Role-Based Access Control (RBAC) vs. Attribute-Based Access Control (ABAC)
Compare Role-Based Access Control (RBAC) and Attribute-Based Access Control (ABAC) to understand their key differences, benefits, and use cases in securing enterprise data and systems.
Role-Based Access Control (RBAC) vs. Attribute-Based Access Control (ABAC)
Restricting access to sensitive data resources to authorised users is an essential component of cyber security which is referred to as access control. There are two kinds of Access Control models which have become popular, and which many have accepted, are: Role-Based Access Control (RBAC) and Attribute-Based Access Control (ABAC). However, while both aim at augmenting protection, they differ in their application and implementation. Let's examine their major differences and how to determine which one fits your company the best.
What is Role-Based Access Control (RBAC)?
Among the most widely used access control models for businesses is Role Based Access Control which is also known as RBAC. This approach provides users with access rights that correspond to their functions within the Organization. For instance, a certain access role is supposed to be assigned to the Managers, Administrators, Employees, etc.
How RBAC Works:
-
Defining New Roles: In every organization, fresh roles will be created such as Finance Manager, HR executive, etc.
-
Defining User Permissions: Permissible actions will be defined for all created roles, for instance, a role may have the ability to authorize payroll or approve requests for leave.
-
Assigning Roles to Users: Users will be attached to the roles and automatic inheritance for the permissions about the attached role will apply.
Example:
A person in the finance team has tasks related to records, with the title "Finance Manager". In comparison, an intern with the title `finance intern` has restricted access to specific reports only.
Advantages of RBAC:
-
Simplicity: Implementation and management are straightforward.
-
Scalability: Ideal for institutions with specific role assignments.
-
Consistency: Facilitates the standardization of the access control policy across various teams.
Read More:- 5 Types of Cyber Security: Protecting Your Digital Assets
What is Attribute-Based Access Control (ABAC)?
In an ABAC model, access is provided based on a range of relevant attributes, such as user traits, information about the resource, or the environment. There are numerous differences, but perhaps the most prominent is that, within the scope of ABAC, access control may be adjusted based on many characteristics, rather than one as in RBAC.
How ABAC Works:
-
Define Policies: Policies can be created by utilizing such attributes as user department, device type, location, or time of access.
-
Evaluate Conditions: The system assesses conditions stipulated in the policy.
-
Grant/Deny Access: If it is met, access is granted.
Example:
According to an ABAC policy, an employee could be permitted to view a certain file if he or she belongs to the “HR” department, accesses it from the company device, and uses it within business hours.
Advantages of ABAC:
-
Granularity: Provides highly specific and dynamic access control.
-
Flexibility: Able to cope with complicated environments and a variety of situations.
-
Contextual Decisions: Evaluates, for example, location or device type, non-static information in the context of time.
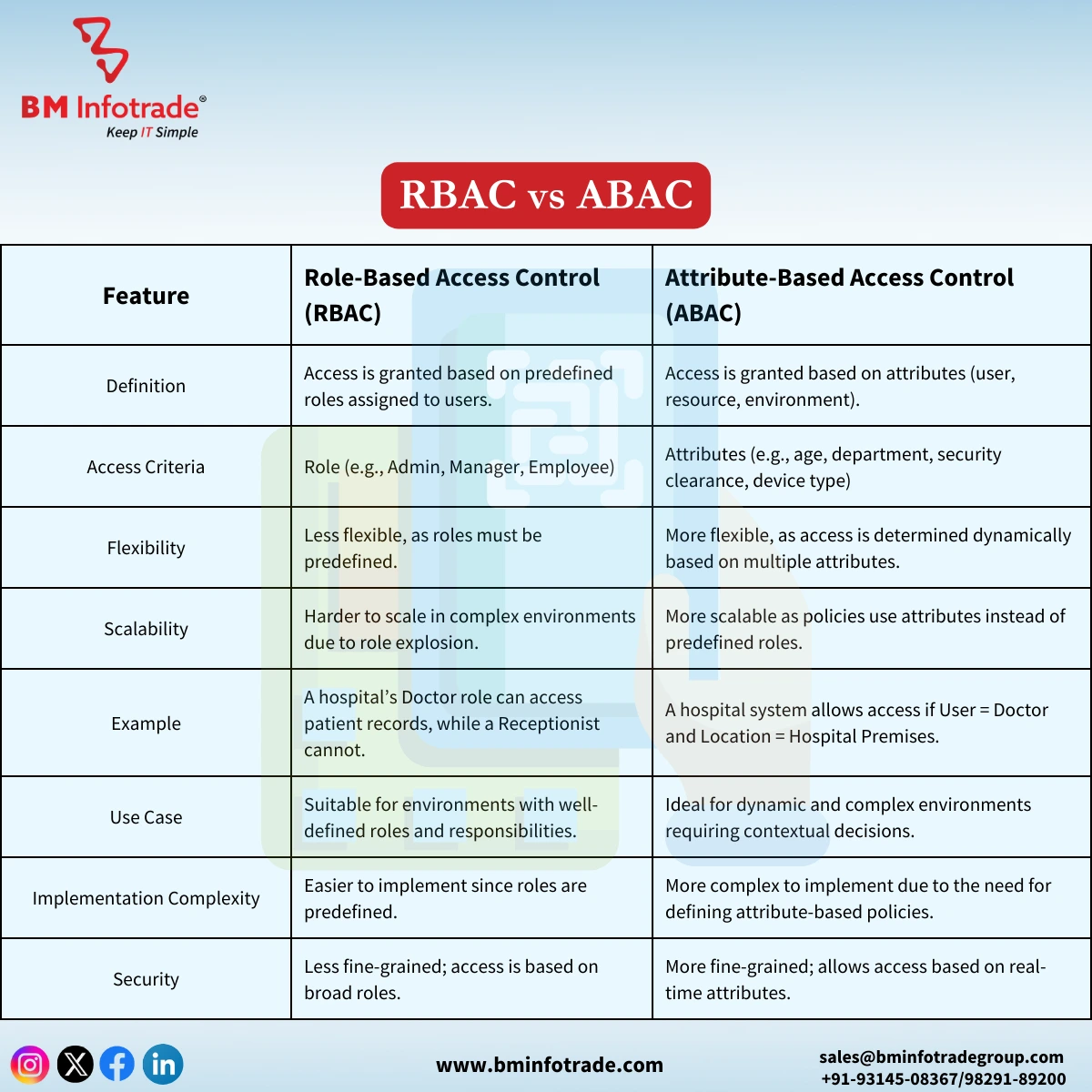
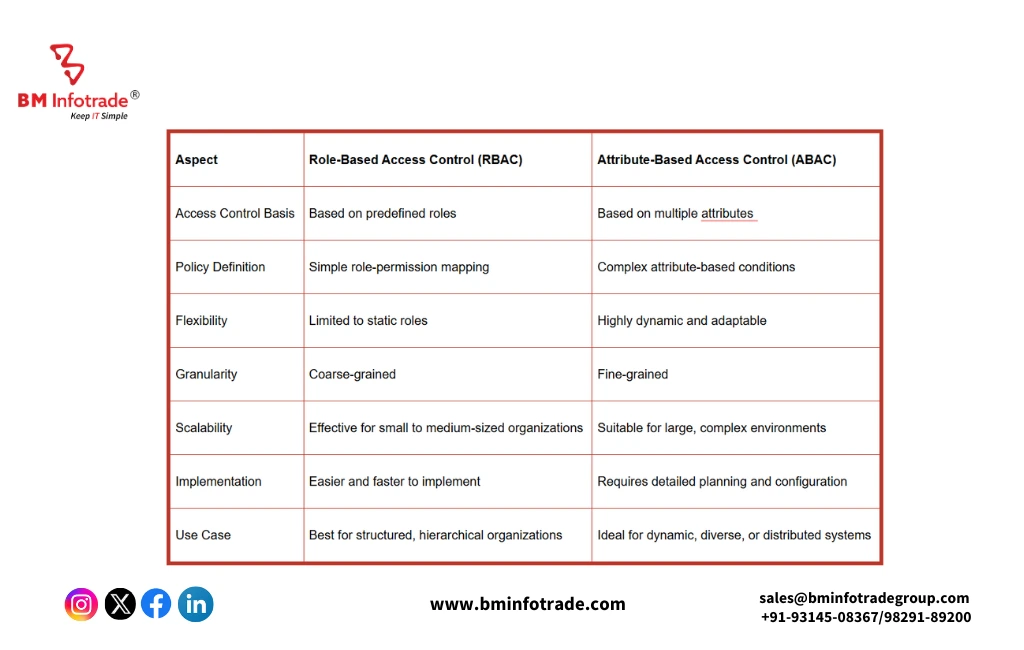
Key Differences Between RBAC and ABAC
When to Choose RBAC
RBAC is relevant for institutions that have well-defined job roles and uncomplicated access requirements. Here are selected situations where RBAC is more appropriate:
-
Structured Organizations: Hierarchical and assigned role types of organizations like that of government institutions or establishments even corporates tend to fall under the category of such organizations as well.
-
Simplified Management: Organizations of this type require management of policies without updating them at frequent intervals.
-
Compliance Requirements: Any industry where the job requirement coincides with the legal requirement such as healthcare or finance.
When to Choose ABAC
ABAC is most suitable for sites that need a fine granularity of access control on a conditional basis. The following are circumstances in which ABAC is supposed to be applied:
-
Complex Environments: Such as very big organizations which have employees working in different teams, resources and workflow processes.
-
Dynamic Access Needs: Organizations that require immediate permission around the clock based on user location and the time and type of devices.
-
Data Sensitivity: As in strategically sounding business sectors like banking and defence where the focus is on utilizing the theories of tiered space and context awareness.
Combining RBAC and ABAC
Often employers can profit from the two-sided strategy of RBAC’s ease and ABAC’s detail. For instance:
-
Everyone can assume standard roles: e.g.” IT admin”, or “support operator.”
-
Overlay ABAC policies to add context-based restrictions, such as allowing access only during working hours or from specific devices.
Such a balance of controllability and accuracy will result in a high-security level without an excessive amount of entanglement.
Benefits of Effective Access Control
1. Enhanced Security
Due to their restriction of access and use to authorized users, both RBAC and ABAC are capable of protecting sensitive data and resources.
2. Improved Compliance
With the help of access control models, organizations can comply with legal requirements like GDPR, HIPAA, or PCI DSS.
3. Operational Efficiency
Controlled usage focuses on the control of management effectiveness and reduces mistakes.
4. Reduced Insider Threats
Enabling people with the access they need in their day-to-day work reduces the chances of abuse, whether deliberate or unwitting.
Challenges in Implementing RBAC and ABAC
RBAC Challenges:
-
Difficulty in adjusting to transitioning roles with speed.
-
Risk of overassignment if there are no established boundaries.
ABAC Challenges:
-
Challenges in creating and enforcing attribute-oriented policy structure.
-
Higher initial cost and sustained management cost.
Future Trends in Access Control
As technology continues to advance in these unprecedented times, security, especially access control models, will evolve. The main trends include:
-
Artificial Intelligence In Access Determination: AI would improve the ABAC system architecture by knowing and anticipating how certain policies may function at a given moment.
-
Zero Trust Policy: Where verification needs to be always performed, the use of RBAC and ABAC models would be obligatory.
-
The Identity’s Range: Due to the diminished distances of the traditional networks, prevailing models will be those based on identities.
Read More:- Security system vs Proxy Server: Understanding Key Differences for Enhanced Network Security
Conclusion
Role-Based Access Control (RBAC) and Attribute-Based Access Control (ABAC) are literally security policies that govern user access to resources and information. While RBAC has scope for management because of the pre-defined roles, ABAC is more flexible to change and gives precise control in a more dynamic environment.
Determining whether to use RBAC or ABAC depends on the organization’s size and security needs. More often, an integrated approach of both systems works well without disrupting the operational efficiency.






Anshul Goyal
Group BDM at B M Infotrade | 11+ years Experience | Business Consultancy | Providing solutions in Cyber Security, Data Analytics, Cloud Computing, Digitization, Data and AI | IT Sales Leader