Why Your Cloud Needs a Dedicated Security Layer
A dedicated security layer fortifies your cloud against cyberattacks and compliance threats—BM Infotrade delivers advanced, managed security tailored to Indian businesses.
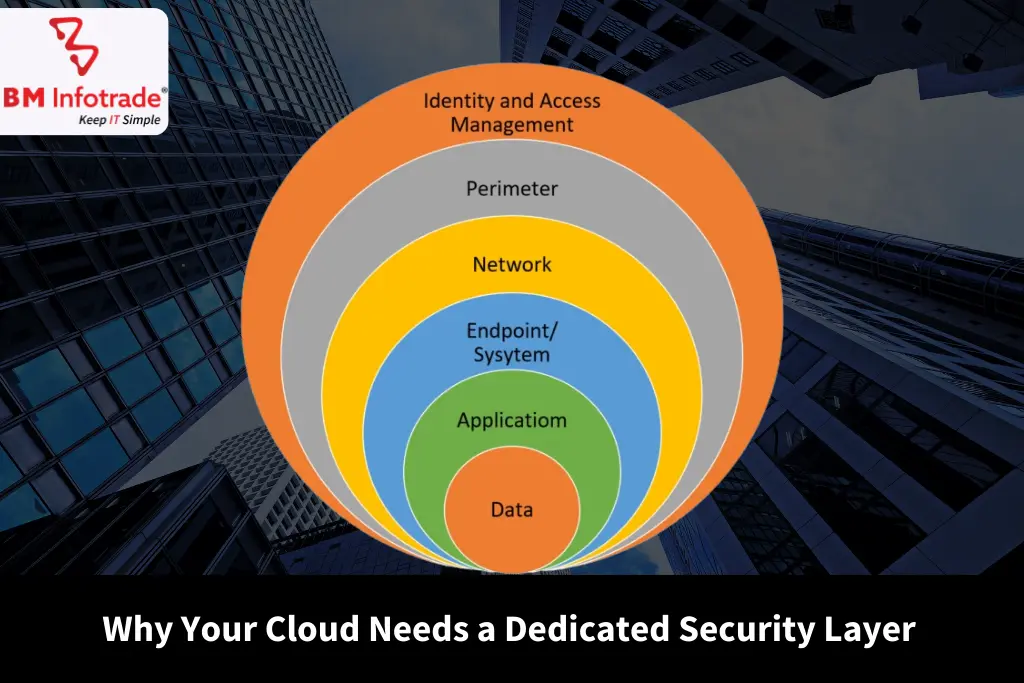
Why Your Cloud Needs a Dedicated Security Layer
Table of Contents
Cloud adoption is sweeping through nearly every industry, offering striking gains in speed, flexibility, and expense efficiency. Whether a fast-moving start-up or a decades-old Fortune 500 company, most digital activities now rest on some form of cloud platform. Beneath that convenience, however, a stubborn security problem lingers: the blind spots that standard, provider-issued tools routinely ignore.
Major cloud vendors do supply basic security features, but their shared-responsibility framework places full responsibility for workloads, data, access, and compliance squarely on the customer. Within that arrangement, adding a purpose-built security layer switches from being a nice extra to an urgent, practical need.
The following sections explain why every solid cloud plan should fold in this dedicated layer, describe how it supplements the controls built into the platform, and outline the specific gaps and threats that remain if the added protection is left out.
The Cloud Security Illusion: Why Built-In Isn’t Enough
Major cloud vendors like AWS, Azure, and Google Cloud offer a suite of security services--identity and access management (IAM), network firewalls, data encryption, and continuous monitoring--yet even these mature toolkits cannot protect against every conceivable vulnerability.
Limitations of Native Cloud Security:
- 1. Fragmented visibility across multiple cloud environments (multi-cloud setups).
- 2. Static security controls struggle with evolving threats like lateral movement or insider attacks.
- 3. Misconfigurations that are often invisible to basic cloud consoles.
- 4. Compliance complexity across different geographies and sectors.
- 5. Limited threat detection and response, especially in hybrid cloud scenarios.
In essence, native cloud security tools are like the locks on a house—but without cameras, motion detectors, or security guards. You need more.
What Is a Dedicated Cloud Security Layer?
A dedicated security layer refers to a third-party, cloud-native solution (or stack of tools) built specifically to monitor, protect, and manage your cloud environment holistically.
It sits above and across your cloud providers, offering unified control over:
- 1. Threat detection and response.
- 2. Cloud posture management.
- 3. Identity governance.
- 4. Encryption key lifecycle.
- 5. Data loss prevention.
- 6. Compliance reporting.
These solutions are often offered as Cloud Security Posture Management (CSPM), Cloud Workload Protection Platform (CWPP), or extended detection and response (XDR) systems.
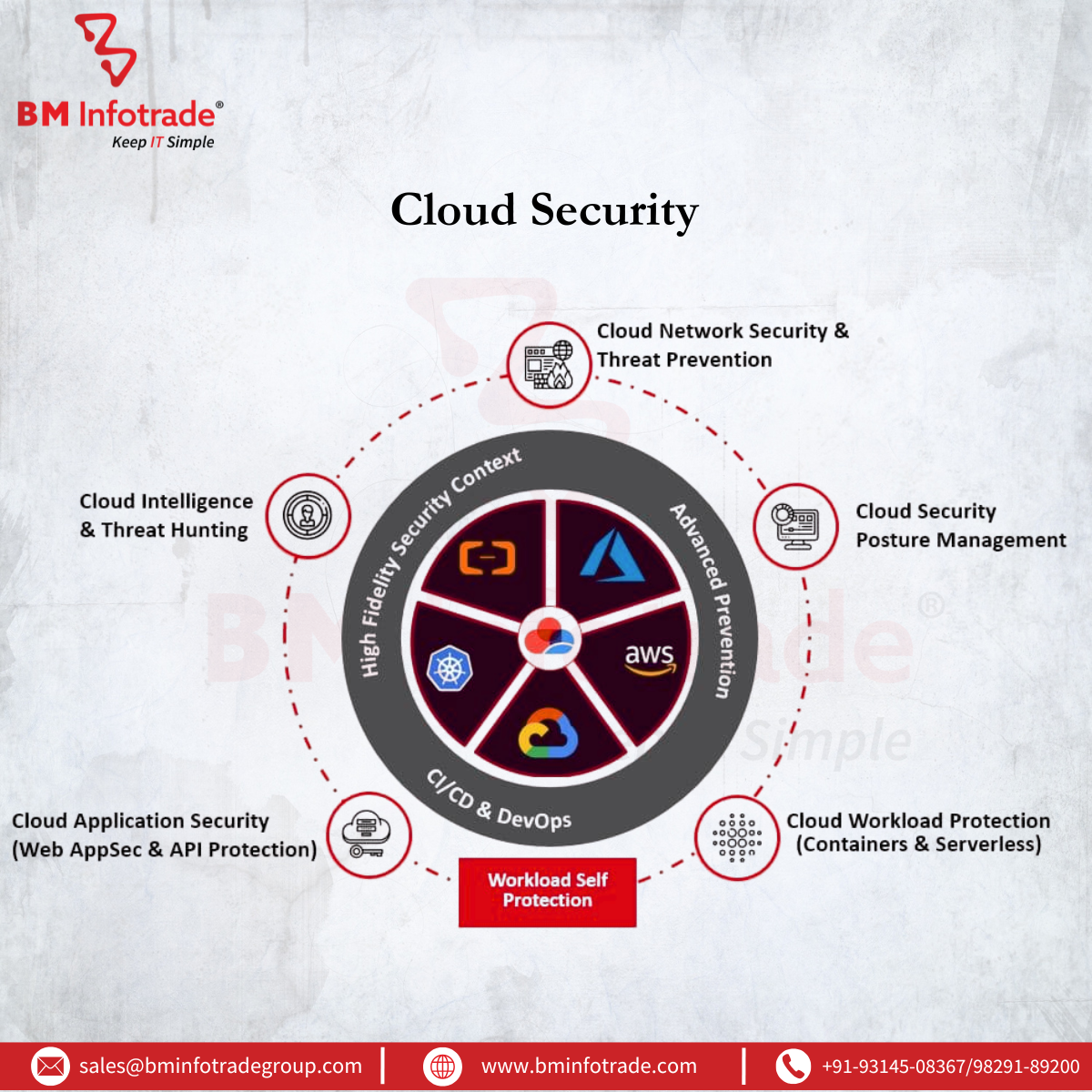
Key Reasons to Add a Dedicated Security Layer
1. Unified Visibility Across Cloud Assets
In modern enterprises, workloads are spread across multiple platforms—AWS for compute, Azure for machine learning, and Google Cloud for analytics. A dedicated security layer correlates data across all these platforms, giving you a centralised dashboard to monitor:
-
1. Network flow logs.
-
2. Suspicious login patterns.
-
3. Asset inventory.
-
4. Policy violations.
This unified view allows security teams to act faster and smarter.
2. Real-Time Threat Detection and Response
Traditional SIEM systems struggle to keep up with the scale and speed of cloud environments. A dedicated cloud security platform uses AI/ML-powered analytics to detect anomalies, flag known attack vectors, and automatically isolate compromised instances.
Examples:
-
1. Detecting excessive data exfiltration from an S3 bucket.
-
2. Identifying privilege escalation by a dormant user account.
-
3. Notifying admins of lateral movement across Kubernetes clusters.
3. Proactive Posture Management
-
1. Detecting excessive data exfiltration from an S3 bucket.
-
2. Identifying privilege escalation by a dormant user account.
-
3. Notifying admins of lateral movement across Kubernetes clusters.
The #1 cause of cloud breaches is misconfiguration—publicly exposed storage, open SSH ports, overly permissive IAM roles, etc.
A dedicated layer provides:
-
1. Continuous misconfiguration scanning.
-
2. Automated remediation (via IaC or API calls).
-
3. Best-practice recommendations.
-
4. Compliance checks for standards like GDPR, HIPAA, ISO 27001, and SOC 2.
4. Multi-Layered Data Protection
Data in the cloud is constantly in motion—being created, shared, duplicated, and moved between services. A robust security layer encrypts and audits this flow at multiple stages:
-
1. At rest (disk-level and object-level encryption).
-
2. In transit (TLS/SSL verification).
-
3. In use (field-level masking and tokenisation).
It also ensures proper key management, with separation of duties between admins and security officers.
5. Identity and Access Risk Management
Modern cloud breaches often begin with stolen credentials. A dedicated layer provides:
-
1. Role and permission audits.
-
2. Behaviour-based anomaly detection (e.g., impossible travel logins).
-
3. Multi-factor authentication enforcement.
-
4. Just-in-time access policies.
-
5. Integration with IAM/PAM solutions.
It helps in aligning with Zero Trust architectures—never trust, always verify.
6. Faster Compliance and Audit Readiness
Industries like finance, healthcare, and manufacturing are bound by strict data governance rules. Dedicated platforms streamline this with:
-
1. Pre-built compliance templates (PCI-DSS, HIPAA, etc.).
-
2. Auto-generated audit trails.
-
3. Risk assessment dashboards.
-
4. Alerts on regulatory violations.
Instead of scrambling during an audit, your team always stays ready.
Business Implications: Why It Matters More Than Ever
According to IBM’s 2024 Cost of a Data Breach Report:
-
1. Cloud-hosted environments had the highest average breach cost at $5.2 million.
-
2. Misconfigured cloud settings accounted for over 30% of incidents.
-
3. Companies using dedicated cloud security platforms detected and responded 37% faster than those without.
In a post-pandemic, AI-driven era, where remote work and global access are the default, investing in proactive cloud security is not a luxury—it’s a business continuity mandate.
How to Choose the Right Security Layer
When evaluating a dedicated cloud security solution, consider:
-
1. Cloud-native compatibility (support for AWS, Azure, GCP, hybrid).
-
2. Automation and orchestration capabilities.
-
3. Scalability with your growing workloads.
-
4. Integration with DevOps tools (CI/CD pipelines, Terraform, etc.).
-
5. Vendor credibility (Gartner, Forrester Wave rankings).
-
6. Support for incident response and real-time alerting.
Popular solutions include platforms like Paloo Alt Prisma Cloud, Wiz, Orca Security, and CrowdStrike Falcon Cloud.
Also Visit:- Cloud Migration
Conclusion
The cloud is evolving fast, but so are threats. Relying solely on native cloud security is like driving a supercar with no seatbelt. It may work… until it doesn’t.
A dedicated cloud security layer empowers your organisation to prevent breaches, maintain compliance, and sleep better at night. As cloud attacks become more sophisticated, layered defence is no longer optional—it’s mission-critical.
FAQs
1. What is a dedicated security layer in cloud computing?
It is an additional protective layer on top of native cloud security to defend workloads from advanced threats, ensure compliance, and maintain operational integrity.
2. Why does my cloud need a dedicated security layer beyond built-in cloud security?
Because built-in security doesn't cover all threats; a dedicated layer provides advanced threat detection, granular controls, and continuous monitoring to prevent breaches.
3. How does BM Infotrade implement dedicated cloud security layers?
BM Infotrade encrypts data, controls cloud access, and performs real-time monitoring with advanced tools tailored for Indian businesses.
4. What are the benefits of having a dedicated security layer?
Benefits include comprehensive protection against cyberattacks, regulatory compliance, minimized downtime, and better visibility and control over the cloud environment.
5. How does a dedicated security layer support compliance regulations?
It enforces security policies, encryption, and audit trails helping businesses meet frameworks like DPDP Act and global standards efficiently.
6. Can BM Infotrade’s cloud security solutions help SMEs with budget constraints?
Yes, BM Infotrade offers affordable cybersecurity packages including managed SOC and endpoint protection fit for startups and SMEs in India.
7. What threat types does a dedicated security layer protect against?
It protects against malware, phishing, data exfiltration, DDoS attacks, insider threats, and unauthorized access.
8. How important is 24/7 monitoring in a cloud security layer?
24/7 monitoring ensures immediate detection and response to threats, reducing risk and downtime, a service BM Infotrade provides through managed SOC.
9. How does cloud encryption fit into a dedicated security layer?
Encryption protects data at rest and in transit, a foundational part of cloud security implemented by BM Infotrade to safeguard sensitive information.
10. What role does access control play in dedicated cloud security?
Access control limits permissions to only essential users, following the principle of least privilege, ensuring reduced attack surfaces and enhanced security.






Anshul Goyal
Group BDM at B M Infotrade | 11+ years Experience | Business Consultancy | Providing solutions in Cyber Security, Data Analytics, Cloud Computing, Digitization, Data and AI | IT Sales Leader