What is Ransomware? How It Works and Steps to Protect Your Data
Learn what ransomware is, how it works, and effective steps to protect your data from cyber threats. Stay secure with best practices against ransomware attacks.

What is Ransomware? How It Works and Steps to Protect Your Data
Table of Contents
Among all of the cyber security threats that have made the headlines, ransomware is likely the most damaging and costly of them all. Ransomware is a growing threat that can cripple any target, be its organizations or individuals. This article looks at different aspects of ransomware from its definition to its impact on security in the modern world, as well as how an individual can enhance their data security in today’s interconnected environment.
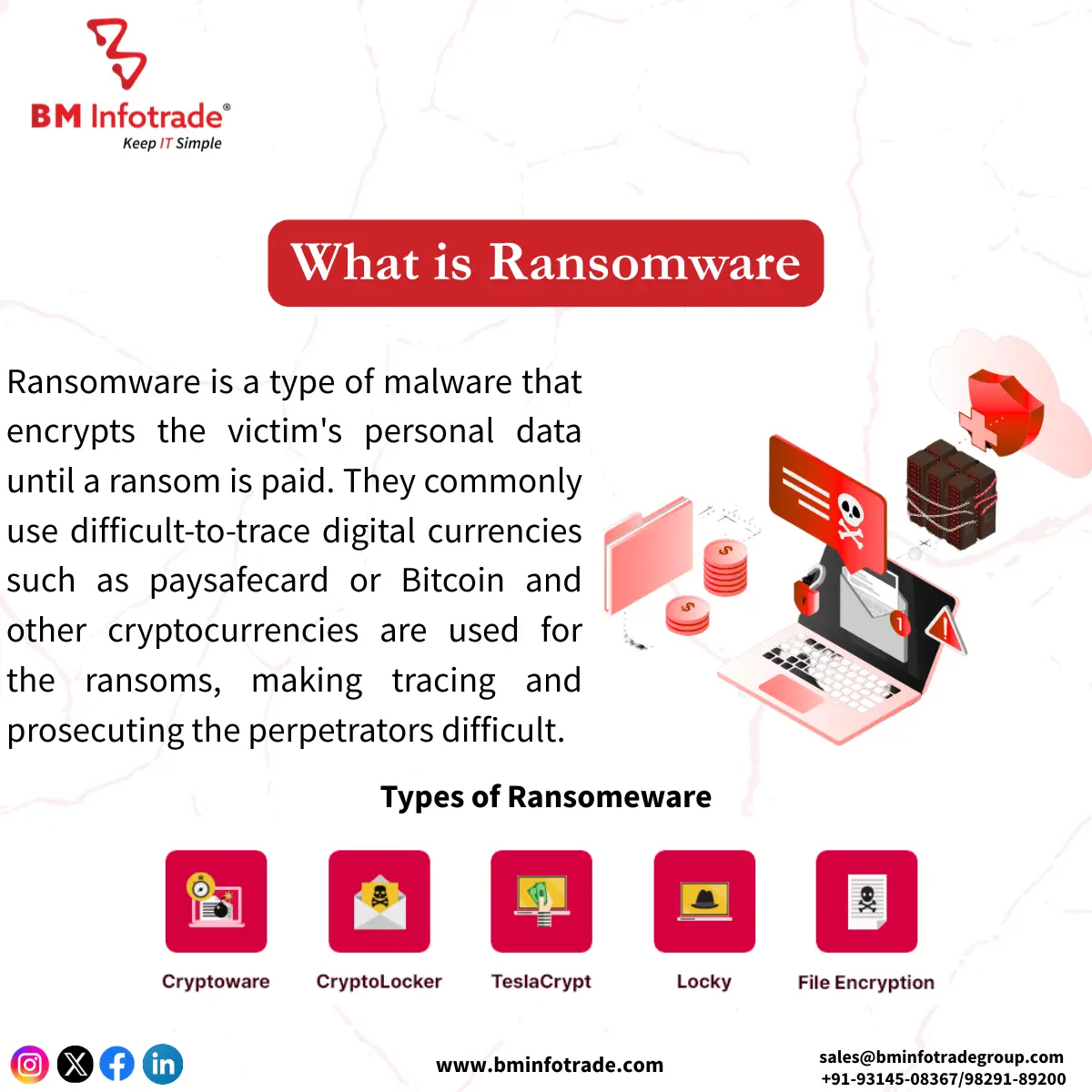
What is Ransomware?
Ransomware is a particular kind of malware that is capable of locking the victim’s files and data and only the criminal with the required key can unlock the data once the ransom amount has been paid. Nowadays, many criminals prefer to be anonymous and out of the reach of law enforcement agencies and as such, they request payments in cryptocurrencies such as Bitcoin. Such Sectors including but not limited to individuals, businesses, healthcare institutions, government and military agencies, and any other critical infrastructure can be at risk of these types of cyber threats.
How Does Ransomware Work?
Ransomware works in specific steps including, infection of a system, encryption of the files and finally, ransom payment.The steps can be elaborated as follows:
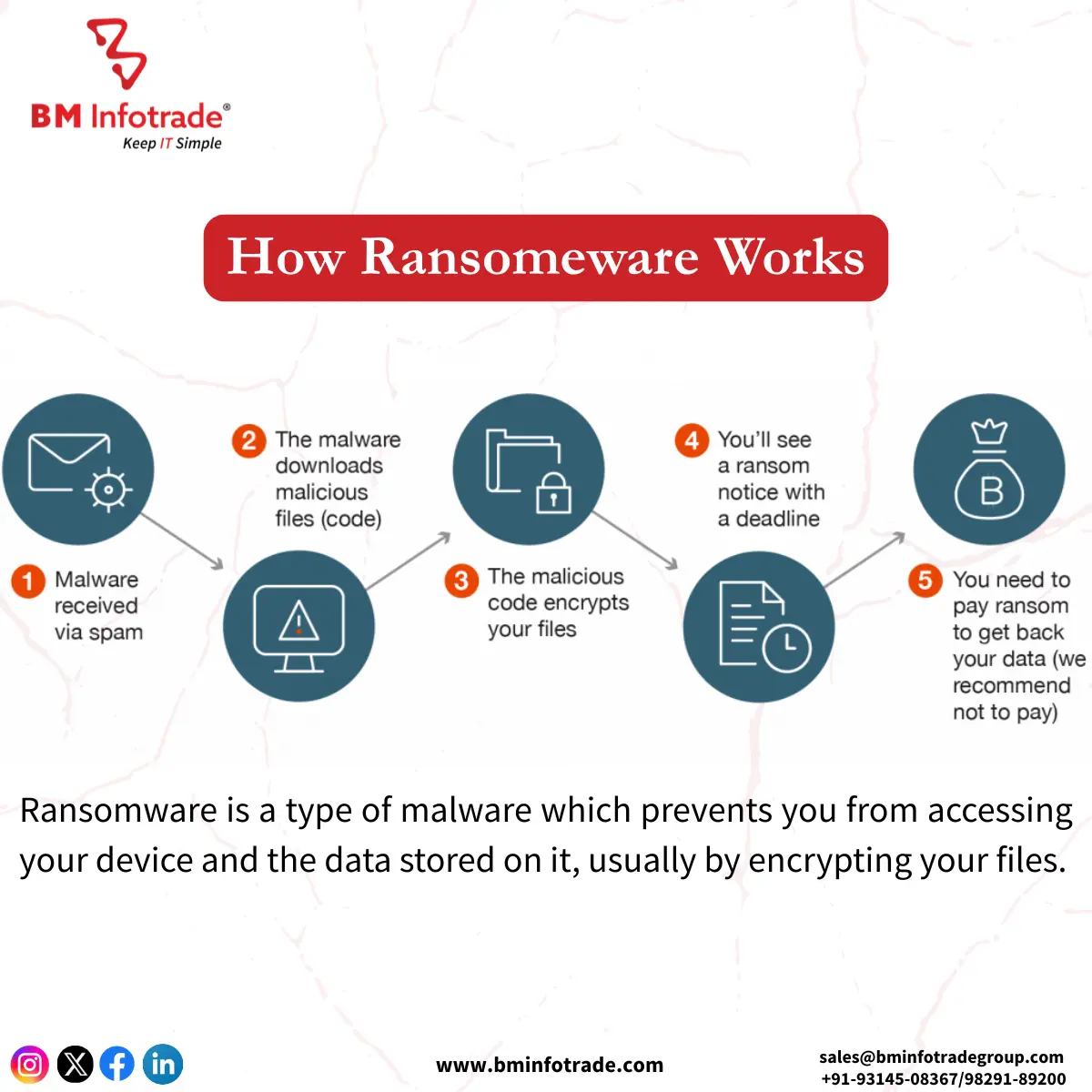
1. Infection
Infection is usually where the possession of ransomware commences and this is the stage where the ransomware has not yet activated within the targeted system but is still capable of locking the target’s files whenever it is ready. Common methods of system infection include:
-
Phishing Emails: Malicious URLs embedded within emails or attachments trick victims into clicking on other sources leading to ransom downloads.
-
Malicious Websites: Such websites include homepages that are able to trigger automatic downloads of ransomware upon being accessed by users.
-
Exploiting Vulnerabilities: This includes targeting software that has not been patched yet and making ransoms out of them.
-
Infected USB Drives: A scenario where a USB device that was already compromised can still hold ransomware can be possible.
2. Payload Execution
When the cybercriminal is inside the network, the ransomware carries out its malicious execution. It usually turns off antivirus applications, erases system images, and makes sure access to important files is blocked out.
3. Data Encryption
The ransomware traverses the system’s landscape searching for valuable assets like documents, photographs or even databases and encodes these files with top-grade ciphers. Without the decryption key, victims cannot access these files.
4. Ransom Demand
When encryption is achieved, the attacker presents a ransom demand, with the particulars of how to pay and a lag time in most instances. Some ransomware threatens the loss of files or escalation of the amount paid if the victim delays making the payment.
Types of Ransomware
The numerous types of ransomware available on the market have their different attack patterns. The most famous include the following:
1. Crypto Ransomware
This locks files and makes them impossible to open unless the ransom is paid. Examples include WannaCry and CryptoLocker.
2. Locker Ransomware
The locker ransomware includes display screens with messages demanding that the user pay the ransom in order to unlock the phone. Additionally, as the list's name suggests, users who pay the ransom never get to access their files until the ransom is paid.
3. Double Extortion Ransomware
These types of ransomware are known for taking up the attention of the public, the cybercriminal first locks filing and threats to expose vital organizational documentation if their ransom is not met. A perfect example is maze ransomware.
4. Ransomware as a Service (RaaS)
With this model of operation, attackers sell services on ransomware tools to other attackers or even lease them out on rent. RaaS allows even the most inexperienced hackers to commit attacks by allowing them to conduct attacks.
Who is Targeted by the Ransomware?
Ransomware attackers frequently go after people or organizations that have important data or limited security protection. Some of the most prevalent targets are as follows:
-
Enterprise Corporations: More primarily SMEs that suffer from subpar cyber security mechanisms.
-
Healthcare Institutions: Due to the sensitive and urgent nature of patient data, the hospitals become easy targets.
-
Educational Institutions: Due to the limited risks, schools and universities lack strong cybersecurity systems.
-
Governmental Agencies: The attackers take advantage of obsolete technology and the nature of work that governments do
-
Private individuals: Personal electronic devices such as phones which have pictures and important documents as well as financial data are at risk too.
The Impact of Ransomware
The aftermath following a ransomware attack has severe and devastating effects. Some of the key impacts include:
1. Financial Losses
Hostage victims have to pay massive ransom fees, costs of downtime and charges for the recovery process. To businessmen, a fatal loss could even go upto millions.
2. Loss of Data
Where hosts are unable to comply with the demands and also have no backup of the data, it is likely that encrypted files may be rendered permanently impossible to access.
3. Loss of reputation
The ransomware culture has affected many organizations and people, especially if data that is more sensitive is exposed.
4. Shifting of business operations
This impact cuts across all ransomware-attacked organizations whereby it leads to loss of productivity and customer dissatisfaction.
Conclusion
Ransomware is a major threat to victims and organizations alike however, threats are managed through respectful measures. Understanding and designing a stretch-out penetration plan through which one will manage the ransomware as a service helps one’s structures and sensitive information to be safe, as the chances of an attack are significantly reduced.
Always remember that it is better to prevent than it is to cure. A few measures such as using appropriate software, monitoring for evolving risks, and educating staff on cybersecurity best practices can greatly help in securing sensitive information from ransomware attacks.






Anshul Goyal
Group BDM at B M Infotrade | 11+ years Experience | Business Consultancy | Providing solutions in Cyber Security, Data Analytics, Cloud Computing, Digitization, Data and AI | IT Sales Leader