What is Malware and How to Protect Your Business from It
Malware is malicious software designed to harm or exploit devices, networks, or data. Learn how malware works, its types, and practical steps to protect your business from cyber threats.
What is Malware and How to Protect Your Business from It
Table of Contents
Malware has proven to be one of the most common and destructive of all cyber threats, impacting people at individual, societal, corporate, and even state levels. It is critical to learn what malware is, how it behaves and how it can be contained to prevent any breach of information confidence and trust in the systems. This entire document aims to address the different categories of malware, its vectors, impacts and effective measures to avoid being explicitly cauterized.
What is Malware?
Simply put, malware also known as ‘malicious software’ or ‘malicious code’ is a term for any computer code that is created with the intent to target and disrupt normal computer activities and operations. Cybercriminals weaponized malware for various malicious purposes: sensitive information theft, data ransom, and severe disruption of ecosystems or units.
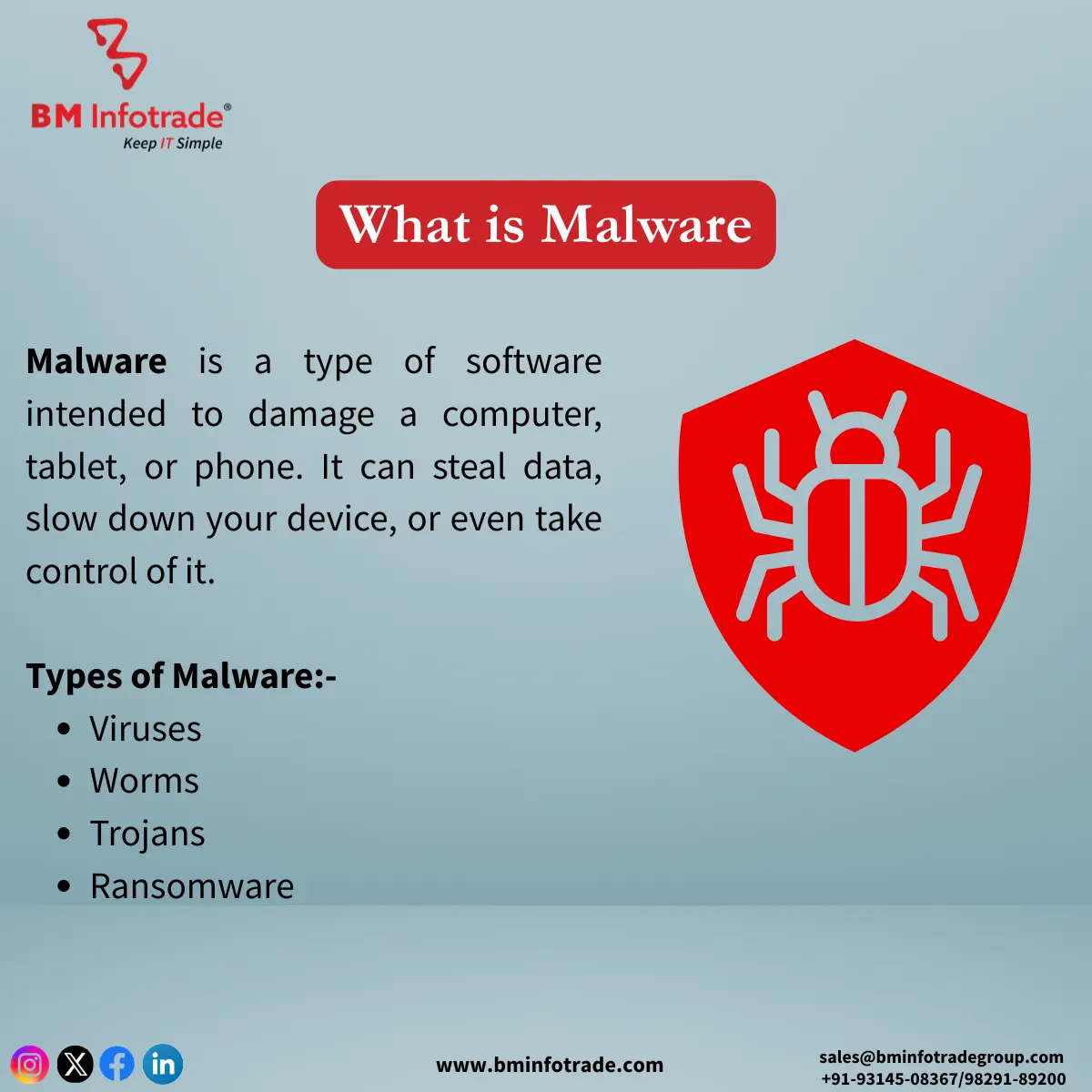
Types of Malware
Various types of malware exist each characterized by sharp differences in molarity and constructed tools of mass destruction. Enlisted below are some of the most dominant types of the are mentioned:
1. Viruses
A virus is a computer program that is designed to reproduce itself and attach itself to other programs. These viruses tend to attack legitimate files and execute themselves as soon as an inherent file or program is launched, flooding systems with a replication of the viruses and causing destruction and corruption across documents and systems.
2. Ransomware
They often render victims’ files undecryptable and demand payments, generally in the form of cryptocurrency, for keys that allow for decryption. Regardless of how extreme, various industries such as healthcare, finance, and vital national infrastructure facilities have come under the hammer of such threats, especially of late.
3. Trojans
The Trojans were named after the famous Trojan Horse as they appear as if they are benign software but are quite the opposite. Once operational, they have the capacity to circumvent security measures and enable illegal entry, or even extract secret documents.
4. Spyware
Spyware is a malicious software program that is emphatically intrusive and tracks the user's or victims’ clicks behind the scenes. These lay low and go unnoticed, for example, capturing passwords and credit information or what is referenced as browsing history.
5. Adware
Although adware is not a serious threat, it is an annoyance and invades users with excessive unsolicited ads that usually affect device performance. However, they may lead users to fake websites that are used in agile phishing scams.
6. Worms
Worms are known as computer viruses that are independent programs but go forth and self-reproduce on networks making them faster than the speed of users. Deliveries such as ransomware are entirely notorious for being branched from those.
7. Keyloggers
Keyloggers are a form of malicious software that captures the customer’s pin or unique identification through keystroke techniques. In most cases, they come in phishing messages or dangerous internet links.
8. Rootkits
Many rootkits are also viruses in the sense that they aid illegal system administrators’ privileged access. Due to their evasion of detection, They tend to switch off antivirus systems or other protection-related features.
Read More:- Cyber Security; Importance, Types, Tips, and Examples?
How Malware Spreads
All forms of malware have turned into networks and are consistently advancing on their own. By knowing these means, it provides the ability to dodge the threat to those using the system:
1. Phishing Emails
To a great extent, hostile actors control such attack campaigns using emails that contain malicious hyperlinks or attachments, in this case sending emails with a tendency to defraud to download malware applications.
2. Malicious Websites
Visiting compromised or fake websites can lead to malicious software infections, or simply malware. Drive-by downloads happen when malware is installed without the user even having to prompt installation.
3. Software Downloads
Downloading software that is not from trusted sources can give the PC malware attacks. Cracked software is among the many.
4. USB Drives
Most forms of malware can spread through USB devices and any other devices that may be infected. This is more common in settings where sharing of hardware is done by more than one person.
5. Social Engineering
Users fall prey to attacks due to a lack of trust and confidence in people. Users give out sensitive information or download malware because they believe everything that they are told by the attackers.
6. Exploiting Vulnerabilities
Malware is usually installed by other attackers because the outdated software contains unpatched vulnerabilities and is not up to current standards.
The Impact of Malware
The impact that malware has on a system is adverse and could result in the company making huge losses and even losing the reputation of its clients. This is some of the negative influence that malware has on persons and companies:
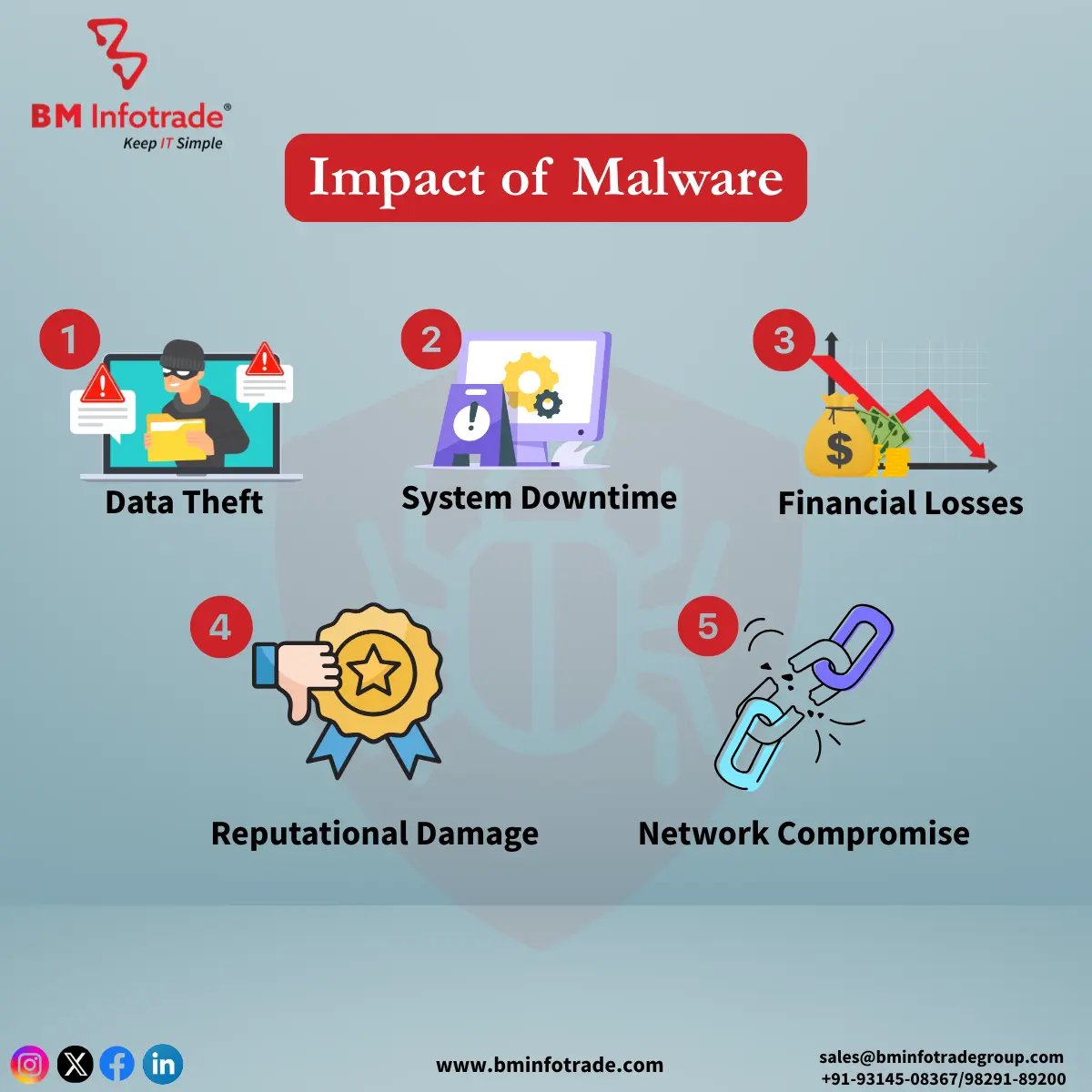
Data Theft: Forms of malware such as spyware seize financial records and personal information to sell it on the dark web.
System Downtime: Make certain systems inoperable which tax the efficiency of the organization.
Financial Losses: Ransomware taunts its victims with payments that run into millions. Data breaches are not cheap at all and due to compliance laws have to be fined.
Reputational Damage: Organizations being tarnished through malware attacks lose customer trust and this pulls their reputation down for long periods.
Network Compromise: Worms and Trojans are the two common types of malware that spread through networks and as a result, multiple systems may get compromised.
Malware Detection Procedure
The first rule of malware is that it gets easier to control once you know what to expect. (Sounds a bit strange at first but hear us out!) These are some indicators of potential infection:
Degraded performance of the device.
1. Issues with the device, such as random crashes or freezing.
2. Watching advertisements that you did not choose to see.
3. Programs that you do not remember downloading or installing are running on your device.
4. Changes have been made to the system or the preferences of the web browser.
5. Data being used or accessed over the network but with no known reason.
Should you find any signs, make sure to perform an investigation and resolution ASAP.
Read More:- Why cyber security? Block the hackers, secure it, and lock it down.
Final Thoughts
Malware programs are indeed a major menace in the modern age but with enough knowledge, one can understand what type of malware strives to achieve, how they reproduce and how one can circumvent their effects. We all have personal devices and even businesses that require protection thus vigilance is very critical.
The best way to handle large-scale pollution threats and supplement the pressures of cyberspace. Integrating reliable processes into enterprises with a minimum understanding of the issues can go a long way in securing today’s technological artefacts.






Anshul Goyal
Group BDM at B M Infotrade | 11+ years Experience | Business Consultancy | Providing solutions in Cyber Security, Data Analytics, Cloud Computing, Digitization, Data and AI | IT Sales Leader