random string of characters, using cryptographic keys.
Cloud encryption is smart because it protects your data after it has left your company's IT infrastructure. This indicates that the data is secure throughout its entire journey within your cloud computing services. Encryption enhances cybersecurity for your organization by protecting the data itself rather than the locations where it is stored.

Read More:- Cloud scalability-Cloud-integrated innovation
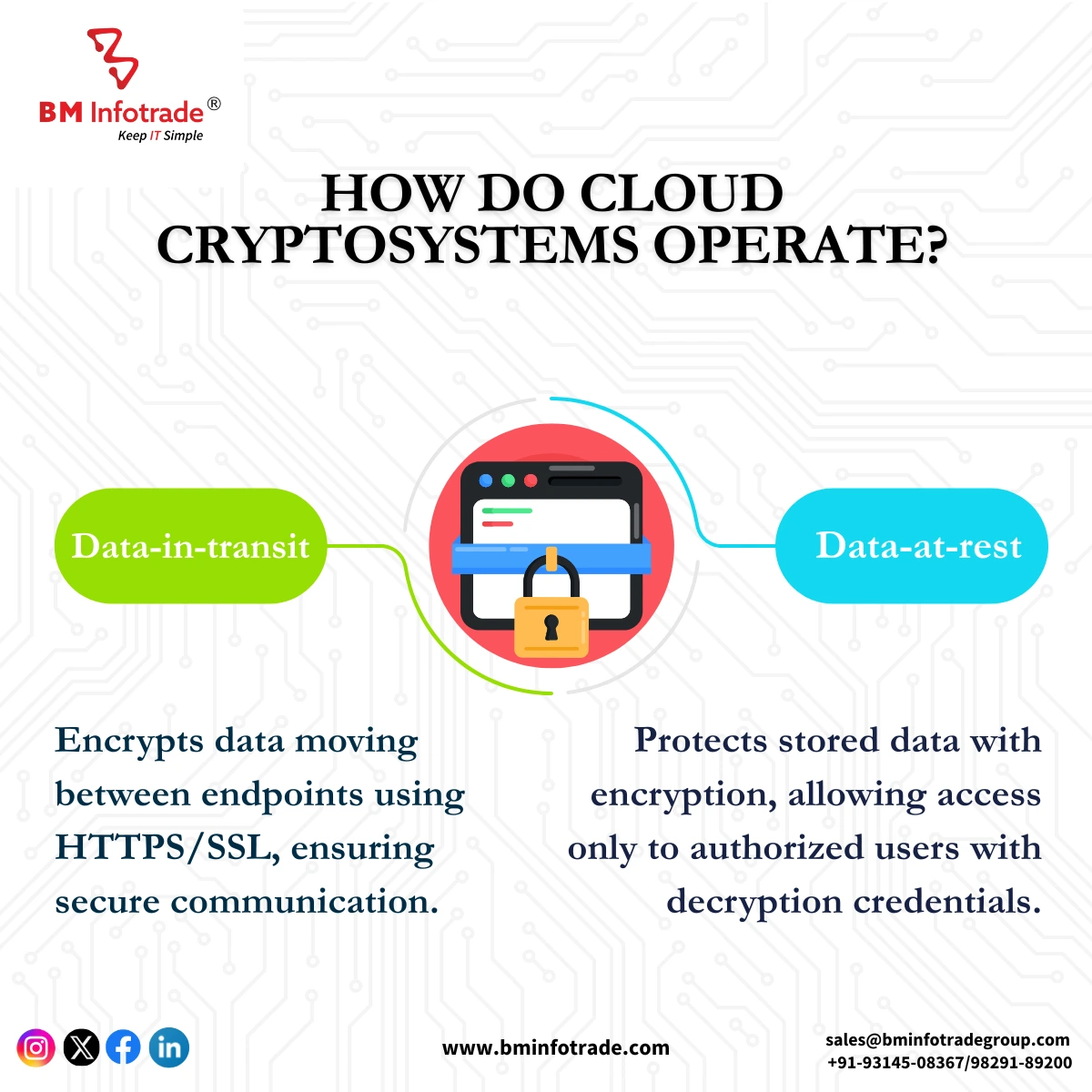
How Do Cloud Cryptosystems Operate?
Data-in-transit
When data is in transit, it is doing so between endpoints. The HTTPS and HTTP protocols that secure the information channel you use when visiting various websites across the web are a common type of data-in-transit cloud encryption that you can see when using an internet browser. They accomplish this using an SSL, also known as "a secure socket layer," which is an encryption layer placed around the secure channel.
When data is sent between your endpoint and the endpoint of the website you are visiting, the SSL within HTTP or HTTPS encrypts both your data and the website's data so that, in the event that your channel is compromised, the hacker would only be able to view encrypted data.
Data-at-rest
Sensitive data is data that is stored in corporate IT infrastructures like servers, disks, or cloud storage services. By encrypting data while it is being stored, you can enforce access control by limiting who has access by granting decryption credentials to authorized employees only. Any other party attempting to access your data-at-rest will see encrypted data instead of plaintext.
Algorithm for Symmetric Cryptography
Authorized users can access both data at rest and data in transit using this type of encryption algorithm without the need for manual encryption or decryption. Once credentials are provided for authentication, the algorithm automatically encrypts and decrypts the sensitive data.
Symmetric cryptographic algorithms still need key management, despite the fact that they are typically automated. Depending on the cloud service provider you use, your organization may decide to use different types of encryption keys or multiple cryptographic key types. Your key management should assist in keeping track of the different encryption keys used by your company if you work with multiple cloud service providers or operate in various cloud environments.
Using ZenGRC, ensure secure cloud computing
Your security and compliance teams benefit from a streamlined, integrated dashboard experience for managing cybersecurity risk with ZenGRC from Reciprocity. You can keep an eye on known risks and get alerts when new attack vectors emerge.
Whether you have data encryption management you're mitigating or you want to develop new cryptographic protocols for improved information security, ZenGRC's cybersecurity experts can help you ensure the strongest level of protection for your sensitive information.
Privacy
Cloud cryptography has privacy as its main benefit. Since the specifics will remain private, there is less chance of fraud from unauthorized users, and the data remains private for the users.
An increase in data security
Data is vulnerable when it is moved from one location to another, but the encryption protects the data's value by preventing this.
Users
The best security precaution is cloud cryptography, according to many experts. Any changes attempted by an unauthorized user are immediately reported to companies or businesses. Anyone with cryptographic keys is able to gain access to it.
Read More:- Cloud Analytics: the deployment of scalable cloud computing
Conclusion
IT services can now be accessed online by businesses thanks to cloud computing, which eliminates the need for on-site servers. The company is exposed to a variety of cyber threats and data breaches due to cloud computing services, though. One way a business can secure its data and defend itself from online attacks is through cloud cryptography. In order to protect data after it has left the company's business IT system, cloud encryption is prudent. By doing this, it is guaranteed that the data is secure throughout its journey through cloud computing services. Instead of securing the places where the data is stored, encryption helps protect the data itself.







Anshul Goyal
Group BDM at B M Infotrade | 11+ years Experience | Business Consultancy | Providing solutions in Cyber Security, Data Analytics, Cloud Computing, Digitization, Data and AI | IT Sales Leader